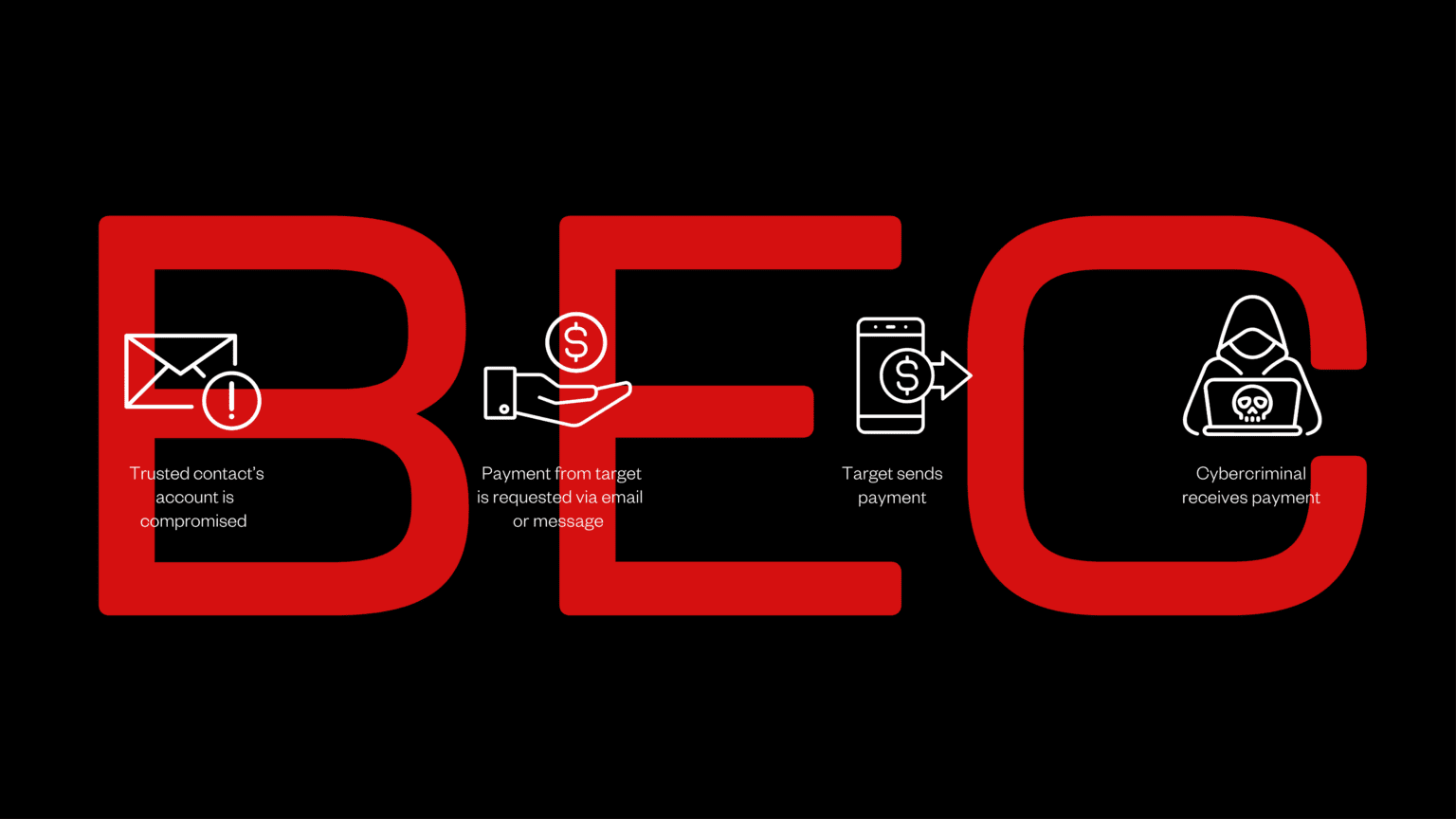
1. Assessment and planning
Begin by identifying your organization’s “crown jewels”—the assets most likely to attract threat actors, such as financial resources or sensitive data.
Next, determine who will conduct the testing within your function. Consult with IT, risk mitigation, and legal teams to obtain authority for testing. These consultations can help you understand relevant compliance or regulatory obligations and consider past incidents that may influence the testing scope.
While many organizations already know which staff have access to critical assets—often within finance and AP functions—it’s important to map out your actual landscape. This includes identifying exact user permissions and determining how many procedures are subject to anti-fraud controls.
Once you have a clear picture of the assets and employees most at risk, define the scope of your testing. This should include processes, policies, and procedures to ensure comprehensive coverage.
Policies
Think of policies as the laws that direct how individual employees, departments, and the entire organisation should operate. These are usually aimed at improving compliance, security, efficiency, and visibility in dayto- day operations.
