How Vulnerable Are Your Emails?
Business email compromise (BEC) continues to plague businesses around the world. According to the FBI's Internet Crime Report 2021, 35% of all cybercrime losses were attributed to BEC attacks with almost $2.4 million in victim loss.
Australia had the world's fifth highest number of reported victims behind the US, India, the UK, and Canada, which is staggering given the size of the Australian population relative to the rest of the world.
In this blog, we break down how business email compromise BEC scams in Australia are orchestrated along with what you can do to prevent BEC attacks.
What is Business Email Compromise?
Business email compromise (BEC) is a type of email scam targeted at organizations to deceive executives or employees into sending money to the attacker's bank account or revealing sensitive information.
BEC attackers can achieve this through phishing or malware to compromise a vendor’s email account or deceive employees through CEO/CFO impersonations.
Types of Business Email Compromise Scams
According to Microsoft Security, there are five types of BEC scams:
CEO Fraud
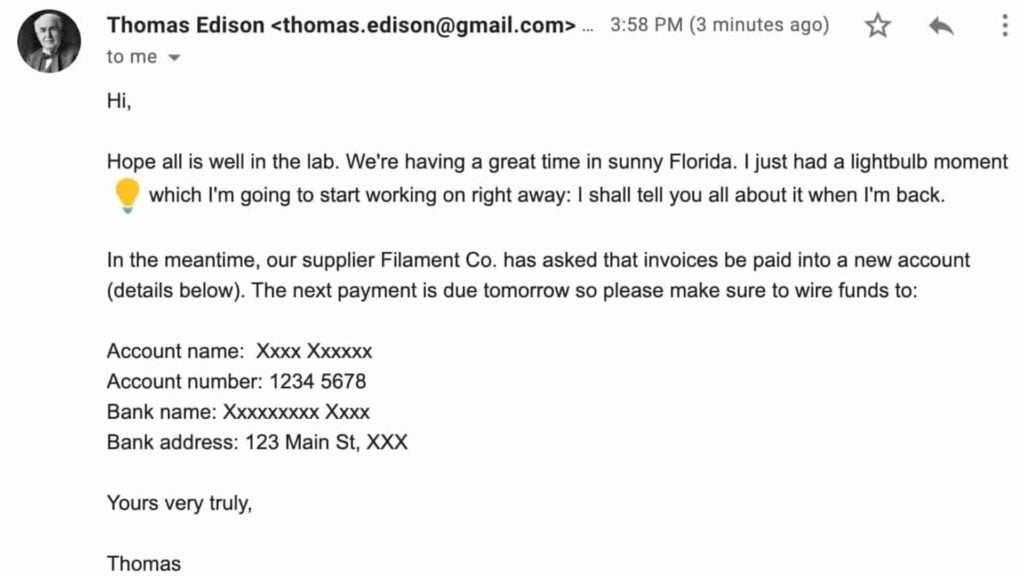
Attackers compromise an executive’s business email account (CEO or CFO) and send an email to an employee requesting funds to be transferred to a fraudulent bank account.
Email Account Compromise
Through the use of phishing or malware, attackers compromise an employee's email account to email fraudulent invoices to a vendor to request invoice payments to fraudulent bank accounts.
False Invoice Scheme
Criminals may impersonate a legitimate vendor to send a fake bill for items that were not ordered, requesting organizations to transfer money to a fraudulent bank account. Another method is criminals committing an email account compromise on a targeted vendor to edit the existing bank details listed on the invoice to receive payments.
Executive, Employee, or Attorney Impersonation
Oftentimes, an attacker may obtain personal information to impersonate executives, employees, or solicitors. They then email employees within the organization to pay an invoice or alert managers that bank details have been changed.
Data Theft
The goal of this attack is to steal company information like phone numbers or email contacts to conduct BEC scams. The accounts payable department or HR department is usually targeted in this type of cyberattack.

How Does Business Email Compromise Work?
More likely sophisticated, skilled, and resourced organizations than anarchic ‘hackers’ – have a target organization or several target organizations in mind. However, they do not try to attack those target companies directly.
