What Can Scammers Do with Your Phone Number?
When cell phones first became popular, no one thought they’d become what they are today. For the first few years, it was …
A phishing kit (sometimes referred to as a “phishkit”) is a bundled set of tools used to create convincing fake websites that steal login credentials and other sensitive data.
These kits are widely available on the dark web and come complete with scripts, cloned pages and setup instructions. Many are plug-and-play and require little more than a basic understanding of how to upload files to a server.
A phishing kit (sometimes referred to as a “phishkit”) is a bundled set of tools used to create convincing fake websites that steal login credentials and other sensitive data.
These kits are widely available on the dark web and come complete with scripts, cloned pages and setup instructions. Many are plug-and-play and require little more than a basic understanding of how to upload files to a server.
What makes phishing kits especially dangerous isn’t just the technology and low barrier to entry. It’s how they exploit behavioural shortcuts that accounts payable teams rely on daily.
Phishing kits are superb imitators and can often mimic legitimate websites down to the pixel. An attacker can spin up a copy of a vendor portal, Office365 login page or finance dashboard in minutes.
At the very least, most kits include:
Advanced phishing kits have extra capabilities. Some offer dynamic content generation and adjust based on a user’s IP address, device or operating system.
Some use bots to alert the attacker the moment a victim enters their credentials, while others include domain registration services and custom email campaigns designed to bypass cybersecurity protocols.
Names, emails, addresses and passwords tend to be the four most popular forms of data targeted using spear-phishing kits. This makes them well-suited to various cybersecurity exploits such as:
Irrespective of the exploit, what many write-ups gloss over is that phishing kits are not just designed to fool systems. They’re built to blend into everyday workflows.
Accounts payable teams are typically efficient, responsive and deadline-driven. These qualities are desirable—but they can also be a vulnerability.
To better understand this, consider that criminals count on specific behavioural patterns in AP departments:
A phishing campaign targeting AP might start with a well-written email posing as a vendor follow-up or finance system notification.
The message includes a link to a phishing site disguised as a portal to review or approve invoices. If the site looks familiar, the timing aligns with an existing task and the user is under pressure, the chance of a successful breach increases.
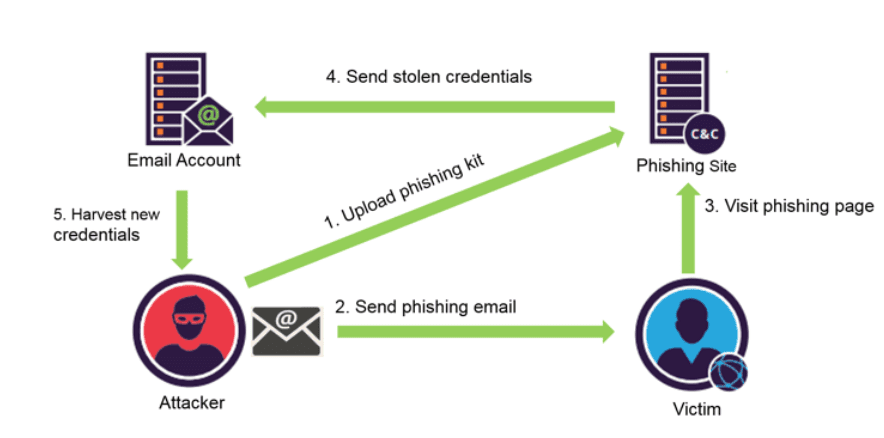
Phishing kits and their role in the infection cycle of a phishing attack (Source: Cyble)
Once an attacker has valid login credentials, they don’t rush. They observe.
Many phishing attempts aimed at AP are part of longer, more calculated phishing campaigns. The attacker could choose to sit inside the system for days or weeks where they watch for patterns across vendor payments, invoice approval timelines and specific internal contacts.
From there, they may:
Because these actions don’t disrupt daily operations, they’re often missed until a vendor reports non-payment or the funds have disappeared.
This kind of fraud is subtle and scalable. Indeed, one phishing kit can be used across dozens of organisations with only minor tweaks needed to target different finance systems, domains, platforms, workflow cues and various region-specific nuances.
Kits can also be deployed repeatedly on different servers, which means a single phishing campaign may have multiple simultaneous deployments.
Traditional security measures often fail to stop these scams. Email filters may block obvious spam, but new phishing kits rotate domains and mimic trusted brands with legitimate HTTPS certificates.
Some even block scans from security teams with IP filtering or browser user agent detection. And because phishing kits use valid credentials and not malware, the unauthorised access doesn’t trip alarms.
Worse, phishing as a service (PhaaS) is on the increase. Rather than build their own kits, attackers can now rent them. They choose a target type (like a finance system) and receive templates, deployment scripts and even support for a low fee or a cut of any proceeds.
It’s this commercial-level access that’s driving the broader trend of low-effort, high-reward phishing attacks. The sophistication of attacks is also on the rise, with one analysis of dark web marketplaces finding that almost 75% of phishing kits referenced artificial intelligence in the description.
While there’s no silver bullet, understanding how phishing kits work gives security teams a clearer path forward. Remember that the effectiveness of these kits is driven by their ability to mimic how people normally work.
Beyond the usual tech stack, security teams should:
Another critical measure involves tracking what type of login pages are commonly used and how users access them. If an AP team logs in through email prompts 80% of the time, that’s a known pathway for phishing kits to exploit.
A technical fix may block malicious sites, but adding friction to the way people work is more effective. Friction, in this context, could mean flagging vendor changes for secondary approval or displaying a brief verification prompt before payment details are updated.
These relatively minor adjustments can disrupt the smooth user flow that phishing kits rely on. They don’t slow down work. They simply ask staff to pause, think, and buy themselves just enough time to spot something suspicious.
When cell phones first became popular, no one thought they’d become what they are today. For the first few years, it was …
When Mr. Beauchamp watched a video of Elon Musk – the world’s richest man – recommend a certain investment platform to make …
Your company delivered the good or service it promised to a client and now it’s time to collect the funds owed to …
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.