Phishing emails are deceptive messages sent by cybercriminals to trick recipients into revealing sensitive information or downloading malware. These emails usually look like they come from legitimate sources, such as banks, government agencies, or trusted companies, but their true intent is malicious.
Phishing emails are a widespread threat that targets individuals and organizations alike, and they can lead to significant financial and personal harm if successful. Understanding the common types of phishing emails is crucial for protecting yourself and your organization from these attacks. So, in this article, we’ll cover the basics of phishing and provide examples to help you stay vigilant.
What is phishing and how does it work?
Phishing is a type of cybercrime where scammers trick people into revealing sensitive information, such as credit card numbers or online banking passwords. Unlike hacking, which involves breaking into systems, phishing relies on deception: scammers disguise themselves as trustworthy entities through emails or text messages to trick victims into providing their data.
The term "phishing" originates from the idea of "fishing" for information, where cybercriminals cast out bait in the form of fake emails or messages, hoping someone will bite. These fraudulent communications often appear legitimate, making it easy for recipients to fall for the scam. A single click on a malicious link can lead to the loss of sensitive data, financial assets, and even access to important documents and images.
Organizations must stay vigilant against phishing attacks because they pose significant risks to their security and operations. A successful phishing attack can lead to data breaches, financial losses, and damage to a company's reputation. Compromised employee accounts can also be used to launch additional attacks, like spreading malware or stealing sensitive corporate information.
Types of phishing emails
Understanding these types of phishing emails is crucial for recognizing and mitigating potential threats. Let’s explore the most common types of phishing emails to help your organization protect itself against cybercriminal tactics:
Phishing: Phishing emails impersonate trusted entities like banks or service providers to deceive recipients into revealing sensitive information such as usernames and passwords. Clicking links in these emails leads to fake websites that mimic legitimate ones, tricking users into divulging confidential data.
Spear phishing: This targeted phishing variant focuses on specific individuals or organizations. Attackers often use personalized information to craft convincing messages. Spear phishing is commonly employed in ransomware attacks, where victims are lured into interacting with malicious links or attachments.
CEO fraud: In CEO fraud, cybercriminals impersonate high-profile individuals within an organization, such as CEOs, to trick employees into making financial transactions or divulging sensitive data. These emails often exploit authority and urgency to bypass usual scrutiny.
Vishing attacks: Vishing involves phishing over voice calls. Attackers impersonate legitimate entities, such as banks or tech support, to coerce victims into disclosing financial information or visiting fraudulent websites designed to steal login credentials.
SMiShing attacks: SMiShing uses text messages to deceive recipients into revealing personal information or visiting malicious websites. Attackers impersonate trusted entities like banks or tech companies, exploiting familiarity to lower victim suspicion.
Pharming: Pharming attacks manipulate DNS settings to redirect users from legitimate websites to fraudulent ones without their knowledge. By compromising DNS servers, attackers redirect traffic to fake sites where they can capture sensitive information entered by users.
Brand spoofing: Brand spoofing involves impersonating reputable companies or organizations to gain victims' trust. Attackers use recognizable logos and email templates to deceive recipients into providing sensitive information, exploiting familiarity with trusted brands.
Examples of phishing emails and how to identify them
Recognizing phishing emails is essential in safeguarding your organization’s data. By familiarizing yourself and your staff with common examples of phishing tactics and learning how to identify them, you can prevent falling victim to cybercriminals' deceptive schemes.
So, first, let’s review some of the typical characteristics of phishing emails:
Sender's identity. Check if the email is from a legitimate company or sender you recognize. Phishing emails often spoof familiar brands or use similar-looking email addresses to deceive recipients.
Unsolicited nature. Be cautious of emails that you did not expect or solicit. Phishing attempts often arrive unexpectedly, urging immediate action.
Requests for personal information. Phishing emails commonly ask for sensitive information like usernames, passwords, account numbers, or personal details. Legitimate companies typically do not request such information via email.
Offers or threats. Be wary of emails promising prizes, discounts, or threatening consequences unless immediate action is taken. These are common tactics to prompt hasty decisions.
Poor grammar and spelling. Phishing emails usually have grammatical errors, spelling mistakes, or awkward language. Legitimate communications from reputable companies are usually well-written and professional.
Suspicious links or attachments. Verify links by hovering over them (without clicking) to see the actual URL. Phishing emails may contain links to fake websites designed to steal your information. Similarly, avoid downloading attachments from unknown or suspicious sources.
Urgency or threats. Phishing emails often create a sense of urgency, threatening consequences if you do not act immediately. They may claim your account is compromised or suspended, pushing for quick responses.
