Sydney hospital loses $2 million in alleged BEC fraud
A Sydney hospital lost $2M in a BEC scam. Learn how to protect your business with MFA, email authentication, and robust financial controls.
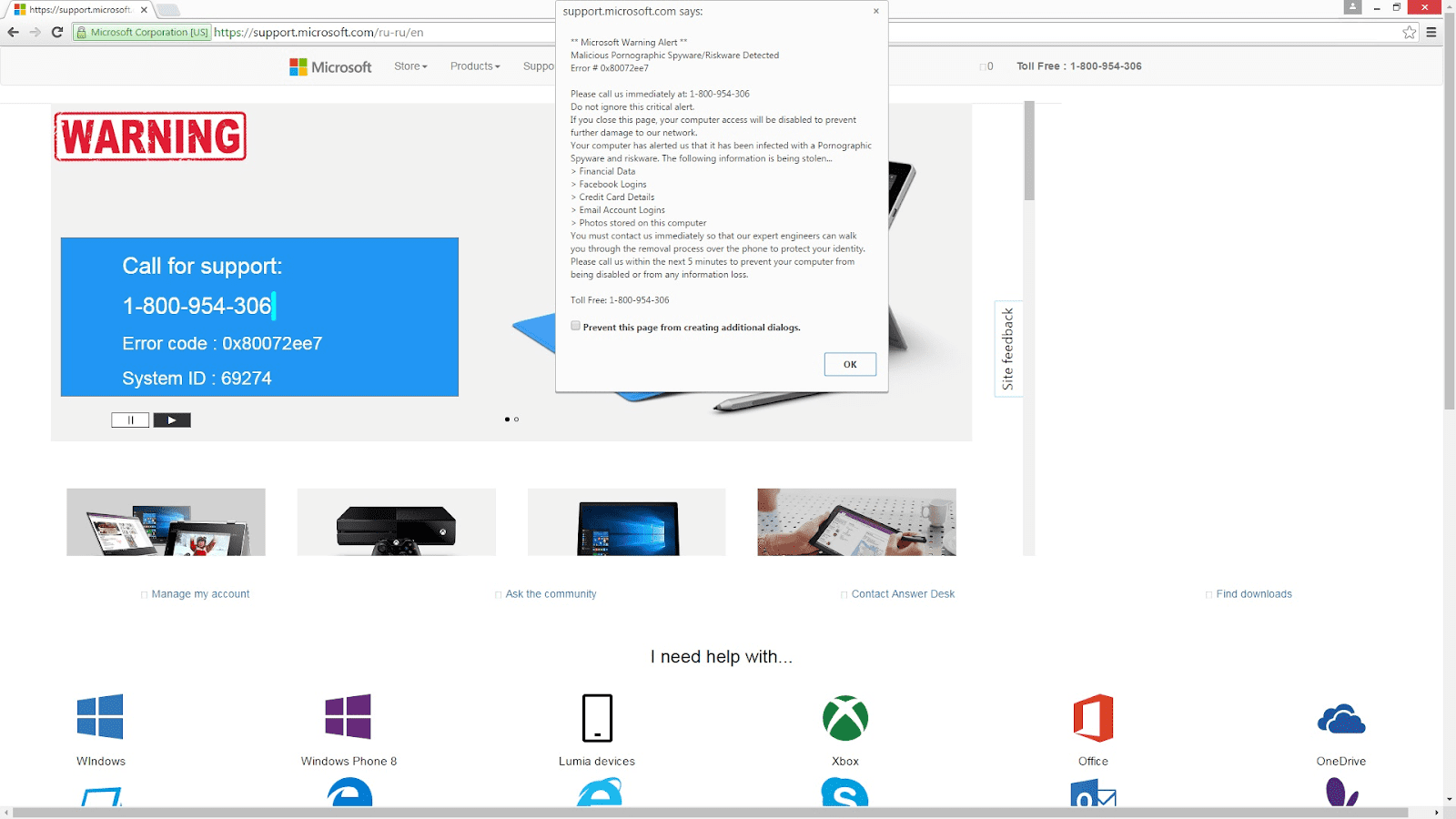
It starts with an innocuous call or pop-up claiming your computer has a problem but ends in drained bank accounts and unrecovered funds.
Unwary Australians suffered remote access scam losses amounting to over $15 million last year alone. And the problem is on the rise.
According to the most recent figures from the ACCC, remote access scam losses saw a staggering 52% increase in the first quarter of 2024 compared to the previous quarter. The average cost of remote access scams also increased this quarter by 57% to $17,943.
As fraudsters deploy increasingly sophisticated social engineering tactics, AP teams need bulletproof payment verification processes to safeguard against significant financial losses.
Remote access scams are a type of cybercrime that occurs when a fraudster gains control of a victim’s computer or device by tricking them into allowing remote access, enabling the fraudster to steal money from the victim.
These fraudsters use scare tactics to manipulate victims into compromising their devices and accounts. Common techniques include:
Once deceived, the victim is instructed to download remote desktop software, such as TeamViewer or LogMeIn, enabling the fraudster complete access to their device.
With full control, the fraudster can run programs that appear harmful to the victim’s device but are innocuous. Playing into this fear, they now have a few options to steal from the victim:
Remote access scammers use a specific approach. To avoid falling victim to remote access scams, AP teams need to know exactly what to look for:
Remote access scammers are adopting more realistic techniques. They sound professional and even use the same software as the actual tech support teams they’re duping. Relying on human judgment to keep these scams at bay is no longer enough on its own. Your AP team needs solid verification processes and controls to effectively prevent scams.
Without effective protection mechanisms in place, your business is left open to several risks:
AP teams must follow a strict process for verifying a supplier’s identity and banking details or risk sending payments to fraudsters impersonating legitimate businesses. Failure to implement or follow these processes can result in funds being stolen outright or requiring a costly and time-consuming recovery. Take, for instance, the finance worker who was fooled by a deepfake video call scam to the tune of $39m.
Once a fraudster successfully impersonates a legitimate supplier, they can easily access internal payment systems and financial accounts, enabling further theft and misuse.
If suppliers aren’t scrutinised sufficiently, your businesses could unwittingly facilitate money laundering activities if payments are sent to shell companies or illicit fronts without oversight.
Misdirected payments resulting from a lack of adequate due diligence cause severe reputational damage. Defrauded companies end up as headlines at a cost. Their credibility takes a hit among shareholders and customers, who quickly lose trust.
Many industries have know-your-customer (KYC) and anti-money laundering requirements that mandate supplier due diligence. Companies that lack sufficient verification processes and controls expose themselves to potential fines and penalties on top of the financial loss caused by a scam.
Fraudulent payments, especially recurring ones, lead to cash flow issues and delayed payments to real suppliers, ultimately disrupting business operations.
The only way AP teams can ensure maximum protection against payment scams is to check payment details every time they pay suppliers. You need rigorous verification processes and controls to prevent fraudsters from infiltrating payment systems.
A Sydney hospital lost $2M in a BEC scam. Learn how to protect your business with MFA, email authentication, and robust financial controls.
CFOs, beware: cybercriminals are exploiting DocuSign’s legitimate business tools to deliver fraudulent invoices directly through trusted channels. This scheme is particularly dangerous …
Because LinkedIn is used as a professional networking platform, account holders don’t use the same caution as they would on Facebook or …
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.