In a world increasingly dependent on digital platforms, you may wonder how likely it is that you'll fall victim to a scam. Scams aimed at individuals and businesses have become more sophisticated and their consequences more profound. However, the good news is that your risk of becoming a victim can be minimized with strong cybersecurity hygiene.
By adhering to a few crucial practices, you can stay one step ahead of potential threats and protect your personal and financial information. Tools like Eftsure's Breach Checker can also help you take proactive measures in the event your email address has been involved in a data breach.
With the above in mind, here are some questions that define cybersecurity hygiene and how you can adopt it in practice.
1 – Have you changed your passwords recently?
Passwords are your first and most basic defense. But the effectiveness of this defense depends on the password you choose and whether you use it elsewhere.
A strong, unique password is essential to keeping cybercriminals at bay. Nevertheless, many still use weak passwords or recycle the same password across multiple accounts.
If you are prone to these habits, understand that it is giving hackers an easy entry point.
Conventional wisdom once said that passwords should be updated every three months or so, but with two-factor authentication (2FA) in place, they should only be changed if there is reason to believe the account has been compromised.
Nevertheless, some best practices for passwords include:
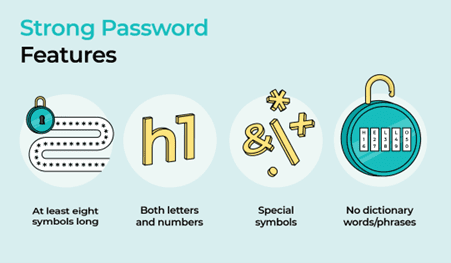
Use unique passwords – this means every account should have a different password.
Length and composition matter – so aim for at least 8 characters (but preferably 12-16) comprised of lower and uppercase letters, numbers, and symbols.
Avoid personal information – don’t use easily accessible details like birthdays, pet names, or the names of family members.
Avoid using words or phrases that can be found in a dictionary.
For managing multiple strong passwords, consider using a password manager to securely store and generate complex passwords.
2 – Are you using two-factor authentication?
If you’re not using two-factor authentication (2FA), your strategy to protect yourself from bad actors is incomplete.
Even the strongest password can be compromised. However, 2FA adds an additional layer of security that requires a second form of verification such as a code sent to your phone or email.
This ensures that even if someone has access to your password, they must still provide a secondary authentication factor to access your account.
Most major services such as banking apps, email providers, and social media platforms offer 2FA.
The specific factors in a 2FA process vary, but in short, they are based on:
Knowledge – something the account holder knows. For example, the answer to a security question.
Possession – something the account holder owns to receive additional credentials, such as a phone or security token.
Inheritance – something the account holder has. These are usually biometric credentials like a retina scan or fingerprint.
3 – Can you recognize a phishing attack?
Phishing attacks are among the most common ways scammers obtain access to personal information.
These attacks tend to present themselves as emails or texts that appear to be from authentic sources, but they’re designed to trick you into revealing sensitive information like your bank account details, username, and password.
To recognize a phishing attack, be on the lookout for:
Emails from unknown addresses, or addresses that have been altered to impersonate a reputable company or person (such as “@c0mmbank.com.au instead of “@commbank.com.au”).
Urgent messages asking for personal information or immediate action.
Attachments or links that are unexpected or seem suspicious.
Unusual requests for personal information – legitimate companies rarely (if ever) ask for sensitive information via email or text.
4 – Is your software up to date?
For many businesses, outdated software is the most significant vulnerability in their cybersecurity armor. In fact, up to 60% of data breaches are caused by known software vulnerabilities that have not been patched.
Scammers and hackers frequently exploit known weaknesses in older software versions and use them to secure unauthorized access to systems. From there, ransomware and malware can severely disrupt operations.
Ensure that all your devices – from laptops to smartphones – are running the latest versions of their respective operating systems. It is also important to make sure that web browsers, extensions, and antivirus software are up to date.
To that end, enable automatic updates where possible to ensure that software is always patched against the latest security threats.
5 – Do you back up your data regularly?
Backing up your data is an essential part of cybersecurity hygiene, but it is often a task that is put off for another day.
Irrespective of whether your data contains personal files, photos, or work documents, a secure backup ensures that you won’t lose everything in the event a system is compromised or held ransom in a ransomware attack.
Back up your data to an external hard drive or cloud-based storage service with secure encryption, and update your backups frequently so that more recent files are safe and secure.
6 – Do you take steps to ensure your privacy?
At the most fundamental level, privacy means you don’t post potentially compromising information in public (such as on social media). This includes your home address, phone number, and other sensitive information a fraudster could use to impersonate you or steal your identity.
Secure networks are also an important aspect of online privacy – particularly when accessing or entering sensitive data such as bank account details, emails, and work files.
While no doubt convenient, remember that public Wi-Fi networks are unsecured. Hackers can easily intercept your data and access login credentials, personal information, and even your private communications. These data are often stolen as part of a man-in-the-middle (MITM) attack.
Virtual private networks (VPNs) are useful if you must use public networks. Otherwise, ensure that the websites you frequent are HTTPS-encrypted and always enable firewalls on whatever device you’re using.
Stay vigilant and stay secure
While there are no guarantees, these cybersecurity hygiene best practices can dramatically reduce your risk of falling victim to online scams.
Each question you can answer in the affirmative makes it more difficult for cybercriminals to access your personal data. But if you suspect your email has been compromised, use Eftsure's Breach Checker tool to verify whether you need to take corrective action and protect your data.








