In the accounting world, accuracy and compliance with financial regulations are of utmost importance. To maintain financial integrity, financial leaders often rely on controls like segregation of duties (SoD).
Before implementing SoD in your workplace, it’s important to understand its significance for accounts payable (AP) teams and how it minimizes fraud and errors.
Once you’re familiar with the benefits that SoD offers for your organization, the next essential step is implementing it within your AP function. This involves assigning distinct responsibilities, establishing strong access controls, setting approvals, and tracking account logins.
In this article, we explore how you can implement SoD to stay compliant and mitigate the risk of fraud and error.
Empowering SoD to Combat Internal Fraud
In today's fiercely competitive cyber threat landscape, fraud and cybercrime can come from any vertical.
Whether it's a sophisticated cybercriminal launching an external attack on your computer networks or a disgruntled insider exploiting system access during non-working hours, the importance of SoD as a formidable financial control cannot be overstated.
Recent trends emphasize the rise in malicious threats instigated by internal stakeholders, such as disgruntled employees or suppliers. According to Proofpoint, insider threats have increased in both frequency and cost over the past two years. For example, 56% of incidents experienced by organizations represented in this research were due to negligence, and the average annual cost to remediate the incident was $6.6 million.
Moreover, senior executives aren't just grappling with malicious insiders but also contending with other insider threat categories, including negligent insiders and compromised insiders, as outlined by IBM.
The question then arises: What are organizations doing to thwart the menace of internal fraud?
Enter the solution - segregation of duties, a tailored financial control that empowers organizations to assert authority over their unique structure while meticulously dictating who gains access to sensitive data.
Segregation of duties is designed to prevent any single individual from having too much control or access within a critical process or system. By separating key duties and responsibilities, it becomes more challenging for a single person to engage in fraudulent activities without detection.
Real-world Challenges of SoD
The challenge that comes with SoD in the real world is that it requires senior executives to continuously monitor roles and responsibilities. And complex processes that make it difficult to establish clear boundaries between said roles.
Not to mention for smaller businesses, the challenges with the separation of duties are greater. A business that only has one or two network administrators may simply not be able to divide the responsibility or role.
To navigate these challenges while upholding effective SoD, consider laying the groundwork with these key practices:
Start with a risk assessment: Commence with a comprehensive risk assessment, pinpointing critical processes and high-risk areas susceptible to fraud or errors.
Prioritize key processes: Given the limited resources, prioritize the implementation of SoD in processes that generate the most impact on financial integrity and compliance.
Draft tailored SoD policies: Develop and tailor SoD policies that harmonize with the distinct needs and scale of your business, steering clear of a one-size-fits-all approach.
For a more comprehensive overview of evaluating internal controls, such as SoD, consider undertaking pressure testing. Keep in mind that SoD is a continual endeavor, and when finely tuned to suit your unique business needs, it stands as a formidable defense against the threats posed by internal fraud and cybercrime.
How to Implement Segregation of Duties in Your AP Function
For businesses using Eftsure, the main objective is to ensure mitigation of fraud and error, without compromising productivity or employee autonomy. An effective approach to mitigate these risks is to implement SoD tailored to your organization. As a basis, we recommend implementing the following:
Identifying key processes and roles
Defining clear roles and responsibilities
Establishing strong access controls (access restriction)
Creating user profiles
Tracking login activity
1) Identifying Key Processes and Roles
The first step to SoD implementation is to assess the current state of your organization. This means identifying your existing key processes and roles within your accounting operations. This will allow you to determine which tasks need to be segregated and who is responsible for those tasks. For example, you may identify these critical roles that need to be segregated.
Invoice processing
Payment approvals
Payroll management
Bank reconciliations
Financial reporting
Supplier management
Auditor/Monitor
Payments review
Approver
The number of separate key processes and roles an organization should have for SoD depends on its size, complexity, and industry. The objective is to ensure that no single individual has control over every aspect of a critical role or process. In addition, the more intricate the organization's financial processes, the more complex SoD becomes.
Once you identify each process and role involved, it's time to determine which individuals are currently responsible for these tasks.
2) Defining Clear Roles and Responsibilities
Once key processes and roles have been identified, you need to clearly define clear roles for each employee and assign specific responsibilities to each role. This will prevent conflicts of interest, help detect and deter fraud, identify errors, and establish accountability. By assigning specific responsibilities to different individuals, you significantly reduce the likelihood of error or fraudulent activity.
