Why is cybersecurity important for small businesses? Small to medium businesses face the impact of cybersecurity incidents each day.
According to the Australian Cyber Security Centre (ACSC) Annual Cyber Threat Report 2021-2022, there were over 76,000 cybercrime reports. This equates to the ACSC receiving one report every 7 minutes compared to the previous fiscal year, which was every 8 minutes.
Anyone can be a potential target for a cyberattack, which means you need to be vigilant. We recognize that Australian small business owners do not have the time or resources to dedicate to cybersecurity. That is why you must act swiftly and implement simple measures to combat cybersecurity threats.
We explore the essential small business cybersecurity guide, including key cyber threats, financial impact, and how we can help.
Top Cyber Threats 2022
Australian small businesses are faced with all types of cyber threats. SMEs are mainly faced with a popular attack called ransomware. A ransomware attack occurs every 11 seconds, making it the number one threat to small businesses in 2022, according to Savvy. Here are the top cyber threats in 2022 that small to medium businesses face:
Ransomware
Ransomware is a type of malware (malicious software) designed to lock down your computer or organization’s sensitive files until a ransom is paid.
What can trigger ransomware?
Visiting unsafe or suspicious websites
Clicking on a website or email link from an unknown source
Inadequate email or network security
Phishing
Like social engineering, phishing is a fraudulent message designed to deceive employees into revealing confidential login credentials or sensitive information using electronic communication channels. Phishing attacks may target the following communication channels:
Below is an example of a phishing email:
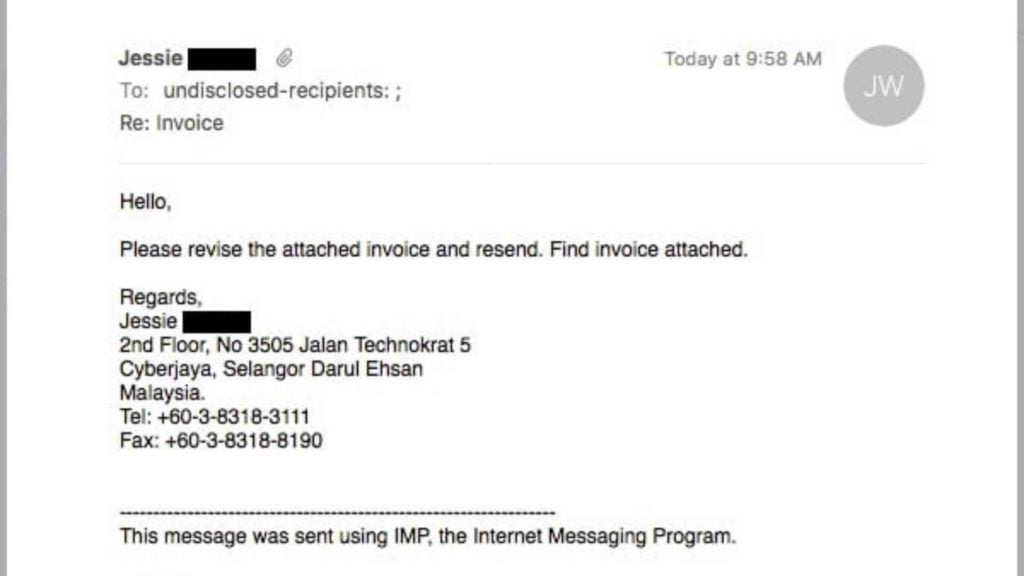
Source: Mailguard
Top phishing statistics in 2022:
Phishing text rose 28% in February 2022 and increased by 1,024% from April 2021
The Netherlands leads the list of targeted countries for phishing attacks in 2022, followed by Russia and Moldova
The most targeted age group in phishing attacks were individuals aged over sixty-five, amounting to a total loss of $6.6 million from October 2022
Malicious Software (Malware)
Malicious software, better known as malware, is any type of software that is specifically designed to make an organization’s computer system install unintended functions that aid cybercriminals in their malicious activities. Cybercriminals use increasingly sophisticated methods to infect targeted computer systems with malware, which can result in:
Damaged files
Data breaches
Fraud
Network control
Here are ten common types of malware:
Viruses: Computer viruses start by infecting a clean computer file, before spreading to other files in the computer system.
Worms: Worms are particularly virulent types of viruses that self-replicate, find new targets, and then execute on the next computer automatically.
