What are imposter scams?
Imposter scams are a type of fraud where scammers pretend to be trusted individuals, companies, or government agencies to deceive victims into …
Multi-factor authentication (MFA) is a security method that requires users to prove their identity using two or more distinct factors before accessing an account, app, or system.
Unlike single-factor authentication – which relies on just a password – MFA adds extra protection by incorporating an authentication method that involves multiple verification factors, making it much harder for cybercriminals to obtain access to compromised accounts.
Despite its importance, MFA remains somewhat underutilized.
Industry regulator The Office of the Australian Information Commissioner (OAIC) claimed that a lack of MFA was a significant factor in the Medibank data breach.
In a separate 2024 attack, a hacker compromised up to 165 customer organizations of the data storage and processing firm Snowflake. Like Medibank, these organizations had also failed to configure MFA protection.
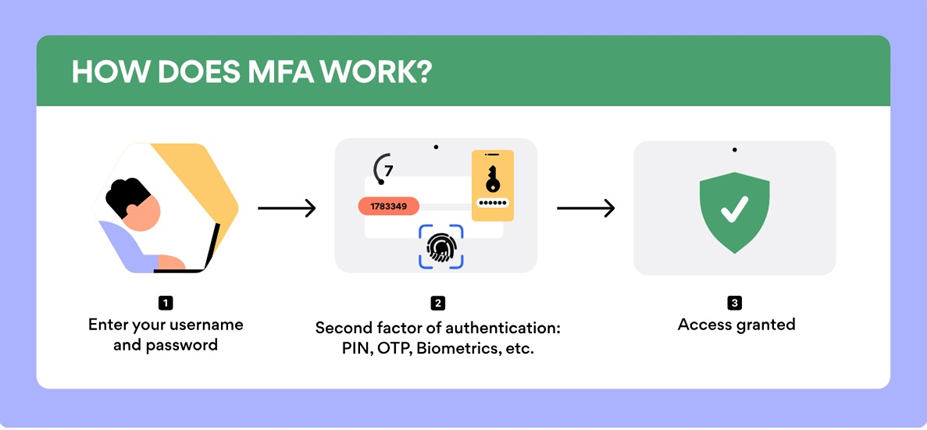
MFA works by requiring at least two forms of authentication from three possible categories. To gain access, users must provide evidence from two or more of the following:
This layered approach prevents hackers from accessing accounts even if they manage to steal a password. According to Microsoft, MFA blocks 99.9% of account compromise attacks. Adaptive authentication, also known as Risk-based Authentication, assesses additional contextual and behavioral factors during the login process to calculate the risk level of a login attempt, determining whether users need to provide extra authentication factors based on their usual login patterns and the circumstances of their access.
There are several authentication methods in widespread use for MFA, and each has particular strengths and weaknesses.
Authenticator apps like Google Authenticator, Microsoft Authenticator, and Authy are some of the most popular.
Here’s how they work:
SMS-based authentication involves sending a one-time passcode (OTP) to a user’s phone. While widely used by Australian banks, it has security vulnerabilities.
SMS authentication is vulnerable to SIM-swapping attacks, where scammers trick phone providers into transferring the victim’s phone number to a device controlled by the attacker.
Hardware security keys offer one of the most secure MFA methods. Among the various MFA authentication methods, security keys stand out as a robust option due to their physical nature and cryptographic security. They are small, USB or NFC-enabled devices used to verify user identity.
Users insert the key into their device or tap it on their phone to authenticate their login. Hardware keys use cryptographic protocols to prove identity, making them resistant to phishing attacks.
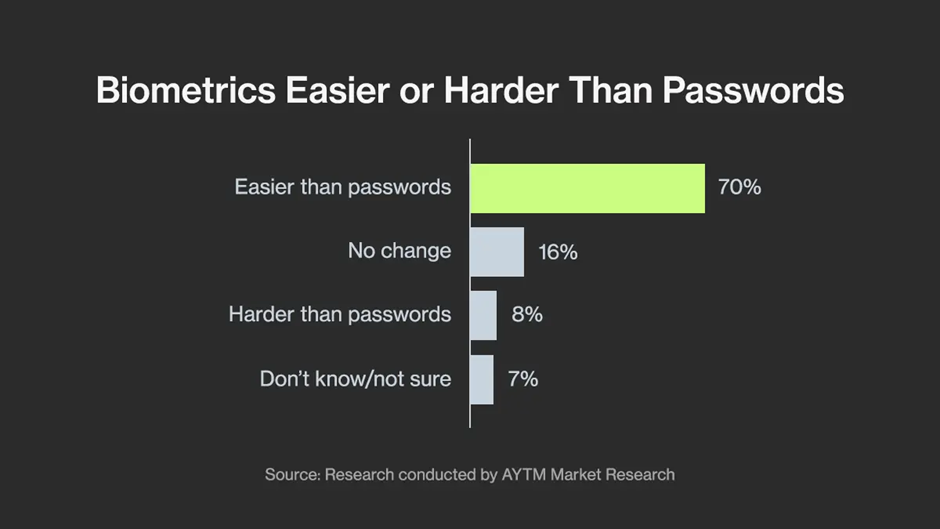
Biometric authentication relies on the user’s unique physical characteristics to verify a user’s identity. This method is increasingly used on smartphones, banking apps, and laptops.