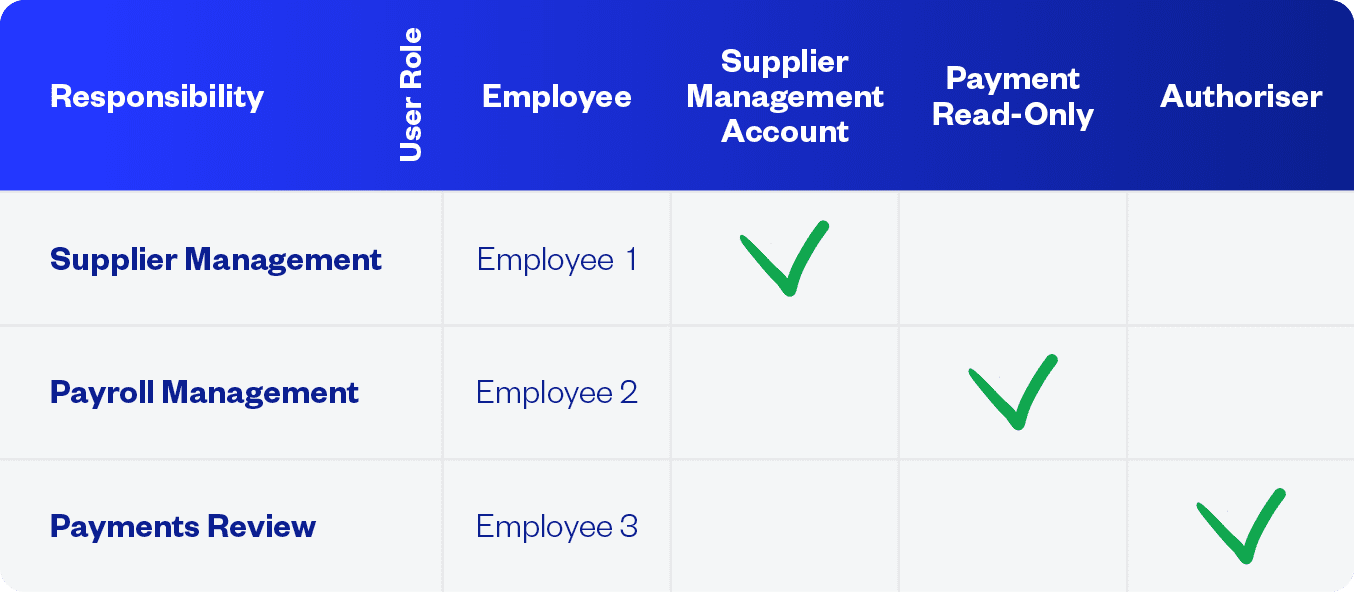
If your organization has a large accounting department, it might be worth considering creating a segregation of duties matrix to effectively manage a diverse range of roles and responsibilities. You can start by drafting an Excel spreadsheet, where roles are listed in the top row and corresponding responsibilities are detailed in the left-hand column.
After the columns are created, you can allocate employees to a specific role and responsibility. You can then appoint a tick or green box in the SoD matrix to indicate tasks that don’t conflict with the principles of segregation of duties. One example might be Employee A, who is authorized to verify and input invoices to the payment or accounting system. Whereas Employee B will have a different responsibility and will have a red box to indicate tasks where a SoD conflict exists.
The objective of the matrix is to eliminate any ambiguity regarding each user’s designated role and responsibility, while also demonstrating a clear overview of each AP clerk’s role and where they may be restricted. This ensures that each task is allocated to the appropriate personnel and that equitable distribution of critical tasks throughout the entire organization.
Here’s one example below:
3) Establishing Strong Access Controls (Restricting Access)
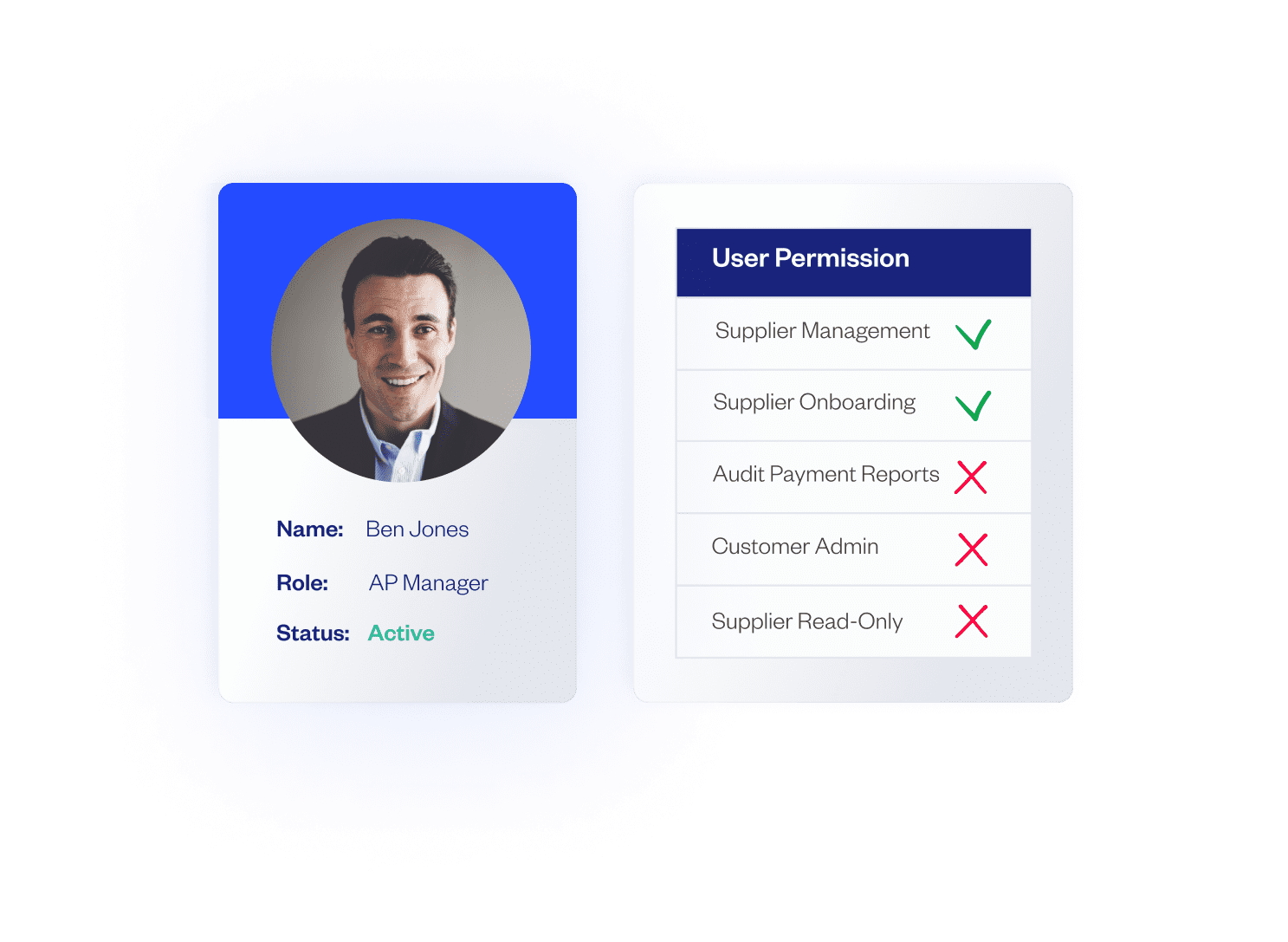
After you allocate the appropriate personnel to each segregated task, you can move on to implementing stringent access controls to regulate and manage user access. This means that finance professionals can assign role-based permissions, where each AP clerk is granted access only to the specific tools, applications, and data relevant to their responsibility.
For instance, an employee responsible for processing invoices might have access to view invoices, financial reports, and supplier information, but they may not have access to approve invoices or modify sensitive data. To add an extra layer of security, organizations can add multi-factor authentication (MFA) as a requirement for certain actions.
The main objective in step three is to restrict unauthorized access to sensitive data. By incorporating strong access controls, you enforce strict segregation of duties. As a result, you control which employees have access to certain functionality – that is, the only functionality they need to carry out their tasks.
With a solution like Eftsure, you can grant users access to specific resources and functions required for their job roles, while restricting the resources and functions they don’t need. For example, an employee responsible for entering invoices can be restricted from seeing if an invoice has been approved or paid.