Instead, they set out to deceive them by first infiltrating the email systems of target companies’ suppliers and then using that access to imitate the supplier company and send the target company authentic but fraudulent BEC communication. Below is how one way a BEC attack may occur:
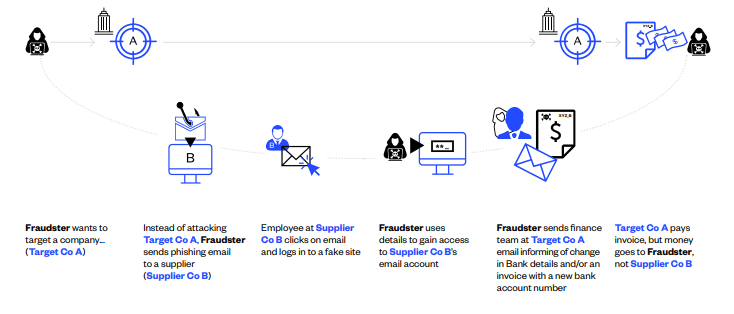
Vendor Email Compromise
1. Phishing for Login Credentials
Using the same monitoring and phishing email tactics used in supplier email compromise, the fraudsters gain access to your organization’s email system. While they may use other forms of attacks like social engineering tactics.
Given companies’ pervasive use of both email and connected applications, phishing is simple and only relies on a single person to be deceived to lead to broader access that enables the scam.
2. Infiltrating and Monitoring
Once they have login credentials to your organizations’ email system, they can monitor emails between staff members involved in the payments lifecycle.
While in supplier email compromise they are aiming to observe and learn the timing and language of communication between suppliers and customers, here fraudsters are observing your own internal payment authorization habits and protocols.
3. Imitating and Instructing
Once they have identified the chain of command and the correct protocols, the fraudsters will imitate high-level employees, the CFO or CEO, and at a relevant time, instruct a targeted junior staff member (likely in the Finance Department) to make a payment into a bank account belonging to the fraudster.
As with supplier email compromise, the email comes from the senior executive’s legitimate email address and does not contain any malicious attachments or obvious signs of fraud.
Fraudsters will often create a sense of urgency around the payment – for example, making their demands near the end of the working day or week. And, abusing the authority of the senior executive they are imitating, may even threaten profound consequences if payment is not made.
Many attacks are timed when the executive being imitated is traveling (ideally internationally) and the email is sent just prior to the executive’s flight departure. The fraudsters determine the travel schedule from the compromised email account and calendars.
The goal is to time the sending of the email such that if the employee is asked to make a wire transfer and wishes to call to confirm, the executive will be unavailable as he/she will be on a flight.
What is the Difference Between Phishing and Business Email Compromise?
Phishing is a type of cyberattack that cybercriminals use to trick employees into revealing sensitive information to commit fraudulent activities.
On the other hand, a business email compromise is a specific type of email phishing attack designed to impersonate senior executives to deceive employees to conduct wire transfers.
BEC attacks are specifically targeted at organizations through spoofed emails or false invoices.
How to Prevent Business Email Compromise
1. Gain Awareness and Promote a Security-Conscious Culture
Attend cyber events, subscribe to some of the many security newsletters available online, and distribute this information to your employees, colleagues, customers, and suppliers.
Different government departments, such as the Australian Cyber Security Centre, provide information and tips on how to mitigate cybersecurity risks. Certain cybersecurity firms – such as Kaspersky – can develop and run simulations and games which are both fun and educational for everyone in the organization.
Crucially, encourage and then make it safe for staff to question any payment instructions that do not ‘look right,’ even if they are from very senior executives or trusted suppliers.
2. Review Your Company Practices
In particular, look at your password and other email security controls. Strengthen your company’s passwords by making them longer and more complex. Certainly, do not share passwords across multiple sites or permit weak passwords.
A two-step authentication of a user’s identity should be implemented on all apps – including particular email systems. It is a simple and powerful measure. Identity management tools are also effective.
3. Enforce Protocols in Finance Teams
These include the separation of duties and independent verification for changes to the banking details. Never trust or rely on emails for bank account changes. And any all-new supplier additions or changes should be checked via a call back to the supplier, again using an independently sourced phone number.
Restrict and isolate access to ERP modules and applications. Only give certain people the access that they need. Finally, set up exception reporting in your ERP wherever possible.
4. Create and Enforce Policies
Recognize that employee email accounts are gateways to extremely sensitive information and phishing attacks. So, your policies might, for example, restrict what information can be kept in a legitimate email account and for how long it can be kept before securely archiving it.
