Speak to friends, family, or colleagues, and there is a fair chance one of them will have been the victim of identity theft.
Typically, criminals seek to impersonate an individual to either obtain bank loans or credit cards in the victim’s name. This enables the fraudster to purchase valuable goods, which they can subsequently on-sell. Meanwhile, the victim is left with a hefty bill.
It is one of the reasons many individuals now subscribe to credit reporting services, so they can be alerted whenever an application for a loan or credit card is submitted in their name.
Whilst there is widespread awareness of the risks of personal identity theft, far fewer people have stopped to consider the rise of business identity theft.
What is Business Identity Theft?
Business identity theft is where a fraudster seeks to impersonate a business, or specific individuals within a business, in order to obtain financial gain. Whilst the fraudster may seek to obtain loans or credit cards in the name of the business, there are a range of other attack vectors associated with business identity theft.
Most notably, a fraudster may seek to impersonate a business’s CEO or CFO to issue realistic instructions, usually via a compromised email account, to the accounts payable team to make electronic funds transfer payments to the criminal’s own bank account. Businesses that process large volumes of invoices are particularly targeted in this type of scam.
According to the Australian Institute of Criminology (AIC), instances of serious identity theft are increasing at an alarming rate. The AIC defines an instance of identity theft as “serious” if it meets one of the following criteria:
A high level of financial loss (over $1.5 million).
A high degree of sophistication in the planning and execution of the offence.
An offence committed by professionals (such as solicitors, accountants, financial planners, or mortgage brokers) who breach clients’ trust.
According to this definition, the AIC estimates that serious identity theft cost Australia over $423 million in the financial year 2018-2019.
The Australian Federal Police (AFP) is at the forefront of national attempts to prevent the spread of this type of crime. It recognises that identity crime need not involve impersonating individuals but rather may involve impersonating corporate entities. It defines identity crime as a generic term to describe activities in which a perpetrator uses either a fabricated identity, a manipulated identity, or a stolen/assumed identity to facilitate a crime.
The AFP has identified three key categories of identity crime:
Identity fabrication – the attempt to create a fictitious identity.
Identity manipulation – the attempt to alter one's own identity.
Identity theft – the attempt to steal or assume a pre-existing identity (or significant part thereof), with or without consent.
Types of Business Identity Theft
Financial Fraud
The first action fraudsters take is to attempt to defraud your organisation. This is the most common form of identity theft, including:
Obtaining a new line of credit, loans, or credit cards in the name of the business
Transferring business funds from your bank accounts to a fraudulent account
Opening a new bank account under the business's name
Withdrawals & purchases involving luxurious items and/or selling them to make quick profits
The goal of the fraudster is to exploit the business for the criminal's financial gain. This is reinforced when viewing identity theft statistics. For example, according to Scamwatch, identity theft exceeded $2.2 million in August 2022 alone.
Fraudulent Tax Returns
Another common form of identity theft is fraudsters committing fraudulent tax returns to claim a refund, also known as 'refund fraud'. Refund fraud can include:
Providing spoofed information and documents, such as invoices and receipts
Lodging fraudulent returns using fake or stolen identities
Lodging fraudulent GST claims through a fraudulent business registration
Much like financial fraud, fraudulent tax returns aim to take advantage of the business's finances, to generate a larger refund compared to an individual's income tax return.
The ATO warns that identity thieves may target unsuspecting small businesses to steal personal information that can be used to commit other cybercrimes. Prevent financial fraud in your accounts payable department today by following our guide.
Website Defacement
Website defacement is a form of online digital vandalism. This typically involves a fraudster gaining access to a business's website and manipulating its appearance such as the company's logo, content, or web pages in their entirety.
The individual or group behind these types of business identity crimes are usually hacktivists driven by social, political, or religious motivations. One notable attack was in 2020 when two Iranians defaced at least 51 US government websites, displaying a "hacked by Iranian hacker" message on the home page.