By limiting access, the organization can minimize:
Risk of intentional or unintentional misuse of privileges
Unauthorized access to sensitive financial data
Potential for fraudulent activities
Internal threats and unauthorized manipulations
4) Creating User Profiles
By combining user profiles with stringent controls, you add another layer of security.
User profiles can be created on the application or network system that holds sensitive data. This allows admins to add a set of permissions granted on a single application or system. Profiles are related to roles, which means that the roles you’ve assigned in your SoD matrix will reflect the perspective changes on applications and systems.
Creating user profiles removes the headache of managing the SoD matrix manually. A profile ensures that specific individuals only have access to certain amounts of information more efficiently. It’s also easier to identify users who have operation capabilities outside of the operations required by their role, reducing potential security vulnerabilities.
The difficult aspect of creating user profiles is that all employee information must be updated at all times. This means where employees have been promoted or have left the company, their user profiles must be updated accordingly.
Tighten Up Your Segregation of Duties with Eftsure
Maximizing your security measures through the implementation of segregation of duties is imperative. It's important to recognize that proactively combating cybercrime will help minimize the risk of unauthorized access to critical functions and sensitive data. During the 2021-22 financial year, more than two in ten businesses experienced a cybersecurity attack.
Unfortunately, most businesses don't prioritize their cybersecurity posture until it's too late.
By incorporating Eftsure into your accounting function, you not only introduce a powerful way to streamline user access but also boost your ability to defend against various types of cybercrime.
Eftsure's solution eliminates the headache of manual segregation of duties management. Instead, we automate some of the processes. Through secure controls such as user permission management, defining user roles, and simplifying financial investigation processes, you can thwart potential fraud attempts without sacrificing productivity or efficiency. This creates robust segregation of duties and safeguards sensitive information.