What Can Scammers Do with Your Phone Number?
When cell phones first became popular, no one thought they’d become what they are today. For the first few years, it was …
A drop address is an address used for the receival of items that conceals the identity of the recipient.
Drop addresses are used in several legitimate scenarios. However, their relative anonymity means criminals can also exploit them to commit fraud.
Since there is no direct link between the recipient and the address to which the items are shipped, it is difficult for authorities to identify the perpetrators.
Let’s start with a few examples of how a drop address can be used legitimately.
Drop addresses are used in remote areas where there is no postal service or other form of reliable delivery.
In this case, residents utilise an address in a nearby town or city to collect their packages and mail. This may be a residential or business address or a PO box.
Some companies offer parcel collection services where items are shipped to their address (the drop address). Once there, the recipient collects the items from a parcel locker at their convenience.
This type of drop address is useful for those who are not at home during regular delivery hours.
Businesses may also utilise drop addresses, especially those that:
The process starts with the selection of a suitable location.
For fraudsters, an ideal drop address is:
Once a suitable property has been identified, criminals may use a drop address to receive:
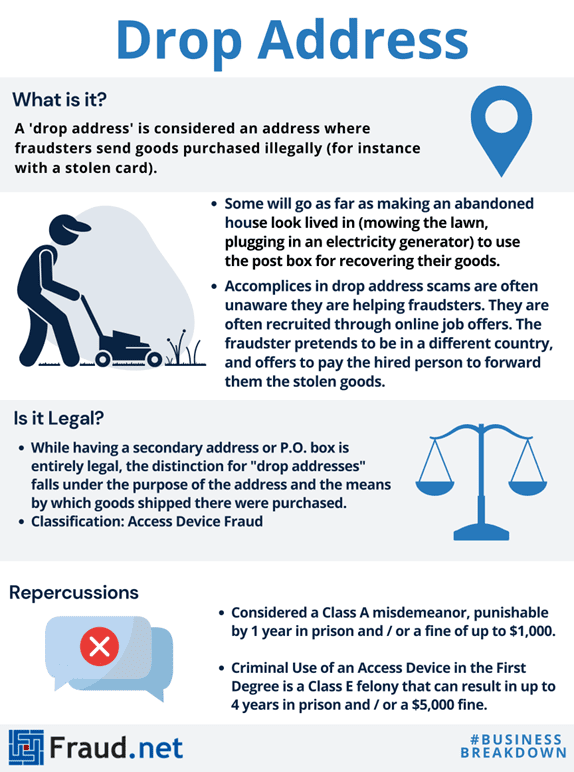
Drop addresses are also a core component of reshipping scams.
In this context, criminals use stolen credit cards or bank accounts to purchase goods online. The goods are then sent to the address of an accomplice who repackages the goods – often in exchange for payment – and ships them to a depot or another intermediary.
From there, the goods are shipped once more to the criminal.
Reshipping scams recruit accomplices with fake work-from-home opportunities, with the Better Business Bureau reporting that 65% of scam job ads posted online were related to re-shipping.
While most accomplices are unaware of their participation in the scam, they are often arrested once the stolen card or account is linked to their address.
Various best practices help prevent (or at least reduce) criminal use of a drop address.
For eCommerce businesses, it is important to note that such use is a symptom of some type of fraud. To that end, specialised tools help identify specific behaviours indicative of fraudulent activity.
These include:
Merchants and financial institutions can also do their part to reduce drop address-related fraud. The absence of robust verification processes is a primary contributor to this problem, so with that in mind, here are two more corrective measures to consider:
In summary:
When cell phones first became popular, no one thought they’d become what they are today. For the first few years, it was …
When Mr. Beauchamp watched a video of Elon Musk – the world’s richest man – recommend a certain investment platform to make …
Your company delivered the good or service it promised to a client and now it’s time to collect the funds owed to …
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.