Safeguarding against insider threats, such as malicious Accounts Payable (AP) staff defrauding your organization, is a hugely challenging issue for business owners and managers. All businesses must ensure they can identify what an insider threat is, including all its various manifestations. Businesses must also ensure they are constantly protected by implementing a range of preventative measures.
According to Proofpoint, spending on insider threats is up 80% over the past 8 years. On average, organizations spend $184,548 annually on insider threat containment. In addition to this, organizations are also spending heavily on insider threat investigation and prevention.
In this blog, we’ll explore how you can protect your business against insider threats through strengthening internal controls and implementing tech solutions.
Defending Against Insider Threats
Insider Threat Training
To defend against the rise of internal threats, such as employee fraud, organizations are conducting insider threat awareness training. Every organization should be aware of these dangers and act before it’s too late.
Implementing insider threat training helps your employees identify malicious practices that may be occurring within your organization. This is crucial in enabling staff to better recognize and report suspicious behavior.
For effective insider threat training, businesses should include:
Defining what an insider threat is
The different types of insider threats
What techniques and tactics are used by malicious insiders
How to spot malicious behavior
How to report a suspicious individual
Insider threat simulations
Learning about data security on devices and networks
Why user privileges and permissions are important
Policies around threat mitigation
To achieve a significant uplift in your organization’s resilience against potential insider threats, the training program must be personalized and interactive. Such training will give staff confidence to recognize potential threats, as well as the ability to make critical decisions around reporting any suspected internal fraud.
Learn what it takes to develop a fraud awareness culture in your organization.
Establishing Policies & Procedures
Although there is no such thing as a one-size-fits-all approach to creating an anti-fraud policy, you need to have a clear outline of the prevention, detection, protection, response, and recovery steps. The Commonwealth Fraud Prevention Centre provides several warning signs to be mindful of when putting together a fraud prevention policy.
Businesses should start by clearly defining which stakeholders should collaborate to identify critical assets, security risk indicators, data sources, compliance requirements, privacy implications, communication protocols, and training curriculums.
A comprehensive insider fraud mitigation policy must outline the following:
Definitions of an insider threat, unauthorized disclosure, classified information
Asset management and governance
Employee training and awareness
Cloud data protection
Prevention and detection processes
Data security controls
Situation analysis and mitigation
Incident response service
Threat reports
Implement these 3 key fraud prevention policies.
Managing Accounts & Assigning User Roles
Another way to combat insider threats is through the implementation of restricted user roles and managing access to sensitive data.
In every business, you must assign user roles where each employee has restricted access to sensitive information and limited account privileges. Restricting privileges should be implemented at both the executive and frontline employee level according to a 'need-to-know' basis.
For example, an AP clerk may have access to low-level supplier data and reports. Whereas, the CFO will have access to all levels of supplier management data, reporting, customer setup, and more.
By implementing management procedures with documented and segregated requests and authorizations, you minimize the risk of internal threats, particularly fraud.
