As the financial industry continues to evolve, so do the regulations governing it. One of those regulations has generated significant attention in recent years – CPS 234, a directive from the Australian Prudential Regulation Authority (APRA) aimed at improving the resilience of the financial sector against cyber threats. Designed to help businesses better manage financial risk, CPS 234 can be a daunting prospect for those responsible for ensuring compliance.
But fear not – in this guide, we'll take a closer look at CPS 234 and provide strategies for staying compliant to help ensure your business remains secure and resilient.
What is the APRA CPS 234 regulation?
APRA CPS 234 is a regulation introduced by the Australian Prudential Regulation Authority (APRA) to improve the resilience of APRA-regulated entities against cybersecurity threats. This regulation was introduced in 2019 and applies to all APRA-regulated entities, including:
Financial institutions like Authorised deposit-taking institutions (ADIs), foreign ADIs, and non-operating holding companies authorised under the Banking Act (authorised banking NOHCs)
General insurance companies, including Category C insurers, non-operating holding companies authorised under the Insurance Act and parent entities of Level 2 insurance groups
Life insurance companies including friendly societies, eligible foreign life insurance companies (EFLICs) and non-operating holding companies registered under the Life Insurance ACT
Private health insurance companies registered under the PHIPS Act (registered life NOHCs)
Superannuation funds
Organisations licensed under the RSE based on the Australian SIS Act
The primary objective of CPS 234 is to ensure that APRA-regulated entities maintain information security in a highly challenging and rapidly changing environment. It aims to do so by outlining clear cybersecurity requirements that APRA-regulated entities must adhere to.
CPS 234 requires APRA-regulated entities to maintain an information security capability commensurate with the size and complexity of their operations. It also requires them to notify APRA of any significant cybersecurity breaches, maintain information on their information security policies and practices, and demonstrate compliance with the regulation.
Why is this important for your businesses? Well, APRA-regulated entities that fall under the CPS 234 must comply with the regulation. Plus, by adhering to the regulation, organisations can maintain a strong cybersecurity posture to keep up with cyberattacks that are increasing in frequency, sophistication and impact – which are all increasing even according to the under-reported numbers we’ve seen in the most recent Scamwatch report.
To comply with CPS 234, businesses must have a clear understanding of their information and financial assets, the threats and vulnerabilities according to those assets, as well as the potential consequences of a cybersecurity incident. They must also have appropriate information security controls in place, including policies and procedures for incident management, access management and vulnerability management.
CPS 234 also requires APRA-regulated entities to maintain a cybersecurity resilience posture and regularly test their information security controls to ensure their effectiveness. They must also have a system in place to review and assess the effectiveness of their cybersecurity practices regularly.
APRA CPS 234 checklist: key requirements and obligations
Businesses that fall under the scope of the APRA CPS 234 regulation must meet several key requirements and obligations to ensure compliance. We’ve outlined them below.
Identifying financial risks
To comply with CPS 234, businesses must first identify the financial risks they face.
This includes risks associated with the threat landscape and broader risks such as market volatility, regulatory changes and operational risks. By conducting a thorough risk assessment, businesses can gain a better understanding of the potential financial risks they face and how they can mitigate them. For example, businesses may face the following financial risks:
Cybersecurity risk. Compliance with CPS 234 can assist organisations to combat cybersecurity risks, such as data breaches, which can result in financial losses from business interruption, legal fees, and reputational damage.
Regulatory risk. Organisations can avoid regulatory risk by ensuring that they meet the CPS requirements set out in the regulation. This will help them prevent fines, penalties, or other legal consequences that can impact their finances. In addition, the APRA can conduct investigations, direct entities to take or refrain from particular actions, impose conditions or ban individuals from working in an APRA-regulated industry. For more information, check out APRA’s enforcement policy.
Business continuity risk. Compliance with CPS 234 can help organisations better prepare for business continuity risks, such as cyberattacks or other cybersecurity incidents that could disrupt operations. This can help minimise financial losses resulting from downtime or lost revenue.
Reputation risk. Compliance with CPS 234 can help organisations protect against reputation risk by demonstrating their commitment to information security and protecting against potential data breaches. This can help maintain customer trust and loyalty and avoid financial losses from damaging the organisation's brand or image.
Six ways to manage financial risk while remaining compliant
To manage financial risks while remaining compliant with CPS 234, leaders need a comprehensive approach that addresses the various risks and requirements outlined in the regulation. This might involve implementing strategies around new policies and procedures, investing in new security technology or training staff to better manage cyber risks.
By taking a proactive approach to risk management, businesses can not only meet the requirements of the CPS 234 regulation but also improve their overall resilience and cybersecurity. Here are some ways to do that:
Develop a risk management framework. Organisations should develop a comprehensive risk management framework that identifies, assesses, and manages financial risks related to information security. This framework should be based on the requirements of CPS 234 and should include policies, procedures, and guidelines for managing risk.
Conduct regular risk assessments. Regular risk assessments can help organisations identify potential financial risks related to information security and prioritise mitigation efforts. These assessments should be based on the organisation's risk management framework and should be conducted regularly.
Implement appropriate controls. Organisations should implement appropriate security and internal controls to mitigate financial risks related to information security. These controls should be based on the results of risk assessments and should be aligned with the requirements of CPS 234.
Establish incident response plans. Organisations should have well-defined incident response plans in place to mitigate financial losses resulting from information security incidents. These plans should be regularly tested and updated to ensure their effectiveness. We provide a comprehensive business email compromise (BEC) incident response guide to mitigate the risk of exponential BEC attacks.
