Cyber Brief for CFOs: April 2024
All the news, tactics and scams for finance leaders to know about in April 2024.
Multiple media outlets are reporting that the International Cricket Council (ICC) has fallen victim to an alleged cyber-crime that saw the organisation wire-transfer around $2.5 million (USD) to fraudsters. It happened via a business email compromise (BEC) attack, a type of email scam that’s common in Australia.
According to ESPN, the alleged incident originated in the United States in 2022 and the ICC Board was updated about it last year.
Details are sparse right now because the cricket governing body has reported the alleged fraud to US law enforcement. We don’t know whether the scam happened over multiple payments, nor do we know whether scammers targeted the organisation’s head office or went through an ICC vendor.
In a BEC attack, scammers target an organisation and try to deceive its employees into making fraudulent payments or revealing sensitive information. They typically do this through phishing, malware or compromising the email accounts of trusted contacts.
This means that some BEC attacks don’t even require hackers to infiltrate your systems or data. Instead, they can use compromised accounts or data of vendors or consultants – or they can simply impersonate people like executives, suppliers or IT professionals and target employees when they know they’re most distracted or time-poor.
Here’s an example of a hypothetical BEC attack.
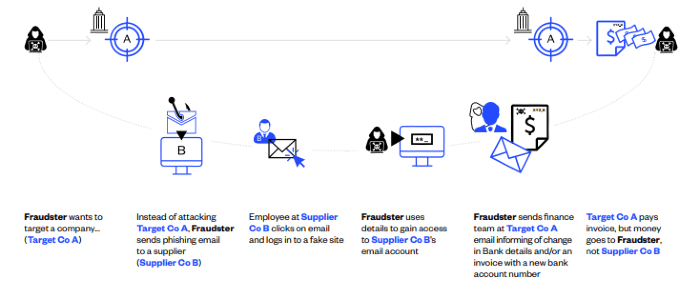
If you think your organisation is too smart to get caught in one of these scams, think again.
The ICC definitely isn’t alone. Some of the world’s most powerful brands and leading businesses have lost huge sums of money to BEC – sums that make $2.5 mil look a bit like pocket change.
Learn more about BEC attacks and how to spot them.
Social engineering is a cyber-crime tactic that relies on old-fashioned psychological manipulation to get access to valuable information or resources.
BEC scams rely on social engineering, which means that many of them aren’t technically sophisticated. That doesn’t mean they aren’t sophisticated at all, though – scammers can be unnervingly adept at impersonating executives or suppliers, waiting until strategic moments to make a move, and engendering trust with employees.
For instance, they might create whole websites and branding to imitate suppliers, as they did in the BEC scam used against Google and Facebook. They can also use psychological tactics to gain employees’ trust or send urgent requests when they know the team is likely to be busiest.
Why does this matter? While BEC scammers can benefit from infiltrating systems and exploiting vulnerabilities, many of the most lucrative cyber-crimes were carried out through social engineering tactics – not sophisticated hacking. This is especially critical for CFOs and other financial leaders, since their teams are the ones who are most likely to be on the frontlines against these types of scams. It’s also important because these are exactly the types of scams that your IT or security teams won’t be able to stop.
Like other BEC attacks before it, the ICC incident shows once more that security isn’t just an IT issue and that CFOs will need to reconsider traditional approaches to financial controls and supplier verification.
Otherwise, they may be leaving their organisations vulnerable to BEC and other online scams.
All the news, tactics and scams for finance leaders to know about in April 2024.
All the news, tactics and scams for finance leaders to know about in February 2024.
All the news, tactics and scams that finance leaders need to know about in January 2024.
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.