Ransomware: Ransomware encrypts an organization’s data and computers to demand a ransom payment, usually in the form of cryptocurrency.
Trojans: A file that may seem legitimate but may contain hidden malicious code. When executed, the malicious code runs, which can result in a range of cyberattack vectors. For example, it can be used to install remote access backdoors to gain access to a network system or operating system.
Spyware: A type of malware designed to gather intelligence on an organization and gain access to its confidential data.
Adware: Adware can typically be installed unintentionally (hidden in fine print) that collects personal information about the user to send unsolicited advertisements.
Rootkits: Provides cybercriminals remote access to a targeted system, gaining full administrator rights over a computer system.
Keyloggers: Records all keys typed on a keyboard so that cybercriminals can obtain confidential authentication details such as passwords or credit card information.
Botnets: A network of computers infected by malware to bring down your organization’s network, spread malware, compromise data, or run tasks.
Scareware: A type of social engineering in which a victim is deceived into running malware out of fear.
Business Email Compromise
Business email compromise (BEC) attacks are targeted attacks that aim to deceive accounts payable staff into transferring funds to a fraudulent bank account controlled by the attacker.
According to the ACSC, there are three common deception tactics that cybercriminals use associated with a business email compromise, such as:
Invoice fraud: Compromising a vendor's email account to send spoofed invoices with the changed bank account details on those invoices
Email impersonation: Sending fake emails impersonating a senior executive (CEO or CFO) within a targeted organization
Mailbox compromise: Compromising a senior executive's email account to send fake payment instructions to accounts payable staff via email using an authentic mailbox

Phone Scams
Cybercriminals not only resort to emails when launching their attacks. Mobile devices are increasingly used, as they allow attackers to circumvent email security controls. Attackers achieve this by calling or texting people claiming to be from well-known businesses or government agencies like the ATO.
When identifying phone scams, there are five that are commonly used:
If you receive a phone call or text that sounds too good to be true, it may be an attacker attempting a phone scam. Other red flags include an individual who is threatening you, asking to gain access to your computer for any reason, or an unknown individual who has your personal details. If the phone call or text seems suspicious, rule number one is to never click on an unknown link and to never give out your personal details without verifying. Sophisticated attackers are always coming up with new ways to gain access to your bank account details, like your credit card information, or take control to commit fraudulent activities.
The Consequences of a Cybersecurity Breach
The costs of cybercrime extend far beyond any amount that has been defrauded.
The impact of a cybersecurity breach is far too substantial for most small businesses to recover from. For instance, the average reported loss by a small business was $8,899, while medium businesses lost an average of $33,442 to cybercrime, according to mybusiness. Australian business owners should recognize the direct and indirect costs that they could potentially face if security controls are not in place.
The Cost of Business Disruption
One of the most significant costs that must be factored into cybercrime is business disruption. This is also among the hardest to quantify in advance, as each case of cybercrime varies in impact and intensity. Costs may include:
Rebuilding operational capabilities such as repairs to computer systems and equipment
Stolen funds
Theft of intellectual property
Theft of personal and financial data
Impacted Cash Flow & Financial Loss
When a small business is impacted by cybercrime, the resulting losses can have a detrimental impact on cash flow. Other than losing bank accounts and loss of revenue, businesses may incur extra costs after a cybersecurity incident, such as increased insurance premiums.
Reputational Damages
Small businesses that are impacted by a cybersecurity incident can have long-lasting effects on the business and reputation. Reputational damages involve:
Loss of customer trust
Loss of partner trust
How Can Eftsure Help?
The time is now.
The most effective way to protect your business is to strengthen your cybersecurity controls like multi-factor authentication and security software that facilitates continuous oversight and compliance monitoring.
By integrating Eftsure, you can safeguard your organization’s financial assets from cybercrime with our fraud tech solution. Our solution is designed to alert in real-time each outgoing payment if there is a mismatch with a BSB or account number when processing an EFT payment, allowing you to investigate any suspicious activity during the payment process.
For more information, download our cybersecurity guide for CFOs 2022 that can be used as the foundation of cybersecurity for small businesses. We explore a comprehensive guide on how to become involved in every stage of your organization’s internal cybersecurity conversations, planning, and execution to mitigate a cyberattack.
Contact Eftsure today for a full demonstration of how we can protect your business in cybersecurity.









