Each month, the team at Eftsure monitors the headlines for the latest Accounts Payable security news. We bring you all the essential learnings, so your Accounts Payable team can stay secure.
Don't Rely on the Banks to Stop Scams!
It has emerged that the Australian banks have been actively lobbying government regulators to avoid taking full responsibility for refunding victims of payment redirection scams, such as Business Email Compromise.
Despite the fact that such scams are directly caused due to a verification gap in the banking system, whereby the Account Name is not aligned to either the BSB or Account Number when an EFT payment is processed, the banks argue that those sending payments must take responsibility for ensuring the payment details are legitimate and accurate. The banks argue that they should not be required to help protect victims due to the risk of moral hazard, in which banking customers may act carelessly when processing online payments if they know the banks will protect them if the payment is fraudulent.
With present scam rates escalating exponentially, and sophisticated scammers finding new ways to deceive Accounts Payable staff, a coordinated approach between the banks, regulators, and Eftsure has never been more important.
The lesson from these revelations is clear - do not wait for the banks to protect you.
With Eftsure sitting on top of your accounting processes, you can benefit from immediate protection from such scams. Over 850 Australian organisations have already made the decision to be part of the Eftsure community - make sure your organisation joins too!
Learn how Eftsure has your back.
Beware – Excel Attachments Spreading Malware
As finance and accounting professionals, we seem to spend our whole lives buried deep in Excel spreadsheets.
Cybercriminals know this and are actively exploiting Excel files as a vehicle to distribute malware to unsuspecting victims. Given their extensive use of Excel, Accounts Payable teams are particularly at risk.
According to the latest Global Threat Report, email threats increased by 12.5% in 2021 compared to the previous year. Many of these email attacks included the distribution of malicious software, or malware, via attachments. Malware comes in a wide variety of formats and can give cybercriminals full access to your computer systems, including email accounts. It can pave the way for the attackers to steal your confidential corporate, financial, and customer data. You could even find yourself subjected to a ransomware attack in which you are locked out of all your systems until paying the attackers a hefty ransom.
Emails containing malware attachments increased over 2021, peaking at over a staggering 25 million sent in the month of November alone.
When it comes to the type of attachments containing malware, .XLS files were most ubiquitous.
.XLS files are an older version of Microsoft Excel and support the use of Macros, which are automated tasks that run when the file is opened. Hackers can embed malware within the Macros, so when the victim opens an .XLS file, the malicious code is automatically executed.
A more secure alternative is to use .XLSX files instead of .XLS files.
.XLSX is a more updated version of Excel that only runs on Excel 2007 or later versions. The benefit of .XLSX is that it does not support the use of Macros.
By ensuring that your entire Accounts Payable team, as well as others in your organisation, use .XLSX files, you can help mitigate the risk of dangerous Excel attachments infecting your systems with malware.
Executive MS Office Accounts Taken Over by OAuth Apps
The dark web is awash with stolen passwords that are available for purchase by any petty criminal.
And with most people re-using the same password across multiple systems, hackers have plenty of opportunities to break into applications to engage in financially motivated cybercrime. Even more concerning is the fact that one application often needs to allow multiple third-party applications access to its data for a range of business purposes.
This interconnectivity between applications is essential for efficient work practices. However, it also means that once a hacker gains access to one application using a stolen password, they can pivot to access other applications as well.
That’s why OAuth was developed.
With OAuth, one application can authenticate a third-party application and grant access to its data through the use of a token instead of a password. By using a token, it helps limit the ability of hackers with stolen passwords from accessing the application.
However, as we know, cybercriminals are always adapting their nefarious tactics. In the latest news, they are also finding ways to circumvent OAuth.
‘OiVaVoii’ is the name ascribed to a new type of attack that targets company executives using malicious OAuth applications. It is resulting in criminals taking over executives’ Microsoft Office accounts, giving the attackers full access to their mailboxes so they can launch a range of attacks, including Business Email Compromise.
The attackers are using the OAuth applications to send permission requests to unsuspecting executives in targeted organisations, who click “Accept,” as the request looks legitimate.
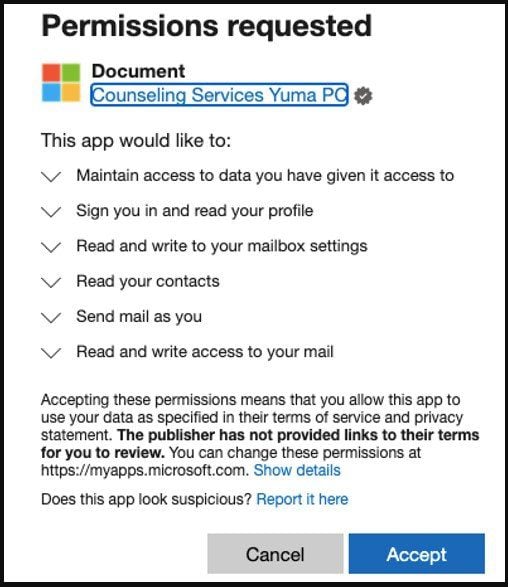
When the targeted executive hits the “Accept” button, the criminals use the OAuth token to access and send emails from their accounts to other employees within the same organisation, often with payment instructions.
Accounts Payable staff may be deceived into thinking such an email is legitimate and action the payment. It is critical that staff are aware that this attack vector is currently active and that any payment instructions should be carefully scrutinised, even if they come from an executive’s legitimate email address.
BEC Scammers Arrested
In a rare piece of good news, Nigerian police, in conjunction with Interpol, have put a stop to one Business Email Compromise (BEC) syndicate by arresting 11 associated individuals.
It is believed the group, known as Silver Terrier, was responsible for over 50,000 BEC attacks worldwide and had been eluding law enforcement for over five years.
A laptop belonging to one of those arrested allegedly contained in excess of 800,000 usernames and passwords belonging to potential victim organisations.
Another member of the syndicate was found to be monitoring communications in target organisations, presumably as part of the reconnaissance efforts that usually precede a BEC attack.
The operation, known as “Falcon II,” sends a clear message that cybercrime will have serious repercussions for those involved in BEC fraud, according to Craig Jones, Interpol's director of cybercrime.
However, given the exponential rise in BEC attacks in recent years, it is highly likely there are many other criminal syndicates currently operating. All organisations must embrace systems that prevent BEC crime, because despite these recent arrests, there is no indication the threat is disappearing.
Essential Procure-to-Pay Checklist for AP Teams
Secure your Accounts Payable process with our 8-step Checklist.
Following these 8 steps throughout the Procure-to-Pay lifecycle will help protect your organisation from falling victim to invoice fraud, as well as erroneous payments.