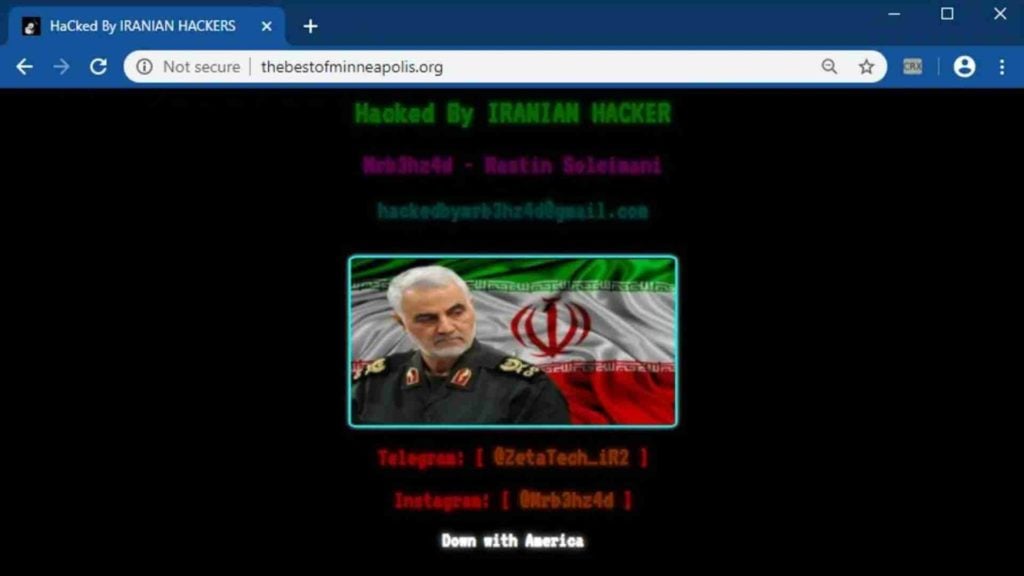
Source: Znet
Trademark Ransom
Trademark ransom occurs when a fraudster registers a business name or logo as an official trademark in an effort to demand a ransom. Fraudsters are always planning their next attack. Information about your business is publicly available on the web and on the Australian Securities & Investments Commission (ASIC) website.
Examples of Business Identity Theft Scams
Identity thieves are always on the lookout for new ways to steal your hard-earned money. They might hack into a small business's website or contact database, looking up information about you that they could then use in an attempt at fraud - like changing their name and sending out bills under yours!
Whether an organisation's identity is being fabricated, manipulated, or stolen, the effects can be devastating. These can include significant financial losses and impacted cash flow, damaged reputation, and long-term business disruption.
CFOs must familiarise themselves with the type of attacks that can occur, we have listed some business scams that CFOs should watch out for:
Fake Invoices
Fake invoices are a type of business identity theft where criminals pose as legitimate businesses to trick victims into paying phoney invoices. This scam is usually carried out by email, but it can also happen on mobile devices or through the mail.
Fake invoices can be very convincing, so it's important to be aware of the signs of this type of fraud. For example, you should be suspicious if you receive an invoice for an unexpectedly large amount of money, or if the invoice is from a business you've never dealt with before.
If you're unsure whether an invoice is legitimate, always contact the company directly to confirm before making any payments. By being vigilant, you can help protect yourself and your business from fake invoices and other types of scams.
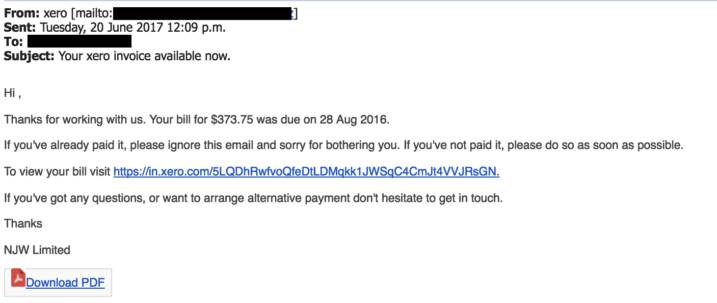
Source: usecure
Phishing
Another common business scam is phishing. In a phishing scam, a fraudster will pose as a legitimate company or individual to obtain sensitive information from you or your employees like bank statements, credit card statements, or invoices.