Engage in regular training and awareness. Regular fortnightly or monthly training and awareness programs can help organisations ensure that their employees understand the risks associated with information security and are equipped to manage these risks effectively. Training is most effective when they are tailored and interactive for optimal results, this can help prevent financial losses resulting from human error or negligence. We provide a guideline on how to create a fraud awareness culture.
Regularly review and update policies and procedures. Policies and procedures should be regularly reviewed and updated to ensure that they remain aligned with the requirements of CPS 234 and are effective in managing financial risks related to information security. Cybercriminals are constantly evolving and so should your policies and procedures.
By implementing these strategies, organisations can effectively manage financial risks related to information security while remaining compliant with CPS 234. This can help ensure the long-term stability and success of the organisation.
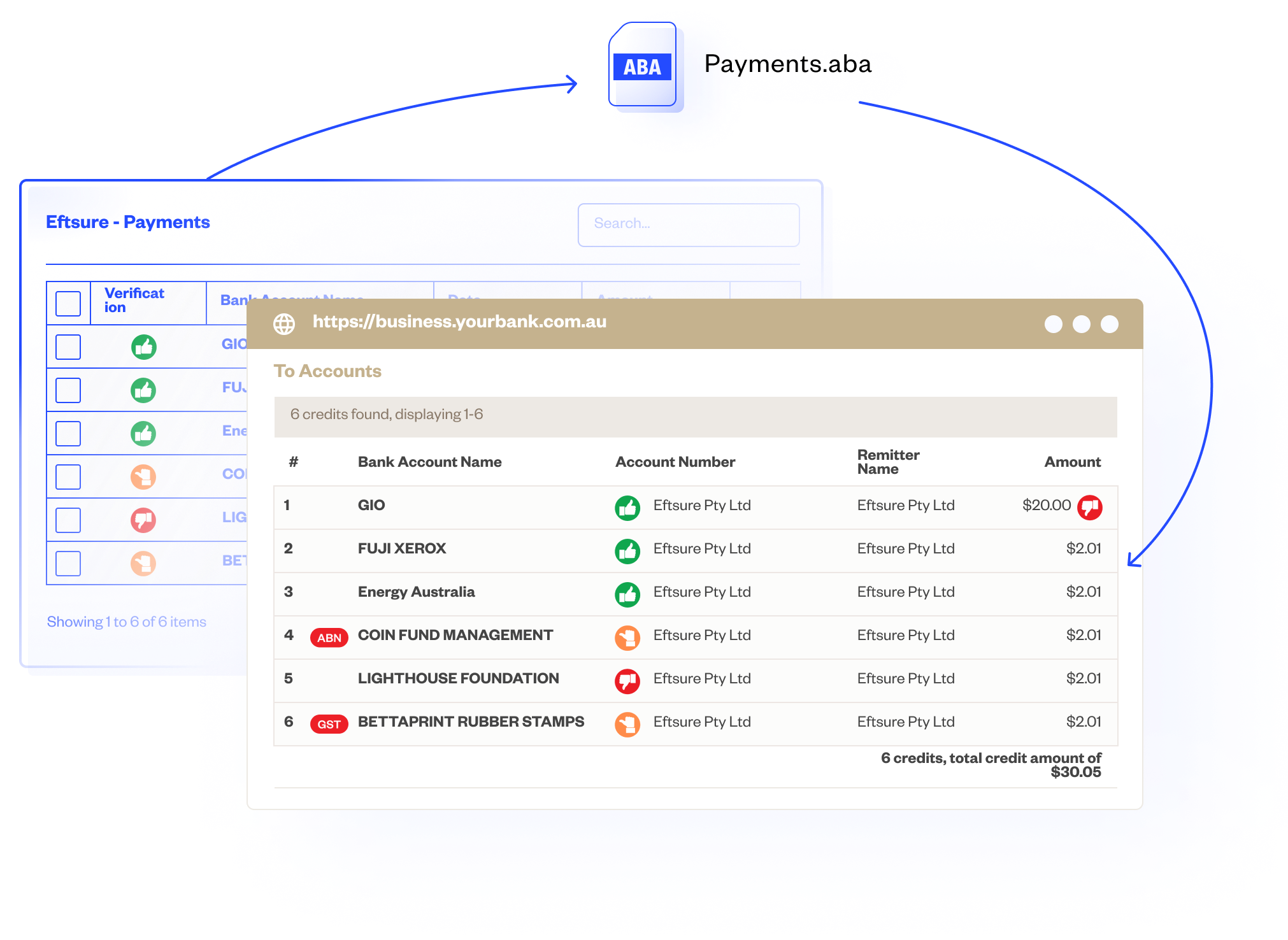
Improve cyber resilience with Eftsure
The release of CPS 234 aims to minimise the likelihood and impact of information security incidents on the confidentially, integrity or availability of information assets.
Complying with this regulation can enhance your business's cybersecurity stance by providing a structured framework for managing information security risks, staying up-to-date with emerging threats and best practices, and building trust with customers and stakeholders.
Organisations can take their cybersecurity strategy to the next level by incorporating strong, technology-enabled defences like Eftsure’s payment protection, helping to ensure long-term stability and cyber resilience.
Our solution allows your organisation to align with the CPS 234 regulation by verifying Electronic Funds Transfer (EFT) when paying suppliers. Through our real-time thumb alerts, you can identify each outgoing payment and ensure it is being paid to the intended legitimate third party. This assures your AP team that they are not being defrauded when processing EFT payments, allowing you to manage financial risk.
Contact Eftsure today for a full demonstration of how we can mitigate financial risk.
Don’t want to let cybercriminals keep the upper hand? Protect your organisation today by building a strong policy around your segregation of duties.