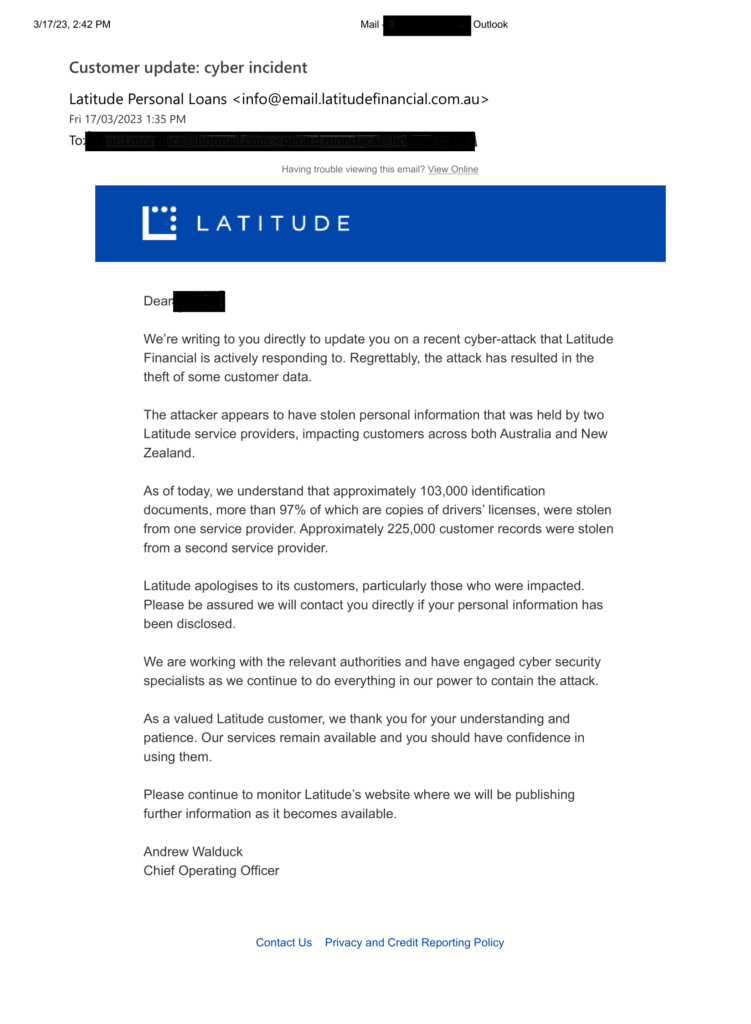
Update on 28 March, 2023: Since this article’s publication, Latitude Financial has continued to disclose impacts as their forensic investigations continue. At the time of this update, that includes an estimated 7.9 million Australian and New Zealand driver’s licence numbers – around 40% of which were provided to Latitude within the last 10 years – and 53,000 passport numbers stolen.
Around 6.1 million customer records were also accessed, “including some but not all of the following personal information: name, address, telephone, date of birth.”
For the latest updates, subscribe to the Eftsure newsletter.
Consumer financial services provider Latitude Financial is the latest major Australian company to reveal a cyberattack and customer data breach, with around 225,000 customers impacted and nearly 100,000 copies of driver’s licences exposed.
On 17 March, the company entered a trading halt on the Australian Securities Exchange, issuing a statement saying it had detected “unusual activity” on its systems and that it appeared to be a “sophisticated and malicious cyberattack.”
Latitude claims that it has traced the breach to one of its vendors, which – according to the ABC – may have been a back-end infrastructure provider. Through this vendor, the attacker allegedly accessed Latitude employee login credentials and was able to steal personal information held by other vendors.
The business says that it’s currently working with the Australian Cyber Security Centre (ACSC) and has notified law enforcement agencies. It has also communicated directly with affected customers.
Latitude Financial offers a variety of banking services including loans, insurance and credit cards, as well as consumer financial services for major retailers like JB Hi-Fi, Harvey Norman and Apple. It’s one of the first financial services providers in Australia to suffer a data breach of this scale – a significant development because of the significant amount of personal information required to access loans and other banking services.
What are the knock-on effects for AP professionals?
When malicious actors access sensitive data, it’s not just the impacted customers who are at risk. Plus, Latitude’s claims illustrate that, often, your security is only as strong as the security of your suppliers and partner organisations.
Accounts Payable (AP) and finance teams should be on high alert since ill-gotten personal information can give fraudsters better opportunities to impersonate trusted contacts and access additional systems and data. Teams are particularly vulnerable when handling supplier payments and acting on bank account change requests.
We saw similar risks with the Optus and Medibank breaches – as the number of major breaches grows, there’s an increasing likelihood that a cybercriminal might leverage victims’ data for tactics like phishing messages or business email compromise (BEC) attacks.
How can finance leaders protect their organisations?
You can’t control the security practices of suppliers or other external organisations. But you can protect your own organisation's finances by shoring up internal controls and alerting staff to heightened risks.
Here are some of the steps that CFOs and other finance leaders can take.
Strengthen your call-back controls: These types of controls offer some of your best defences against social engineering and BECs. Put simply, AP staff can’t trust the information they receive in emails – look to independently verify information like phone numbers rather than going off information on invoices or emails, since these can be manipulated. And don’t ask questions like, “Have your account details changed to X?” Ask open-ended questions in case a malicious actor has intercepted the call.
Keep employees in the know: Regular anti-cybercrime training can keep common tactics front-and-centre in employees’ minds, while timely warnings encourage staff to take a beat even during busy periods. Threat actors sometimes deliberately wait for hectic periods because they know that employees are more liable to overlook little details or skip a step in a financial control process. Subscribe to our newsletter to get regular updates on the latest scams and risks to AP teams.
Equip teams with technology: Informed staff make for a stronger security posture, but no one is perfect. Technology-enabled solutions can automate some of the processes that are more vulnerable to human error, and can arm AP staff with additional information while processing payments and onboarding suppliers.
Call-back Control Procedure Template
Are your call-back controls strong enough to mitigate your fraud risks, even as cybercrime becomes more frequent and more sophisticated?
Download our template to ensure your team is correctly performing these critical measures.