What is MFA?
Multi-factor authentication (MFA) is a security method that requires users to prove their identity using two or more distinct factors before accessing …
Imposter scams are a type of fraud where scammers pretend to be trusted individuals, companies, or government agencies to deceive victims into providing money, personal information or access to online accounts.
Scammers create fraudulent websites to impersonate trusted figures and deceive victims into revealing sensitive information. They exploit trust, urgency, and fear to manipulate individuals and businesses into making payments or disclosing sensitive data.
Imposter scams have become one of the costliest types of fraud. In 2023 alone, U.S. consumers lost over $2.7 billion—or 27% of the $10 billion lost to all types of fraud in the same year.
Imposter scams are a type of fraud where scammers pretend to be someone else, often a government official, financial institution, or trusted individual, to trick victims into sending money or divulging personal information. These scams can take many forms, including phone calls, emails, text messages, and social media messages. Scammers pretend to be credible sources to create a sense of urgency or panic, making it difficult for victims to think clearly and make rational decisions. The goal is to manipulate the victim into acting quickly, often resulting in financial loss or compromised personal information.
Imposter scams typically follow a recognizable pattern. The scammer impersonates a trusted source and uses pressure tactics to make the victim act quickly. Scammers may manipulate caller ID to appear as if they are contacting potential victims from legitimate government or business numbers.
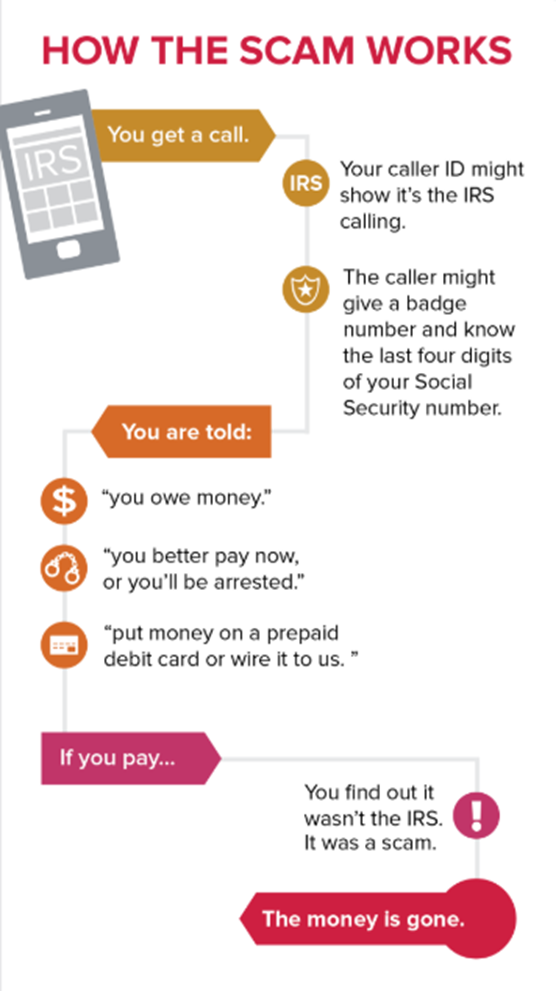
The process usually follows these key steps:
While imposter scams come in many shapes and sizes, here are three types most likely to affect businesses.
Government impersonation scams are one of the most common imposter scams. Here, scammers pose as government officials and claim the victim owes taxes or fines. Victims are then told to pay via wire transfer, cryptocurrency, gift cards or some other less traceable payment method. Scammers may claim individuals could miss out on some government benefit if they fail to comply with fraudulent requests for personal information or payments.
Government agencies, however, do not demand payment through these methods, which makes such requests an obvious red flag. Scammers create a sense of urgency by threatening consequences, such as arrest or suspension of benefits, unless the victim pays immediately, often demanding unconventional payment methods.
BEC scams target businesses and financial teams. Fraudsters impersonate executives or vendors and request urgent payments or bank detail changes.
For example, an accounts payable clerk may receive an email from the “CEO” requesting an immediate wire transfer.
Scammers create a sense of urgency by demanding that the victim pay immediately, often bypassing standard approval processes.
One indicative sign of a BEC scam is a request for immediate payment that bypasses standard approval processes.
In a tech support scam, individuals may be alerted by a pop-up or message that claims malware has been detected. Victims are prompted to call a phone number where scammers demand payment for “technical support” services.
Scammers often create fraudulent websites that appear legitimate to deceive victims into calling for these ‘technical support’ services.
Note that legitimate companies do not send pop-up alerts asking users to call for urgent technical support.
There are several warning signs that can help you identify an imposter scam. These include:
Recognizing these red flags can help you avoid falling victim to an imposter scam and protect your personal information.
Government agencies, such as the Federal Trade Commission (FTC), Social Security Administration, and Internal Revenue Service (IRS), have strict protocols for communicating with the public. Here are some key things to know:
Understanding these protocols can help you identify and avoid government imposter scams.
Recognizing the warning signs of an imposter scam can prevent financial loss. Key signs to watch for include:
Preventing imposter scams requires proactive security measures and proper training for employees. Here are some key prevention strategies:
Education is paramount since scammers often rely on a victim’s lack of knowledge. To strengthen employee awareness, companies should:
Multi-factor authentication (MFA) can also prevent scammers from obtaining access to online accounts. Key recommendations include:
Vendor impersonation scams – where attackers pose as legitimate suppliers – are one of the most common forms of business-related imposter fraud. To prevent vendor impersonation scams, businesses should:
If you suspect that you have been a victim of an imposter scam, it’s essential to report it to the relevant authorities. Here are some steps you can take:
Remember, reporting imposter scams can help prevent others from falling victim to the same scam and can also help law enforcement agencies track down and prosecute scammers.
The consequences of imposter scams can be severe, impacting both individuals and organizations. As documented earlier, financial losses from imposter scams are substantial.
Companies hit with BEC attacks often face even larger financial losses, with these scams the second costliest category of cybercrime in 2023. In New Jersey, for example, 628 businesses lost an average of $223,041.73.
Data breaches often occur as a result of impersonation. Fraudsters may steal a victim’s bank account details or login credentials to commit identity theft or obtain unauthorized access to accounts.
Reputational damage is another major consequence, with businesses known to have been impersonated losing the trust of customers, vendors, and other stakeholders. This loss of confidence can have a long-term impact on client relationships and growth.
Multi-factor authentication (MFA) is a security method that requires users to prove their identity using two or more distinct factors before accessing …
Accounts payable fraud is a deceptive practice that exploits vulnerabilities in a company’s payment processes. It occurs when individuals—whether employees, vendors or …
Two-factor authentication (2FA) is a security measure that requires users to verify their identity with two separate authentication factors before accessing an …
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.