Mismatched URLs. Verify that the URL in the email matches the legitimate website address of the supposed sender. Phishing emails often use URLs that resemble but slightly differ from the actual domain.
Strange email addresses. Check the sender's email address for typos or irregularities. Phishing emails may use email addresses that are similar to, but not exactly like, those of reputable companies.
Unusual requests or content. Be cautious of unexpected or unusual requests, especially those related to financial transactions or sensitive data. Verify these requests through official channels before taking action.
Now that you know the common traits of a phishing email, let’s go over some examples:
Capital One phishing email
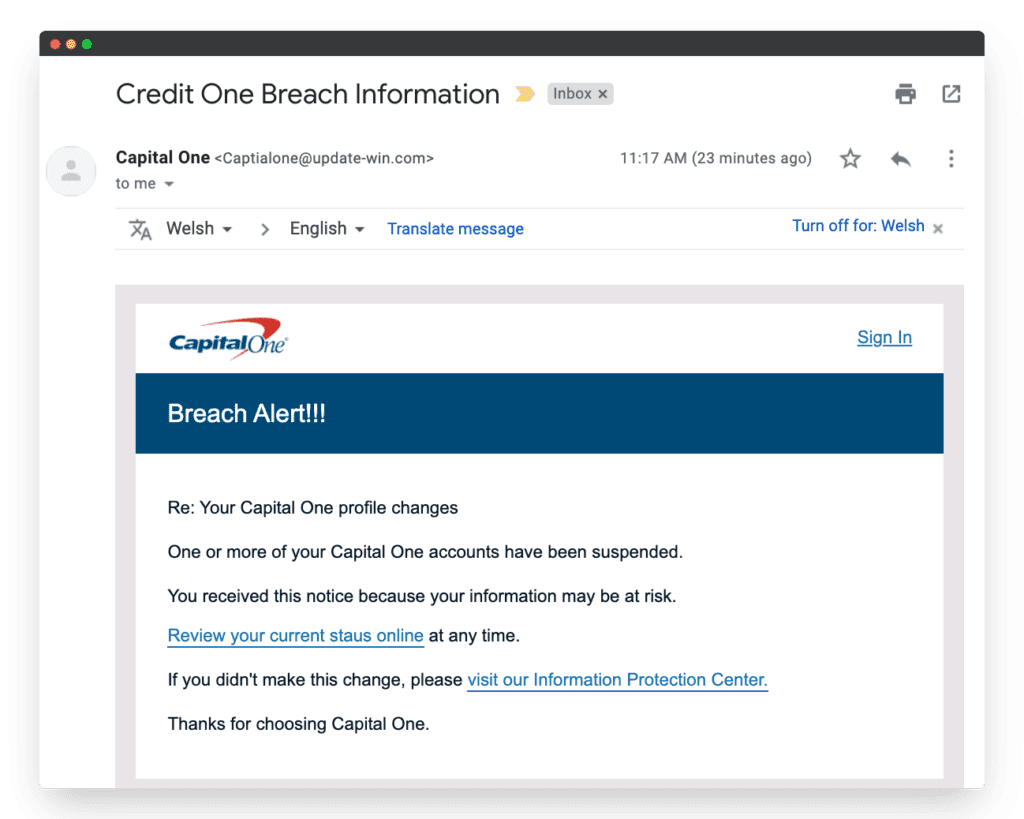
This is a very obvious example of a phishing email. First, the subject line says “Credit One” instead of “Capital One,” which should immediately alert the recipient. Then, the email address is misspelled and doesn’t seem legitimate. And the final tip-off is the “Breach Alert!!!” title, which is obviously a poor attempt at creating urgency.
