What Can Scammers Do with Your Phone Number?
When cell phones first became popular, no one thought they’d become what they are today. For the first few years, it was …
Phishing is a common cyber scam, whereby cybercriminals or hackers attempt to obtain personal information through fraudulent emails, text messages or phone calls. Often, phishing attacks are effective because they will pose themselves as a reputable company, banking institution or government agency in an attempt to build trust while accessing highly sensitive information such as banking details, passwords, credit card numbers and more.
The term phishing was originally coined in 1996 when a group of hackers targeted users through the AOL (America Online) brand. At the time, AOL was a pioneer in the internet space and quickly became the most widely used and recognised internet provider in the United States.
In this timeframe, AOL began to tighten security measures, but groups of hackers began impersonating the internet giant, sending falsified emails and messages to AOL customers disguised as the brand. Given this was a brand new era of digital communication, many consumers lacked awareness on the topic and quickly became victims to fraud and identity theft.
Since the mid-1990s, hackers and cyber criminals have only become smarter and better equipped in the space of phishing scams. It remains a huge and continuously growing problem today. According to Statista, phishing was the most prevalent scam in Australia in 2022, they noted over 74.5 thousand incidents were reported.
Hackers and cyber criminals will emulate a well-known organisation, banking institutions or government agencies via email to try and gain access to personal information and data. Sometimes the emails will contain links that, when clicked, take the user to a form to submit personal information or login details. In other instances. The emails may contain attachments that lead to the installation of malware if opened.
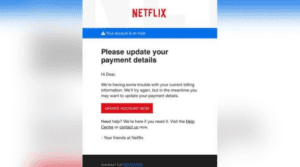
Similar to email phishing, spear phishing takes a similar approach but is unique in that it’s more tailored and targeted. Rather than sending emails to a large group of people at random, this would be an email attack focus on a specific group of people or organisation. Spear phishing is a type of social engineering, and usually emails will appear as if coming from a trusted person.
Attacks over SMS messaging (text messages), usually containing malicious links. These can range from a falsified message from FedEx, encouraging you to update your details for an upcoming delivery, to messages containing information on claiming a prize.
These are criminal attacks made over the phone. Often a person will receive a phone call and the caller will impersonate a bank or government agency, looking to gain access to personal information or incentivising them to take action on something.
Business Email Compromise (BEC)
Cybercriminals gain access to business email accounts to impersonate people within an organisation to get access to sensitive information or to prompt an action to take place, such as a funds transfer.
This one is a bigger effort by hackers, where they will use redirects to guide users onto a malicious or fake website. These websites can appear almost identical to common ecommerce stores, allowing you to complete a purchase online while unknowingly giving personal, login and credit card information.
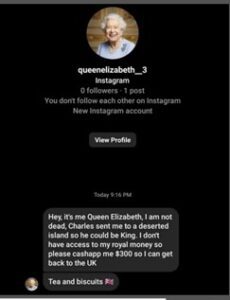
Cyber criminals will create fake accounts impersonating brands, government agencies, or even close friends, to reach out via direct message to start a conversation with the intent to gain sensitive information or money.
Hackers will replicate an existing email and either add or replace an existing link or attachment, which will result in adding malware to the recipients computer. Other ways of using clone phishing can include the hackers adding a link to a cloned invoice, with updated banking details that, without proper payment protection in place, can go easily unnoticed by the recipient.
Similar to pharming, scammers will use search engine results to drive people to a malicious website on a false URL.
Last but not least, never pick up an unknown USB. USB phishing leads to the downloading of malware onto a computer, which can then provide cyber criminals access to everything saved on the system.
Cyber scammers are always looking for their opportunity, targeting everyday people, organisations, and governments, so it’s important to remain vigilant. Unfortunately, we live in an era where it’s best to question everything, rather than assume any request for your personal information is 100% safe and secure.
According to the Federal Trade Commission, these are common themes in phishing emails:
In a phishing email, often scammers will change a single letter in an email address, or they will make a variation a person’s or company’s email to make it seem legit.
If the URL doesn’t appear to be to a legitimate website affiliated with the source of the request, don’t click it. For example, if you receive a text from AusPost to update your shipping details, but the link doesn’t mention Australia Post or the website, this could be a red flag for a malicious link.
Sometimes, if the URL is not evidently written in a message, it’s worth hovering over the button or link to see a preview of the link appear before you click anything suspicious.
Many times, scammers and cyber criminals will use AI to help generate messages. Sometimes you’ll notice poor grammar or spelling mistakes in a message, which can signal it hasn’t come from a reputable or legitimate source.
Banks and other reputable subscription software will have your personal details on file. If your messages are not personalised, but they are asking you for information, it’s best to contact the company directly and confirm if this is valid.
When phishing messages are sent on social media, check the handle and details on the account to see how likely it’s actually who they appear to be. If the account is new and/or lacks friends and followers or photos and details, don’t engage with the request.
If you’re still unsure about a request for your information, it’s best to reach out to the company or person directly to confirm it’s them seeking the information. For example, if you receive a suspicious email from your bank, reach out to them over the appropriate channels (phone or email) and explain what you’ve received and ask if it’s safe to proceed with the request.
Note: if you’re looking for a phone or email, don’t take any information from the messaging source. Be sure to head directly to the company website from your browser and pick-up actual contact details.
Ensure you’re constantly running updates on your electronic devices, especially when it comes to security upgrades to keep you safe from malware.
This ensures when you login to important accounts, you have a way to validate yourself as the user. MFA can include a text message code at login or using an authenticator code generator, such as Google Authenticator or Microsoft Authenticator.
From a personal perspective, this can look like installing anti-virus software on your laptop to keep hackers and scammers from getting into your personal devices. Alternatively, from a business standpoint, investing in tools like accounts payable protection software (Eftsure), provides an added layer of security to keep payments out of the hands of scammers. Falsified invoices or payment requests will be immediately flagged and checked, so funds always remain safe.
Although we hope this part of our article never has to be used by our readers, it’s important anyone who feels they may have been affected by a scam receives the support they need as soon as possible.
In the event you receive a phishing attempt, it’s important to report it, even if you we’re able to recognize it before submitting your details. The Australian Cyber Security Centre breaks down several different scenarios, with appropriate next steps to follow for phishing protection.
No matter what, be sure to report the scam to the National Anti-Scam Centre, and in the event you’ve become a victim, you’ll need to lodge a report through ReportCyber and then contact your financial institution.
Reporting helps to stop future scams, protect others in vulnerable situations, and ensures victims get the support they need to recover from potential hardship.
When cell phones first became popular, no one thought they’d become what they are today. For the first few years, it was …
When Mr. Beauchamp watched a video of Elon Musk – the world’s richest man – recommend a certain investment platform to make …
Your company delivered the good or service it promised to a client and now it’s time to collect the funds owed to …
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.