What is spear phishing?
Spear phishing is a targeted cyberattack where personalised emails are crafted and then sent to deceive specific individuals within organisations.
Social media phishing involves scammers using social media platforms to deceive users into sharing sensitive information.
With more than 5 billion social media users that each visit an average of 6.7 platforms every month, the amount of information criminals can exploit for such attacks is immense.
Fundamental to social media phishing is the idea of social engineering. This practice refers to manipulating human behaviour such that victims act in ways that compromise their security.
To achieve this, various tactics exploit trust, social norms and emotions to deceive individuals. Fraudsters also incorporate personal information the victim has shared on social media to make the attack more convincing.
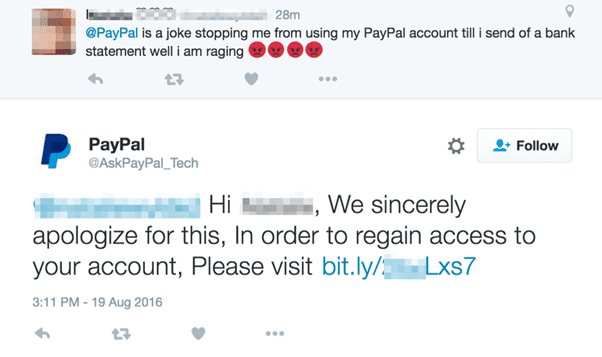
For example, an attacker may impersonate someone the victim knows by creating a fake profile in the contact’s name or hacking into their account. Then, they exploit the trust and familiarity of the contact when messaging the victim.
These messages invariably contain malicious links or requests to provide sensitive information such as passwords or bank account details. Since the request appears to come from someone the victim knows, they are more likely to comply.
The tactics attackers use on social media are diverse, but most share a common objective: to exploit human behaviour for personal gain.
Here, fraudsters create profiles that mimic legitimate brands or individuals and entice users to click on links or enter their credentials on fake websites. To build credibility, both the profile and website may incorporate logos and branding from reputable companies.
In 2022, for example, 45% of individuals who lost money to social media scams were online shoppers. These individuals had purchased items via fake social media profiles that impersonated real brands.
Fake job offers alert victims to the presence of fictitious employment opportunities.
This is a particularly deceptive and pernicious form of social media phishing because it often takes advantage of economic hardship.
Scammers typically have two aims when employing this tactic:
Seemingly harmless quizzes that ask social media users for personal information may also be a phishing scam.
These questions – which are identical to those used by banks for identity verification – may prompt the individual to reveal the make of their first car or the name of their pet.
Answers are then combined with other stolen information and used to breach bank and email accounts.
In a brand ambassador scam, influencers are approached by what appear to be legitimate brands. The brand typically offers an ambassador deal in exchange for the influencer’s personal information.
Other influencers will be asked to buy the product upfront with a discount code and then promote it on their accounts. However, neither the brand nor the product exists.
For the victims of social media phishing attacks, impacts include identity theft and emotional distress.
Financial loss is also common and widespread. Between January 2021 and June 2023, the FTC reported that financial losses to social media scams were $2.7 billion. However, the body conceded that the actual cost was much higher since many instances of fraud are not reported.
The impact on businesses can also be substantial:
To conclude, let’s look at two ways businesses and employees can protect themselves from social media phishing.
Employees are often on the frontline of social media cyberattacks, so they must be trained on how to recognise a phishing attempt before it has a chance to cause damage.
Phishing awareness programs can help employees spot unusual links or requests for sensitive information. Employees should also be aware of social engineering and its power as a tool for psychological manipulation.
Social media habits are also important. Employees should be wary of allowing third-party apps on social media accounts as these provide another entry point for cybercriminals.
Similarly, individuals should never save their username and password on a public device and always log out after each session.
Multi-factor authentication is one of the easiest (and most effective) ways to add extra security to social media accounts. MFA blocks up to 99.9% of all automated cyberattacks and reduces the number of account hacks by 50%.
Note, however, that not every MFA technique is effective at combatting phishing attacks. Some techniques are susceptible to push bombing, for example, where attackers flood victims with numerous fraudulent requests to authenticate until they comply.
Authenticator apps are a relatively cheap and easy form of MFA, but to avoid push bombing, it is important to find apps that utilise rolling codes and not push notifications.
Otherwise, the most effective defence is a hardware-based security key such as WebAuthn and FIDO2. These keys combine the security of a physical token with biometric verification.
Summary:
Spear phishing is a targeted cyberattack where personalised emails are crafted and then sent to deceive specific individuals within organisations.
Email phishing occurs when malicious actors pose as reputable entities and send fraudulent emails to deceive recipients.
Money laundering detection is the process by which financial institutions (and other entities) identify and prevent the movement of illicit funds.
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.