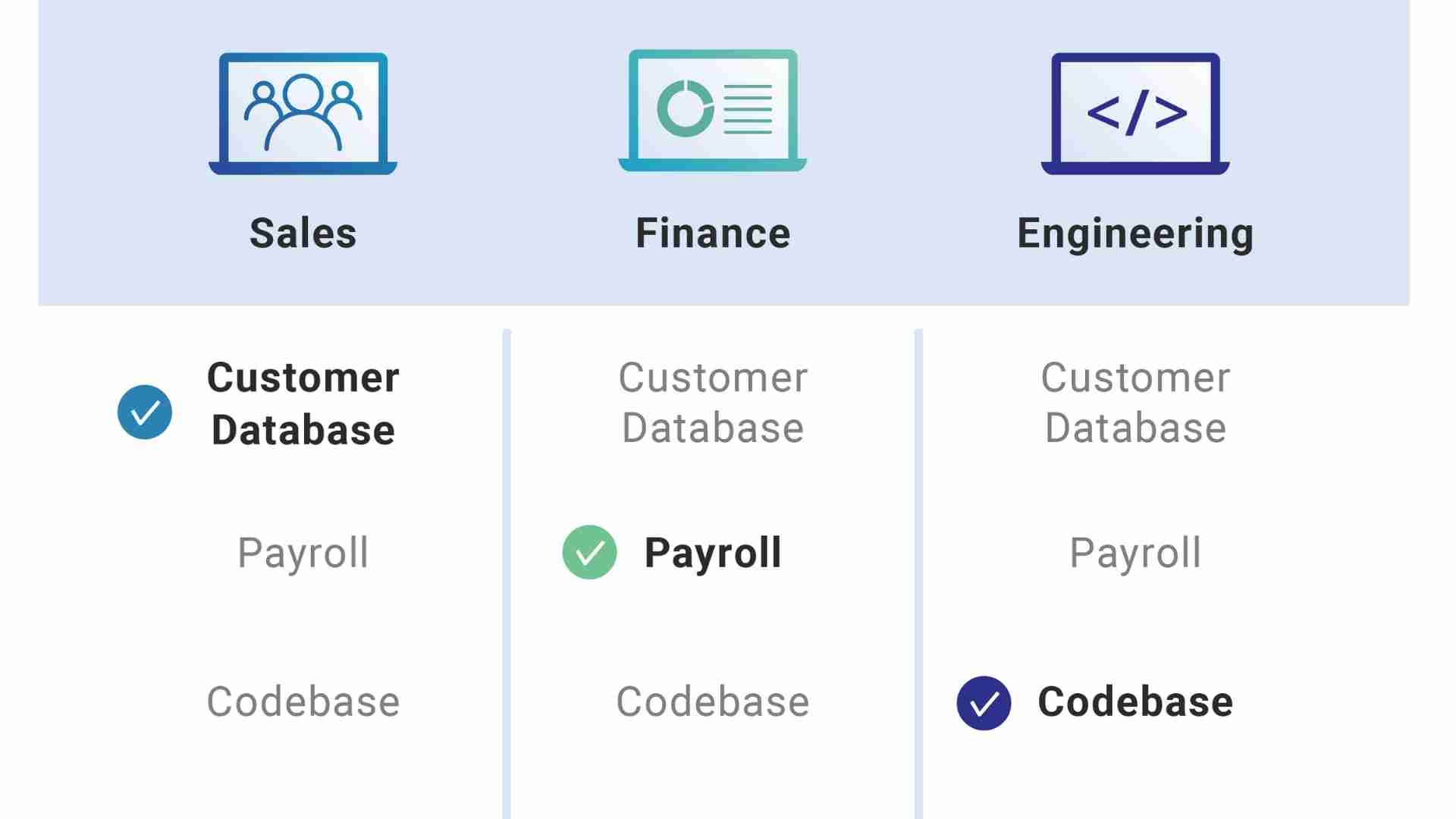
Source: Cloudflare
Implementing Password Best Practices
Every organization must ensure its network, devices, applications, and critical data are protected by strong, secure passwords. If your systems are not adequately protected, an insider could corrupt company data as a pretext for committing fraud.
In some cases, an employee might take advantage of exposed passwords in the office, guessing weak passwords, or accessing data after they depart the business.
The following password best practices can help ensure no data is stolen or corrupted:
Create strong passwords that involve a combination of numbers, special characters, lower and upper case letters
Change passwords regularly - every 2-3 months is recommended
Set passwords to expire if they are not changed
Implement a procedure whenever an employee or user leaves the organization (network access should be removed immediately)
For shared passwords, store passwords in a third-party password tool or secure password-protected location
Implement multi-factor authentication
Importantly, you should also ensure that any shared folders used by AP staff are password protected. This will allow your security team to identify who accessed the data in the folder should a breach occur.
How can Eftsure help?
Preventing insider threats, particularly internal fraud, is a huge challenge for businesses.
The threat is particularly acute when it comes to AP staff who have access to your organization's financial resources and know any loopholes in internal controls that may be exploited.
With Eftsure sitting on top of your accounting processes, you can identify and stop suspicious payments to illegitimate third parties. You also have a detailed audit trail, allowing you to investigate and take action against any malicious activities.
To learn more about Eftsure and how we can help your organization stay protected from insider threats and internal fraud, contact us today.








