In today's digital world, data breaches have become a common threat, putting organizations worldwide at risk. For CFOs and AP managers, it's crucial to understand how these breaches lead to financial scams. Without this knowledge, you could fall victim to clever scams that not only cause direct financial losses but also damage your company's reputation and disrupt operations.
The challenge isn't just understanding this connection, but also taking action to break it. By working closely with IT, investing in strong cybersecurity measures, and staying up-to-date on the latest threats, finance professionals can better protect their organizations from the growing cybercrime menace.
The surge in data breaches: a global concern
In 2023, more than 892 data breaches were reported to the Australian Office of the Information Commissioner (OAIC). The situation is even worse in the United States, where data breaches shot up by 76%, totaling over 3,000 incidents. These breaches mean millions of compromised records, personal information, and sensitive data are now floating around on the dark web, fueling a worrying rise in financial scams.
One of the biggest examples is the Optus breach, where over 11.2 million user records were stolen. The hacker posted the data for sale on the dark web, leading to a surge in financial scams that hit both businesses and individuals. As Gavin Levinsohn, Chief Growth Officer at Eftsure, pointed out in a recent webinar, "cybercrime is not just a crime; it's a business, and data is the currency." The stolen data becomes a goldmine for cybercriminals who use it to craft targeted scams aimed at defrauding organizations.
From breach to scam: the cybercriminal's playbook
The path from a data breach to a financial scam is well-worn for cybercriminals. Once they get their hands on stolen data, they enhance and segment it much like a marketing campaign. This enriched data lets them create targeted schemes to trick their victims. For instance, with data from the Optus breach, criminals could pretend to be vendors, sending fake invoices or asking to change bank account details. These scams are often very convincing, and if an employee falls for them, the organization can suffer significant financial losses.
It's crucial for finance leaders to understand how organized these cybercriminal groups are. Ken Gamble, co-founder and executive chairman of IFW Global, a cybersecurity and investigations firm, reveals on Eftsure's On the Defense podcast that these organizations are "run like industrialized operations with HR, accounting, onboarding, and customer service departments." He adds, "They hire great talent and are highly structured, innovative, and intent on turning data into dollars." This level of sophistication means that finance leaders need to be on their toes, actively identifying and preventing scams before they hit their organizations.
This means recognizing that a single data breach can quickly turn into a targeted financial scam.
Imagine an AP officer gets an email that looks like it's from a trusted vendor, asking to update their bank account details. Without understanding the risks, the AP officer might okay the change, only to find out later that the money went to a fraudulent account. This not only leads to a direct financial loss but could also trigger legal issues and damage the company's reputation.
Why finance leaders must take action
Traditionally, cybersecurity has been the CTO or IT department's job. But now, the lines between cyber risks and financial risks are blurring. Finance leaders need to step up and take an active role in cybersecurity to protect their organizations. One key insight is the need for teamwork between finance and IT departments. "Finance leaders need to take ownership of cybersecurity strategies," says Levinsohn. "The days of leaving it all to the IT team are over."
It's not enough to just focus on preventing data breaches; finance leaders must also make sure that if a breach happens, it doesn't lead to financial losses. This calls for strong internal controls, regular staff training, and the use of technology solutions designed to prevent scams. Michael Connery, Founder and CEO of leading cyber firm Security in Depth, stresses the importance of ongoing education and awareness to minimize human error, stating, "90% of all attacks start with or include email."
Nigel Phair, director of the Institute of Cybersecurity at the University of New South Wales, further emphasizes the role of finance leaders in protecting their organizations. He notes, "Because cybercrime is all about fraud and scam, and businesses need to protect their money, the CFO is the logical individual to oversee a cybercrime strategy."
The five tenets of a cybercrime strategy
While a cybersecurity strategy focuses on locking the front door—securing the perimeter and protecting data from being breached—a cybercrime strategy is about locking the back door, ensuring that even if data is stolen, it doesn’t lead to financial losses. The distinct difference between the two lies in their areas of focus: cybersecurity is IT-driven, concentrating on preventing breaches, whereas a cybercrime strategy is finance-driven, focusing on safeguarding assets and mitigating the financial impacts of scams and fraud.
