CFOs, beware: cybercriminals are exploiting DocuSign's legitimate business tools to deliver fraudulent invoices directly through trusted channels.
This scheme is particularly dangerous for finance teams because it operates within standard business workflows, using DocuSign APIs, accounts, and templates. The resulting fake payment requests can look virtually indistinguishable from legitimate vendor invoices.
(Real quick: what is an API, exactly? An application programming interface is basically a secure gateway that allows different software systems to communicate and share data – in this case, it's what lets DocuSign connect with your company's other business systems, like payment processing or document management platforms.)
Breaking down the DocuSign API exploit
Based on intel from API security platform Wallarm, cybercriminals are leveraging legitimate DocuSign accounts and APIs to:
Generate authentic-looking invoices through official DocuSign channels
Deliver payment requests directly to finance teams' inboxes
Bypass standard email security filters and authentication protocols
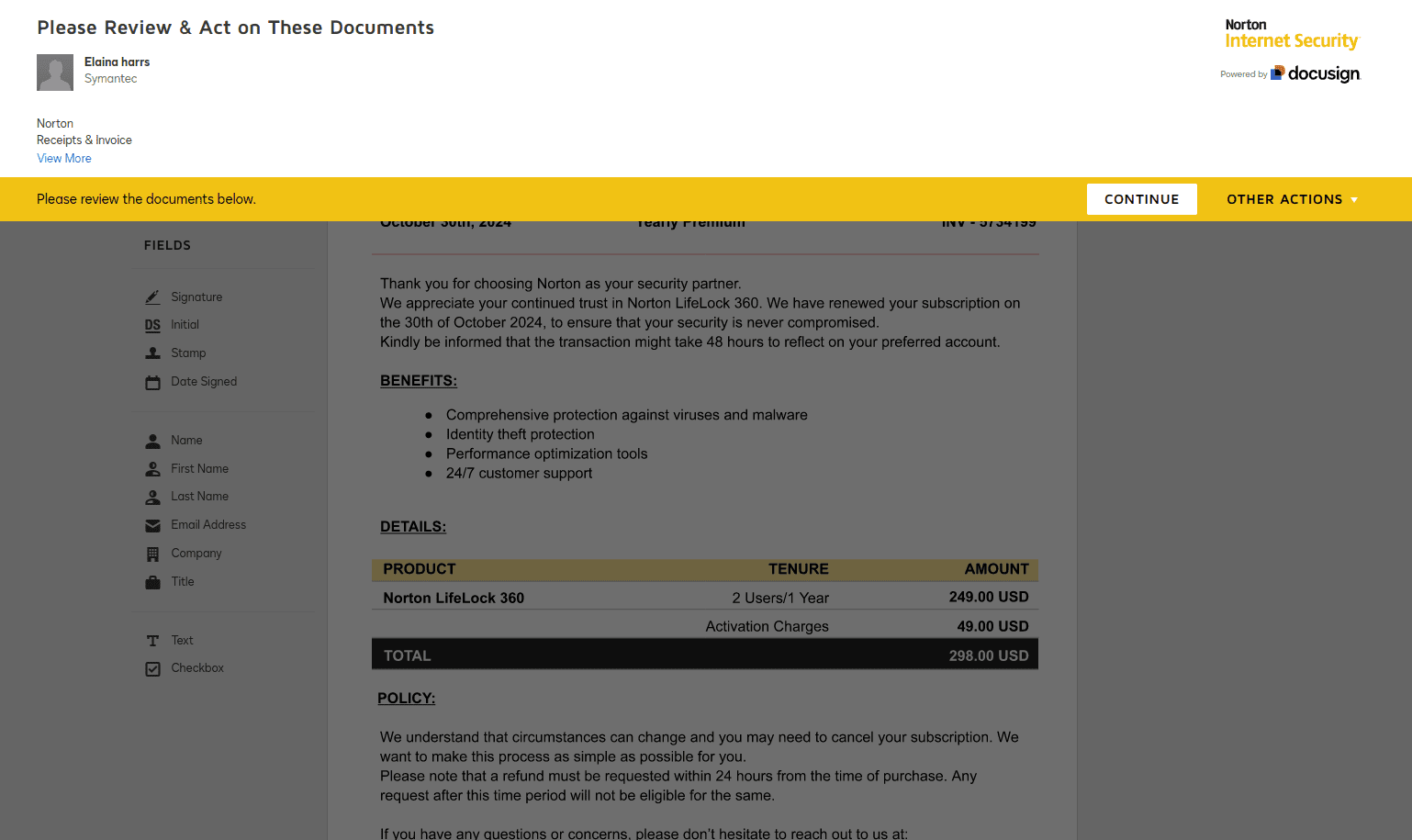
This means scammers are purchasing actual DocuSign accounts and accessing official templates, allowing them to precisely replicate known vendor branding and payment workflows.
It represents a shift away from more “obvious” scams meant to capitalize on time-poor employees who simply don’t notice major anomalies – instead, these are sophisticated operations designed to blend seamlessly into normal accounts payable processes.
Rather than using obviously fake amounts, the criminals craft invoices that closely mirror legitimate pricing while inserting subtle additional charges such as activation fees. They've also developed a concerning two-step approach: first obtaining signatures on seemingly routine documents, then leveraging these signed documents to request payments either through DocuSign or through separate channels.
Why this matters for your organization
Evidence suggests organized criminal groups are using automated systems to distribute large volumes of fraudulent invoices – systematically, at scale. This trend has shown significant growth, with DocuSign's own community forums reporting a marked increase in incidents over the past five months.
There are unique risks to financial operations.
1. Circumvention of standard controls
Traditional email security measures cannot detect these threats
The invoices appear within legitimate DocuSign workflows
No suspicious links or attachments trigger security alerts
2. Enhanced credibility
Attackers leverage DocuSign's trusted brand reputation
Fraudulent invoices mirror legitimate vendor documentation
Payment instructions appear through official channels
3. Targeting of finance personnel
Attacks specifically target accounts payable workflows
Fraudulent requests blend with legitimate invoice processing
Time pressure and volume of transactions increase vulnerability
Immediate actions
Review and enhance payment verification protocols
Implement mandatory secondary verification for all DocuSign-initiated payment requests
Cross-reference vendor payment details against established records
System changes
Update accounts payable procedures to include DocuSign-specific verification steps
Enhance staff training to cover sophisticated payment fraud techniques
Establish clear escalation protocols for suspicious payment requests
Strategic considerations
Review internal controls around electronic payment authorizations
Implement additional verification steps for high-value transactions
Evaluate the need for specialized training for finance team members, especially those who are closest to high-value transactions and approvals
Traditional security measures and training programs may need updating to address this specific risk vector, but it’s also just one of many potential gaps between IT and finance teams that scammers are constantly looking to exploit. Download our free anti-cybercrime guide to understand these gaps and protect your business.