Set up email alerts for exceptional incidents. This can be set up on most modern email systems that might alert you if someone from another country, say logs into your system or if your account is sending out large numbers of emails in a brief period.
Promptly remove access to your system once freelancers, consultants, and staff have left the company.
5. Use Tools to Secure and Verify Details Throughout the Payment Lifecycle
Along with multi-factor authentication tools and email encryption. You should also verify all suppliers at all key points throughout the payment lifecycle – that is, at the stages of supplier onboarding, supplier changes and maintenance, payments-file upload, and at the point of final payment.
There are, however, few systems or tools that cover the entire payments lifecycle. Secure supplier onboarding processes may lack automation and automated ERP supplier onboarding may lack security features.
What To Do If Your Email Has Been Compromised
If you have fallen victim of business email compromise, you may be liable. Here are actions you should take if you suspect a BEC attack has occurred:
If you have sent money or revealed banking details to a scammer, contact your bank immediately
Report to the police and the cyber incident to the Australian Cyber Security Centre (ACSC)
Notify other key stakeholders in the business and conduct a company investigation
Immediately lockdown compromised email accountings and security network
How Can Eftsure Help?
Losses resulting from BEC and electronic payments are extremely difficult to prevent and recover.
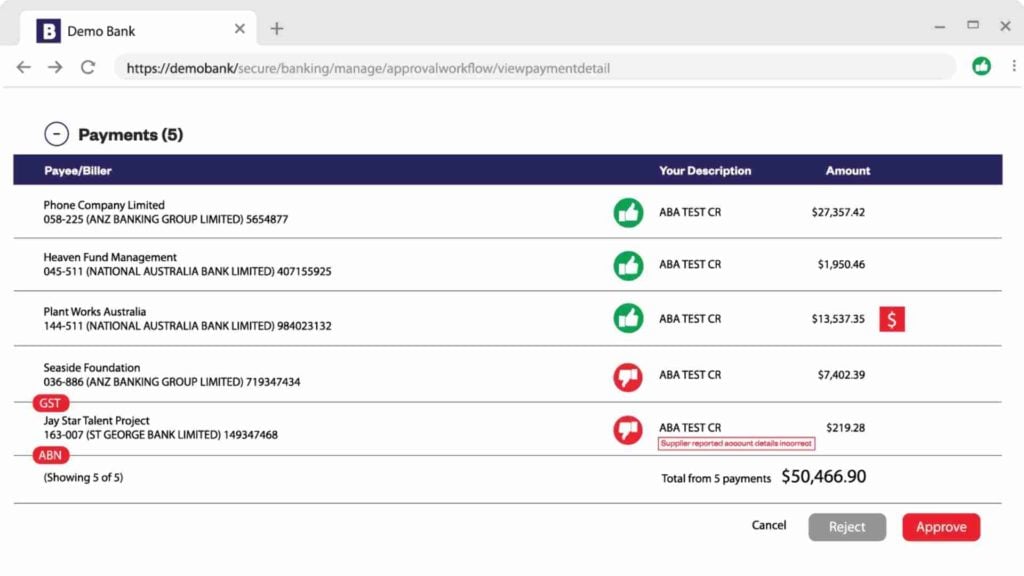
Australian banks do not verify that BSB and account numbers match account names at the point of payment. So, if the payment has been made into the wrong account, the banks do not detect or signal it.
BEC attacks exploit this fact – they change bank account details but leave the Payee name the same.
Eftsure’s fraud tech solution does what other systems cannot: it provides real-time supplier verification and alerts throughout the payment lifecycle: at the point of supplier onboarding, through supplier changes, prior to uploading a payments file, and finally at the Point of Payment; in your banking environment.
In doing this, Eftsure is unique in its ability to mitigate the risk of loss due to business email compromise be it executive fraud or supplier email compromise.
Contact Eftsure today, for a full demonstration of how we can protect your payments.
Anyone Can Be a Victim
Recently, the owner of homewares business Sage & Clare fell foul to this step of a BEC scam, losing $10,000 when she placed an order with a long-term supplier in China. For about three to four months she was actually exchanging emails with the scammers and not the suppliers themselves. Just before she had to make the final payment for the order, she was told the supplier had changed its bank account due to auditing issues. She later found out that the order and the $10,000 she paid had gone to the crooks.