Office 365 phishing email
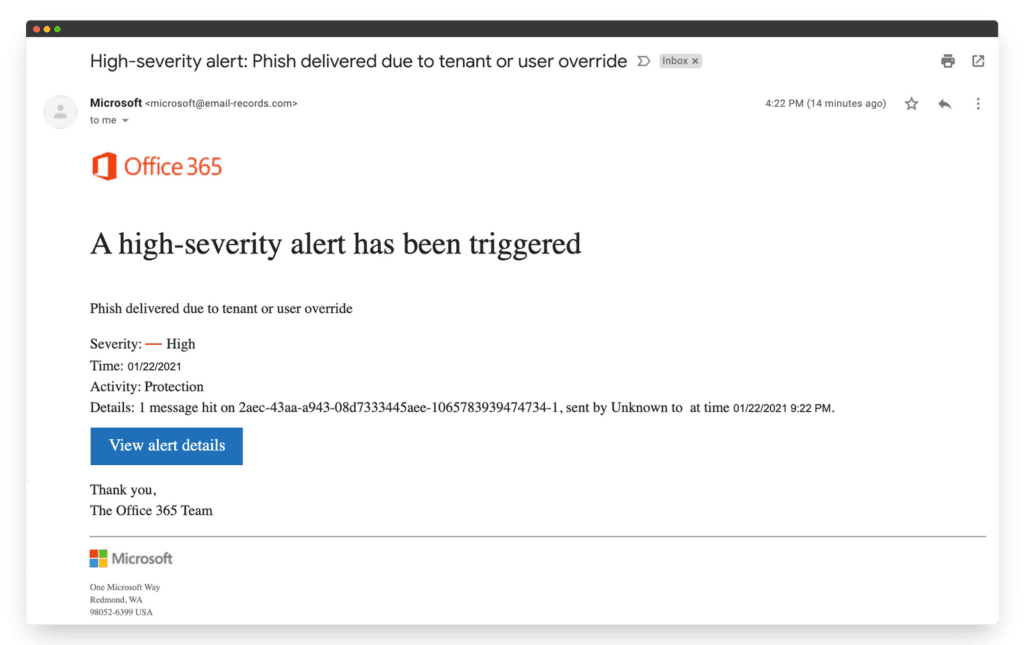
This email checks several phishing boxes: It includes a weird title and unusual grammar, and it attempts to create urgency in the reader. Also, although it appears to be from a trustworthy company, the email address of the sender doesn’t seem legitimate.
LinkedIn phishing email
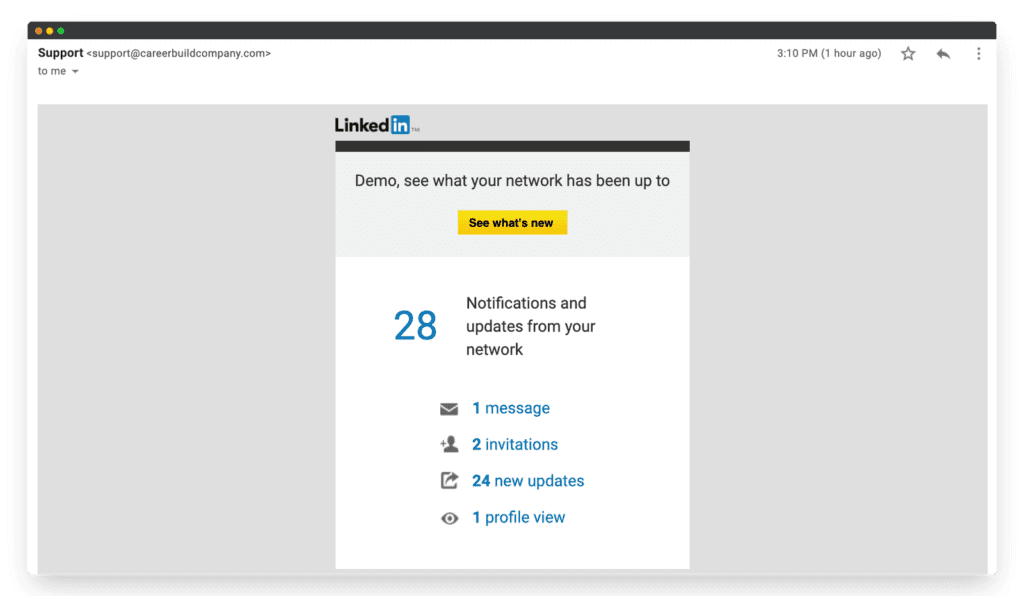
This one might be a bit more tricky to decipher. The grammar and design seem overall OK, and the email appears to be legitimate. But there’s one key element that gives it away: the sender’s email address is “support@careerbuildcompany.com.” That doesn’t seem like the type of email a legitimate company like LinkedIn would have, right?
Phishing emails can pose a serious threat to an organization’s security, operations, and reputation. By understanding the different types of phishing attacks and learning how to identify suspicious emails, you can significantly reduce the risk of falling victim to these scams, maintaining security and protecting your sensitive business information.
Summary
Phishing is a cybercrime where attackers use deceptive emails to trick recipients into revealing sensitive information or downloading malware. It's a major threat to both individuals and organizations, causing significant financial and personal harm.
Common types include spear phishing, CEO fraud, vishing, smishing, pharming, and brand spoofing. Each type uses different tactics to deceive victims and steal valuable information.
Look for red flags such as unsolicited requests for personal information, poor grammar, mismatched URLs, suspicious links or attachments, and emails creating a sense of urgency or threats.