Processes
These build upon the organization’s policies by providing a high-level overview of what, who, and when. Processes are often developed by management (e.g. the AP manager) and detail what specific tasks need to be executed, who has responsibility for executing each specific task, and when each task needs to be executed.
Procedures
Whereas processes are higher-level overviews, procedures are often more granular and outline the ‘how’ of different processes. These tasks tend to have the most direct impact on how employees carry out their responsibilities.
2. Testing and documenting
Once you’ve identified the priorities and scope of pressure testing, you can set a timeline for testing, especially if the testing will be a routine occurrence. While factoring in your most critical processes or vulnerabilities is important, it’s also reasonable to start with smaller tests and ramp up to more complex testing over time.
This approach lays the groundwork for simulating the attacks or fraud tactics you’ve chosen. During this phase, it’s essential to characterize each vulnerability and document the outcomes of every simulated tactic.
Documentation will be particularly important as you look for weaknesses such as:
- A lack of awareness: Among staff, contractors, and suppliers regarding fraud tactics or common cyberattacks like phishing or vishing.
- Incomplete checks or verification: Missing or inadequate verification of information.
- Inadequate detection processes: Ineffective measures to identify fraud or cyber threats.
- Inefficient segregation of duties: Poorly implemented separation of financial responsibilities.
- Weak technology or system controls: Insufficient safeguards within IT infrastructure.
- A lack of oversight or documentation: Missing processes for tracking actions or maintaining accountability.
- Unnecessarily manual tasks: Tasks with few or no guardrails for human error.

3. Reporting and remediation
Analyze documented outcomes by:
- Identifying the most critical risks or vulnerabilities: Focus on areas that pose the greatest threat to your organization.
- Suggesting steps for addressing vulnerabilities: Provide actionable recommendations, including timelines and dependencies for resolution.
- Determining owners: Assign responsibility for addressing vulnerabilities and identify other functions that need to be engaged.
- Recommending other areas for improvement: Highlight additional opportunities to strengthen processes and systems.
Anti-cybercrime strategy
Pressure testing is just one cornerstone of a comprehensive anti-cybercrime strategy. However, it can inform all other elements of your strategy, including how and where you focus resources.
Let’s take a look at how adversarial thinking and simulated fraud attempts can enhance decision-making across each of these elements.
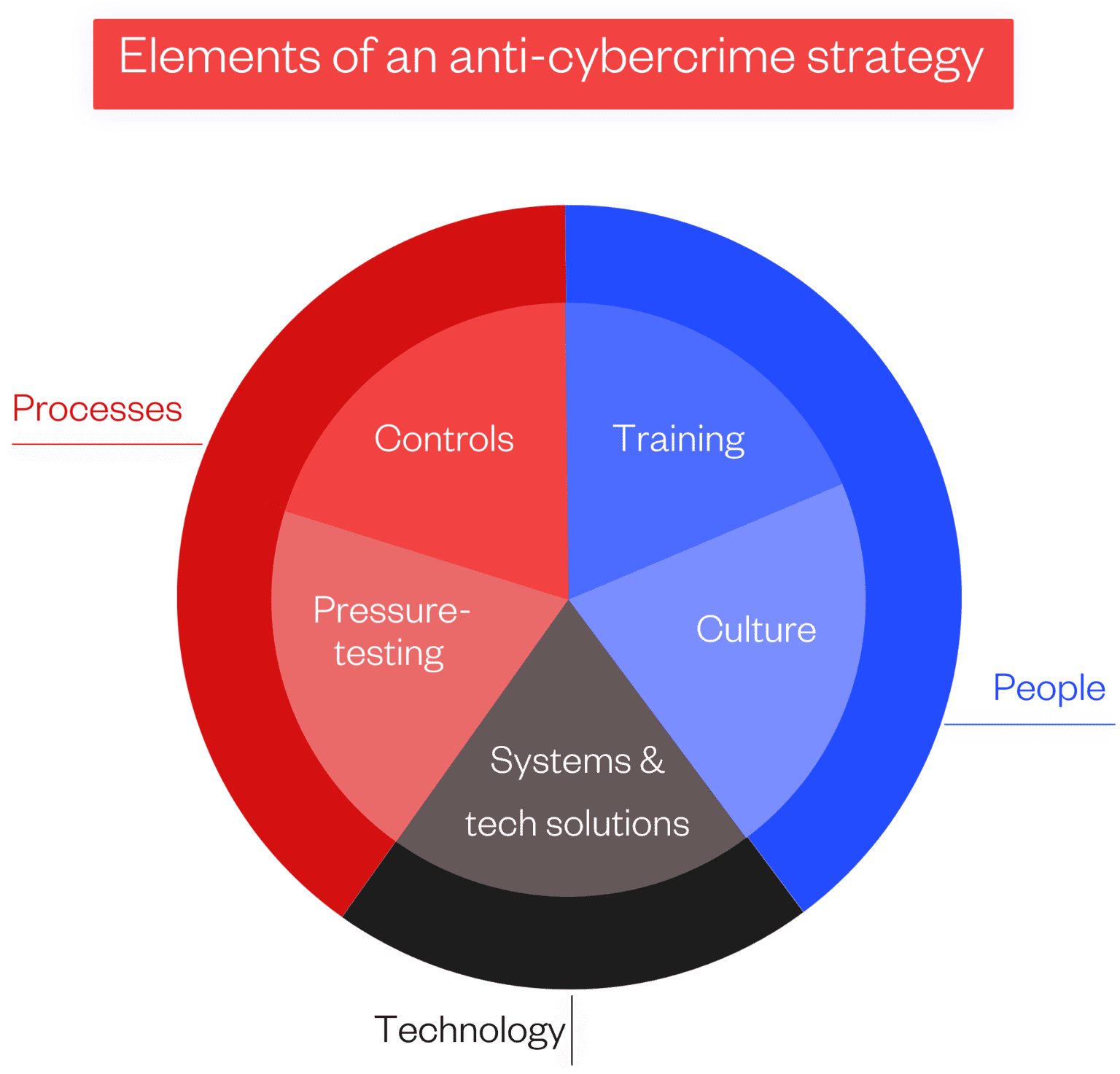
People
Staff training is crucial for any risk mitigation strategy, and modules should be developed in collaboration with IT or security specialists. Many organizations already run cybersecurity and fraud awareness training programs.