They may do this by sending an email or text message that appears to be from a reputable source but contains a link that leads to a fake website. Once on the fake website, victims are typically prompted to enter personal or financial information, which is then used by the fraudster for criminal purposes.
To protect yourself and your business from phishing scams, never click on links in emails or text messages unless you are certain that they are legitimate. If you are unsure, you can always contact the company.
Money Mule
Money mules are individuals who act as intermediaries in business identity theft schemes. Typically, a money mule will be recruited through some type of business opportunity or scam, such as a fake work-from-home offer or an advanced fee fraud.
Once the individual has been recruited, their personal details are often used to open fraudulent business accounts and obtain business loans, credit cards, and other lines of credit that the mule then passes on to the criminal behind the scam.
While these individuals do not benefit directly from the fraud, they are still held liable for any financial losses incurred because of their participation. Because of this, it is important to avoid any business opportunities that seem too good to be true and to report any suspected identity theft scams immediately.
Fake Social Media Accounts
The objective of social media identity theft is to impersonate the victim's business by creating a fake social media profile. Typically, the motivation behind this act is to scam clients of the targeted business, or to drive customers away potentially causing business disruption.
By posing as a legitimate supplier or business on social media, fraudsters can use social engineering tactics to phish out more information on their target. They may attempt to look for information like addresses, email addresses, bank accounts, invoices, company information, and more.
Fake Websites
Fraudsters often impersonate their victims by setting up a fake website to impersonate their business with a similar URL. Fraudulent sites are used to gain as much information about you and your business information.
They achieve this malicious act by leading you to fill out various forms involving names, addresses, emails, and possibly financial information like credit card numbers, BSB, and account numbers. A fake website can surface in spoofed emails, fake social media accounts, or be listed in search engines like Google to commit identity theft.
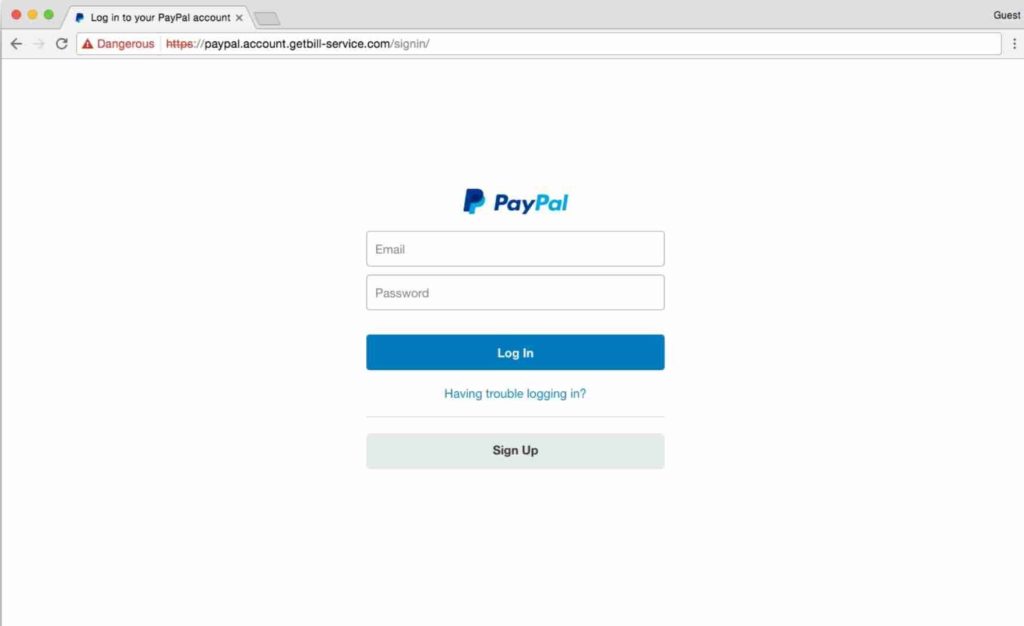
Source: hashedout
Phone Scams
Lastly, after a fraudster has exhausted all options, they may resort to phone scams by impersonating a bank, credit report agency, ATO, or any form of entity in hopes of stealing your information.