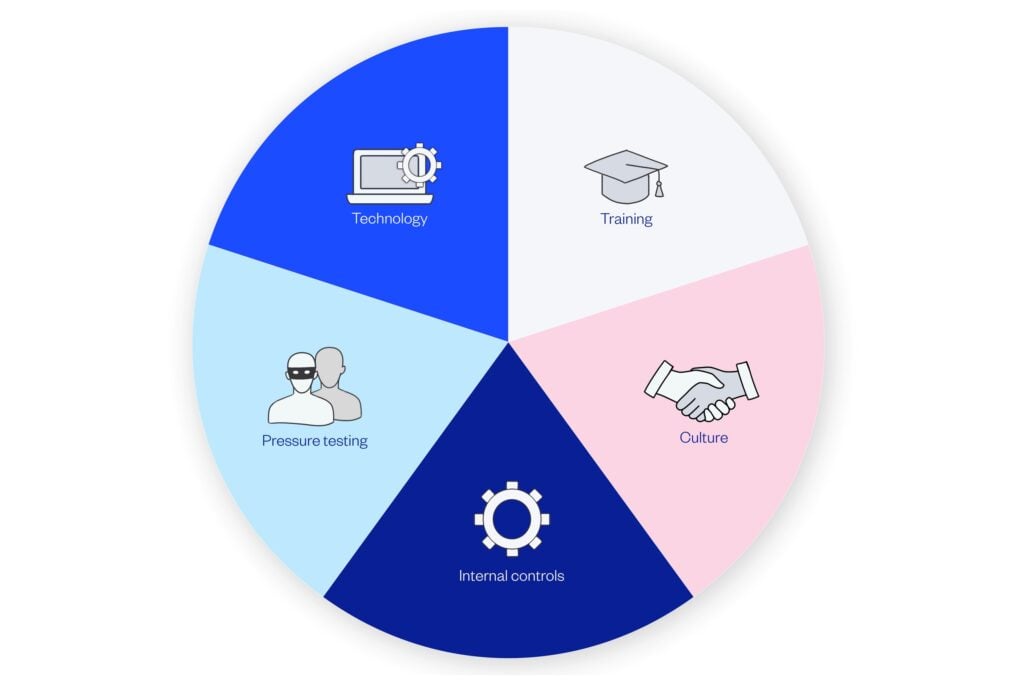
A comprehensive cybercrime strategy encompasses five key tenets:
1. Technology
Leveraging technology solutions is essential to prevent financial fraud. This includes implementing tools like Eftsure that verify payment details, monitor transactions, and alert you if something is amiss. Investing in the right technology ensures that even if criminals access your data, they can’t easily convert it into financial gain.
2. Training
Regular and ongoing staff training is crucial. Many breaches and scams occur due to human error, such as an employee clicking on a malicious link. By educating staff about the latest threats and best practices, you reduce the risk of falling victim to scams.
3. Culture
Building a strong organizational culture where employees feel safe reporting mistakes is key. When staff know they can come forward without fear of repercussions, issues can be addressed quickly before they escalate into major problems.
4. Internal controls
Robust internal controls, such as segregation of duties, regular audits, and strong vendor management practices, are vital. These controls ensure that no single point of failure exists and that suspicious activities are flagged and investigated before any damage is done.
5. Pressure testing
Just as you would conduct penetration testing for cybersecurity, pressure testing your financial systems is equally important. Simulating fraud attempts helps identify weaknesses in your processes, allowing you to strengthen them before a real attack occurs.
Steps to prevent financial scams post-breach
Preventing data breaches is the first line of defense, but finance leaders must also lessen the impact of a breach if it happens. Here are three critical steps to consider:
1. Develop a comprehensive incident response plan
A well-crafted incident response plan is essential. This plan should include predefined scenarios, communication strategies, and clear steps to take immediately following a breach. "Having an incident response plan isn't just about being prepared; it's about ensuring that your organization can respond effectively when the worst happens," said Levinsohn. For example, during the large-scale Latitude Financial breach, a swift response plan helped the company minimize damage by quickly identifying the breach, notifying affected parties, and securing the compromised data.
2. Invest in data loss prevention (DLP) tools
DLP tools help monitor and protect sensitive data, ensuring that it doesn't leave the organization without proper authorization. "Data loss prevention is a crucial layer of defense that every organization needs, especially in today's threat landscape," said Levinsohn. For instance, companies that use DLP tools can quickly detect and block unauthorized transfers of sensitive data, which can prevent the data from being used in subsequent scams.
3. Secure adequate cyber insurance
Cyber insurance is no longer optional. Finance leaders must ensure that their policy covers the specific risks their organization faces, including scams and frauds. "Without the right cyber insurance, a breach could be financially devastating," warned Levinsohn. Having the right insurance in place can mitigate the financial impact of a breach, covering costs such as legal fees, forensic investigations, and customer notifications.