But dedicated training may be necessary—pressure testing can help you tailor these programs for different employees, especially those who are more likely to be targeted or have access to more sensitive processes and data.
Alongside general security hygiene, training for finance and AP staff should aim to improve understanding of:
- The tactics scammers use to manipulate information or engineer certain responses, including new tactics enabled by generative AI and synthetic media
- The risks your organisation could face when suppliers or other third-party organizations are breached
- Common red flags of social engineering, phishing, invoice manipulation, or insider threats
Regardless of training specifics, ensure that it’s both regular and relevant. Digital boundaries tend to blur between professional and personal, too, so consider training that helps employees understand how to protect themselves—both at home and at work.
We pivoted to training that shows staff how to protect themselves and their family. By doing that, we had a 100% uptake. Yes, we want you to be vigilant in the organization, but, by osmosis, [staff] brought that same level of awareness and vigilance into the business naturally.
– Damian Seaton, Founder and Managing Director, Cyber Audit Team (On The Defense)
Culture
Mitigating fraud risks also requires a culture that aligns everyone in your organization around efforts to prevent cybercrime. That includes:
- Forging an atmosphere of trust between management and employees: Trust starts with open, two-way communication, empowering both management and staff to contribute insights and ideas. Pressure testing doesn’t need to jeopardize this, either—staff should be aware of risk mitigation strategies and the role of pressure testing. Testing needs to be communicated as a routine way to uncover vulnerabilities, not to embarrass or blame any individual or team.
- Fostering a safe environment: It’s essential that employees feel comfortable flagging suspicious activity, especially incidents that involve their own errors. The more comfortable an employee feels to report concerns, the more likely they are to speak up quickly if they open the wrong attachment or make the wrong payment.
Often, this requires cultivating a deeper understanding of cybersecurity and risk mitigation: sophisticated fraudsters are looking to capitalize on human error, and no employee is immune or infallible.
Processes
Controls and pressure testing
With scam tactics and fraud incidents becoming increasingly sophisticated—and increasingly digital—your controls will need to be just as sophisticated. A robust anti-cybercrime strategy, validated by pressure testing and formed in collaboration with other functions, is crucial for assessing, implementing, and remediating these sorts of controls.

Technology
This guide has explored many ways in which cybercriminals are leveraging technology to work more efficiently and at scale, so don’t cede technology-enabled advantages. The right systems and solutions can help you automate processes without sacrificing efficiency. It’s not about automating everything, though—some solutions simply arm your employees with clearer insights and better information for decision-making, further minimizing risks of human error or social engineering.
Look for solutions that provide additional protection around your crown jewels and the people or processes most likely to face scammers’ tactics.
Lastly, no single solution can fully eliminate your fraud risks, so choose solutions that integrate with other necessary systems and processes. Employee experiences should still be as efficient and seamless as possible—after all, clunky, slow experiences tend to raise the risks of error, corner-cutting, and poor morale.
Protecting your organization isn’t about playing defense anymore—it’s about getting inside the mind of potential attackers. The old ways of managing risk are no longer sufficient in today’s world of ultra-organized cybercrime syndicates and technology-driven threats.
Practices like red teaming and penetration testing may be the domain of cybersecurity specialists, but they’re underpinned by important concepts that finance leaders can and should apply to their own functions.
Think of it like this: the best defense is a team that can spot vulnerabilities before the bad guys do. By constantly questioning how things work, imagining worst-case scenarios, and poking holes in your own processes, finance teams can act as their organizations’ final guardrails against cybercrime and close the intra-departmental gaps that cyber-fraudsters have long exploited.