What is MFA?
Multi-factor authentication (MFA) is a security method that requires users to prove their identity using two or more distinct factors before accessing …
Payment authentication is the process of verifying the identity of a customer before an online payment can proceed. This ensures that the person who wants to make a payment is the legitimate cardholder and not a fraudster.
Banks, merchants and payment service providers rely on five core factors to authentic payments:
In the process, payment authentication factors help businesses avoid several types of online payment fraud. These include identity theft, chargeback fraud, card testing, marketplace fraud and refunds to an alternative payment method.
Let’s return to the five core factors above to explain how payment authentication works in practice.
Customers will be asked to verify their details for at least one of the payment authentication factors, with tools such as multi-factor authentication requiring two factors.
The most common type of authentication relies on something the customer knows and that they alone should possess. Examples include account passwords, PINs and the answers to security questions.
Possession-based authentication involves verifying that the customer has access to an object, device, key, certificate, token or signature.
Payments made with a physical credit or debit card require the user to know the card number, expiration date and CVV code. Other providers may ask the customer to confirm a one-time password (OTP) via phone or email.
Inherence verification is one of the most sophisticated of the authentication types and relies on biometric data to verify the customer.
Services such as Apple Pay and Google Pay use facial recognition and fingerprints as part of their authentication process. Australia Post’s Digital iD app also uses facial biometrics to verify customers with a range of partner organisations.
Inherence is a popular form of authentication, with Deloitte reporting in 2019 that Australians were already making an estimated 100 million imprints a day using smartphone fingerprint scanners.
Location-based authentication takes the geographic location of the customer into account. This process is mostly supplemental and provides an extra layer of security in specific contexts such as mobile banking and eCommerce.
When a customer initiates a smartphone payment, for example, the payment provider can track their location via GPS, WiFi or cellular data. If the location of the buyer is considered high-risk or not where they typically make payments, additional authentication may be required.
Location-based authentication may be one way to combat card-not-present (CNP) fraud, which was responsible for $608 million in unauthorised transactions on Australian cards in FY23.
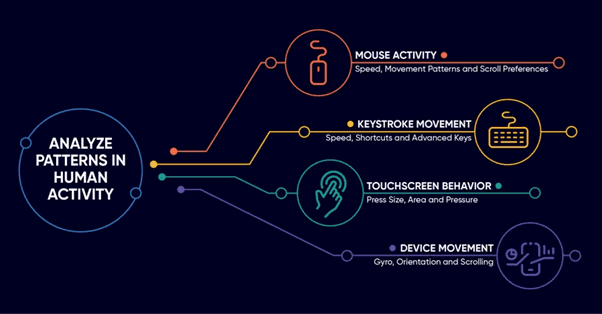
Behavioural authentication verifies a customer’s identity based on their unique behaviour patterns.
Behaviour-based factors are less prevalent than the more traditional authentication types. But there exists tremendous potential with machine learning algorithms able to analyse hundreds or even thousands of parameters on human behaviour and detect anomalies.
To that end, behavioural authentication leverages various aspects of a user’s interactions with their device. Some solutions measure the press size and pressure of touchscreen behaviour as well as the speed and scroll patterns of mouse activity.
Other more well-known applications include algorithms that analyse historical spending behaviour to better identify abnormal payments.
Various protocols and features authenticate payments and protect businesses and consumers alike. Many have been developed or refined in response to the increased prevalence and sophistication of payment fraud techniques.
3D Secure 2 (3DS2) is a payment authentication protocol used by Visa (Visa Secure), Mastercard (Identity Check) and American Express (SafeKey) to combat fraud and chargebacks.
The protocol helps providers comply with Strong Customer Authentication (SCA) requirements, which are outlined in the European Union’s Revised Payment Services Directive (PSD2).
SCA mandates the use of multi-factor authentication for certain types of electronic payments. To that end, the 3DS2 protocol must verify at least two of the three authentication factors in knowledge, possession and inherence.
3DS2 is the most common authentication method in Europe, and though its use is not legislated in Australia, many banks and other companies that deal with cross-border transactions have adopted it.
The Address Verification System is another payment authentication method with a particular focus on the prevention of credit card fraud.
The system – which is predominant in the US, UK and Canada – authenticates payments by verifying whether the billing address used in a transaction matches the address of the cardholder.
As such, AVS is commonly used to detect fraud in online payments and other contexts where a card is not present, such as mail order/telephone order (MOTO) payments.
In most cases, a request for address verification is sent with the payment request to the bank where the card is held.
The bank then checks the address provided with the one it has on file and returns a specific AVS code that indicates a full match, partial match or no match, among other results.
Based on this code, the seller can decide to approve the order, cancel it or investigate further.
The Card Verification Value is a payment security feature that is also prevalent in card-not-present (CNP) situations.
The CVV – more commonly known as the CVV number – is a three to four-digit number printed on the back of a debit or credit card (or on the front for American Express). In either case, buyers must enter this number at checkout to prove they have possession of the card.
In a similar way to AVS verification, merchants compare the CVV code provided by the customer with the code their bank has on file. Discrepancies may indicate that the buyer does not have physical possession of the card and the transaction is potentially fraudulent.
EMV (Europay, Mastercard and VISA) is a payment standard that enhances the security of debit and credit card transactions at a physical point of sale. It was developed by EMVCo – the same company responsible for development of the EDS2 protocol.
Authentication is achieved with a chip embedded in the card that generates a unique, one-time-use code for each transaction known as a cryptogram.
The cryptogram is then sent with the payment details to the card issuer before the card issuer decrypts the cryptogram to authenticate the transaction.
The use of a unique cryptogram is the cornerstone of EMV security. Unlike static data in traditional magnetic stripe cards, the data contained in a cryptogram is virtually impossible for fraudsters to steal and clone onto a new card.
Payment authentication faces many of the challenges inherent to the finance and cybersecurity industries.
Fraudsters pose the most obvious risk, and as authentication methods evolve, so do the tactics they employ to bypass them.
Some criminals use malware to compromise authentication systems themselves, while others use social engineering and phishing to steal personal information from customers and make unauthorised purchases.
Businesses that operate in multiple countries are also subject to different laws, requirements and systems, which increases the complexity and cost of both compliance and integration.
On the merchant side, the payment experience for customers can also be problematic. Multi-factor authentication protocols can add friction to the checkout process and may cause cart abandonment and customer dissatisfaction.
In the B2B space, thousands of businesses in Australia and the US trust in Eftsure’s payment verification technology to provide peace of mind when processing vendor and supplier payments. We provide businesses with the tools to prevent payment fraud, onboard new vendors and manage the accuracy of existing vendors’ banking and compliance data.
In summary:
Multi-factor authentication (MFA) is a security method that requires users to prove their identity using two or more distinct factors before accessing …
Imposter scams are a type of fraud where scammers pretend to be trusted individuals, companies, or government agencies to deceive victims into …
Accounts payable fraud is a deceptive practice that exploits vulnerabilities in a company’s payment processes. It occurs when individuals—whether employees, vendors or …
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.