If you receive this kind of call, make sure to never provide any information over the phone without validation of authenticity. If you suspect a fake call, hang up immediately. Most of the time, banks and government entities communicate through mail or possibly through email. If you are unsure, look up the caller's phone number on Google and confirm.
Impact of Identity Theft on Businesses
Whether a business’s identity is being fabricated, manipulated, or outright stolen, the effects can be devastating for shareholders, employees, and customers. It’s a serious and growing risk that every organisation, big or small, should be taking steps to prevent.
For fraudsters, the potential returns from engaging in business identity theft are far higher than individual identity theft. When a business is confronted with fraudulent loans or credit cards being taken out in its name, it faces an arduous task to clean up the mess. Whilst it may be possible to have the issuing bank void the losses, the problem is more complex in the case where funds have been wired to a criminal’s bank account. Usually, these funds are irretrievable.
Beyond the direct costs of such fraud, businesses will likely face a number of other significant challenges, including:
Impacted cash-flow
When a business has its identity stolen, the resulting lost income can make keeping up with bill payments a significant challenge.
Consequently, there may be delays in the business’s capacity to make payments to suppliers, keep up with wage bills, not to mention the possibility of defaulting on loan repayments. The business may be forced into a position where it has to rapidly cut costs.
Impacted credit score
We know fraudsters regularly use stolen identities to apply for loans or credit cards. This could negatively impact a business’s credit score, making it harder to obtain financing in the future.
This risk is particularly high for sole traders and other small businesses, where the owner is personally guaranteeing lines of credit. It could result in the owner’s personal credit score also being negatively impacted.
Impacted brand reputation
When a business is a victim of identity theft, it can have long-lasting effects on the brand. Customers, suppliers, and other commercial partners may perceive that the business is insecure.
This may lead to questions around whether the business’s information security controls can be fully trusted. The result could be lost market share and revenue.
How Can I Prevent Business Identity Theft?
Whilst businesses should seek to prevent all instances of business identity theft, in the event of fraudulently obtained loans or credit cards, banks will typically void these.
However, in instances where the business identity theft was used to deceive your accounts department into making electronic funds transfer payments to the criminal’s bank account, this can result in irreversible financial losses.
That is why you need a technical solution in place that can warn the accounts payable team that it may be transferring funds to an illegitimate bank account.
Eftsure’s unique software integrates seamlessly with your online banking and ERP platforms to highlight suspicious outbound payments before they are sent. This gives your accounts team the opportunity to verify any funds before they click “send”.
We further explore how to prevent identity theft by exploring 7 steps with easy-to-implement strategies to get started.
What To Do If You Fall Victim of Identity Theft
If you suspect that your organisation is a target of business identity theft, you should report this to the Australian Competition and Consumer Commission’s Scamwatch.
Scamwatch provides information to consumers and small businesses about how to recognise, avoid, and report scams. By reporting any suspected scams, you’ll be helping the authorities understand the scale of the threat, allowing them to raise awareness so others can avoid being victims.
If you're uncertain how to react to corporate identity theft, or if you have fallen victim to identity theft, we have 8 essential steps you can take to respond immediately.
Key Takeaway
Business identity theft is a serious problem that can have devastating consequences for a company.
As a CFO, it's important to be aware of the risks and take steps to protect your business. Business identity theft occurs when criminals use a business's information to open new accounts, obtain loans, or make purchases.
This can damage the business's credit rating, cost the business money, and lead to investigations by law enforcement. To protect your business, be sure to carefully monitor your accounts and report any suspicious activity immediately.
You should also have strong internal controls in place to prevent unauthorized access to your business's information.
Contact Eftsure for further information on how this unique Australian platform can help you avoid becoming another business identity theft victim.