Here, the process is simple. Users scan their fingerprint, face, or voice using a biometric sensor, and the system compares the data to stored biometric data to confirm the user’s identity.
Trusted devices are devices that users mark as “trusted,” so they don’t have to complete MFA for every login.
Push notifications are another simple and secure method.
When a login attempt is made, a push notification is sent to the user’s device. The user can approve or deny the login attempt with one tap.
A multi-factor authentication system is a robust security process designed to protect online accounts by requiring users to provide two or more verification factors before gaining access. Unlike single-factor authentication, which relies solely on a password, a multi-factor authentication system employs multiple authentication factors to verify a user’s identity. These factors can include something the user knows (like a password), something the user has (such as a smartphone or security token), and something the user is (biometric data like fingerprints or facial recognition).
By leveraging multiple authentication factors, this system significantly reduces the risk of unauthorized access. Even if a cybercriminal manages to obtain one authentication factor, they would still need to bypass additional layers of security to gain access. This makes it much harder for attackers to compromise multiple accounts using the same password. Implementing a multi-factor authentication system is a crucial step in safeguarding online accounts and ensuring that only the user can access their sensitive information.
MFA is one of the most effective measures for protecting organizations and individuals from cybercrime. The variety of authentication methods available, including those enhanced by machine learning and artificial intelligence, play a crucial role in enhancing security. With more businesses moving to cloud-based systems and hybrid work, it’s more important than ever to secure online accounts and apps.
Hackers often steal passwords via phishing emails or brute-force attacks.
Without MFA, these stolen credentials allow instant and unrestricted access to accounts. With MFA, on the other hand, hackers still need to pass an extra layer of security which is far more difficult.
The Essential Eight framework – promoted by the Australian Cyber Security Centre (ACSC) – identifies MFA as one of eight key strategies for safeguarding digital assets.
Organizations that fail to implement MFA may face compliance risks, especially when handling sensitive data.
Zero-trust security requires constant verification of users and devices. MFA fits neatly into this framework, as users must prove their identity every time they access a new system, app, or resource.
Email accounts, cloud-based workspaces, and financial systems are prime targets for cybercriminals. MFA secures these accounts, making it significantly harder for attackers to compromise them.
Businesses can follow these steps to implement MFA:
While two-factor authentication (2FA) and multi-factor authentication (MFA) are often mentioned together, they are not identical. 2FA is actually a subset of MFA, as it involves the use of exactly two authentication factors. Typically, 2FA combines something the user knows, like a password, with something the user has, such as a one-time password (OTP) sent via SMS or email.
On the other hand, MFA can involve two or more authentication factors, providing an even higher level of security. For instance, MFA might combine a password, biometric data (like a fingerprint), and an OTP generated by an authenticator app. While 2FA adds a significant layer of security compared to single-factor authentication, MFA offers even greater protection by requiring multiple authentication factors. This makes it much more challenging for cybercriminals to bypass all layers of security and gain unauthorized access.
Legislation and regulation play a pivotal role in encouraging the adoption of multi-factor authentication (MFA) to protect sensitive data. Various laws and regulations around the world mandate the implementation of MFA to enhance security. For example, the General Data Protection Regulation (GDPR) in the European Union requires organizations to implement MFA to safeguard personal data. Similarly, the Payment Card Industry Data Security Standard (PCI DSS) mandates that merchants use MFA to protect payment card information.
In the United States, industry-specific regulations like the Health Insurance Portability and Accountability Act (HIPAA) also require the use of MFA to protect healthcare data. These regulations ensure that organizations handling sensitive information adopt robust security measures, including MFA, to prevent unauthorized access and data breaches. By mandating the use of MFA, legislation and regulation help to promote its widespread adoption and improve the overall security of online transactions and data protection.
MFA is highly effective, but it isn’t foolproof, and some methods are more secure than others.
Various SMS-based MFA methods are vulnerable to SIM-swapping attacks as noted earlier. SMS messages are also unencrypted, which makes them more vulnerable to interception by nefarious actors.
Other challenges include:
Key takeaways:
Imposter scams are a type of fraud where scammers pretend to be trusted individuals, companies, or government agencies to deceive victims into …
Accounts payable fraud is a deceptive practice that exploits vulnerabilities in a company’s payment processes. It occurs when individuals—whether employees, vendors or …
Two-factor authentication (2FA) is a security measure that requires users to verify their identity with two separate authentication factors before accessing an …
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.