Payment Security 101
Learn about payment fraud and how to prevent it
A new generation of cyber-threats calls for a new approach to protecting your organisation’s finances. That’s why we’ve created a guide for CFOs and financial leaders to help you create and implement a cyber-crime strategy, one that protects your organisation’s finances from a new generation of fraudsters.
Cyber-security is now a core priority for many Australian organisations. Boards are investing record amounts in cyber-security, IT and security teams are working harder than ever, and regulatory obligations are intensifying.
But boards and executives need to ask themselves this question:
Despite closer scrutiny and bigger cyber-security budgets, why are Australian organisations still seeing unprecedented financial losses stemming from online fraud and scams?
Part of the answer can be found in the latest Targeting Scams Report from the Australian Competition and Consumer Commission (ACCC), which offered this chilling assessment:
Australia is in an ‘arms race’ with scammers.
Scammers are constantly hunting for innovative new approaches and technologies to facilitate crime in unforeseen ways – crimes that are now costing Australians in excess of $2 billion annually.
Often, the CFO is the only individual standing between these criminals and their organisation’s finances. However, as online fraud and scams become more sophisticated, CFOs need a new approach.
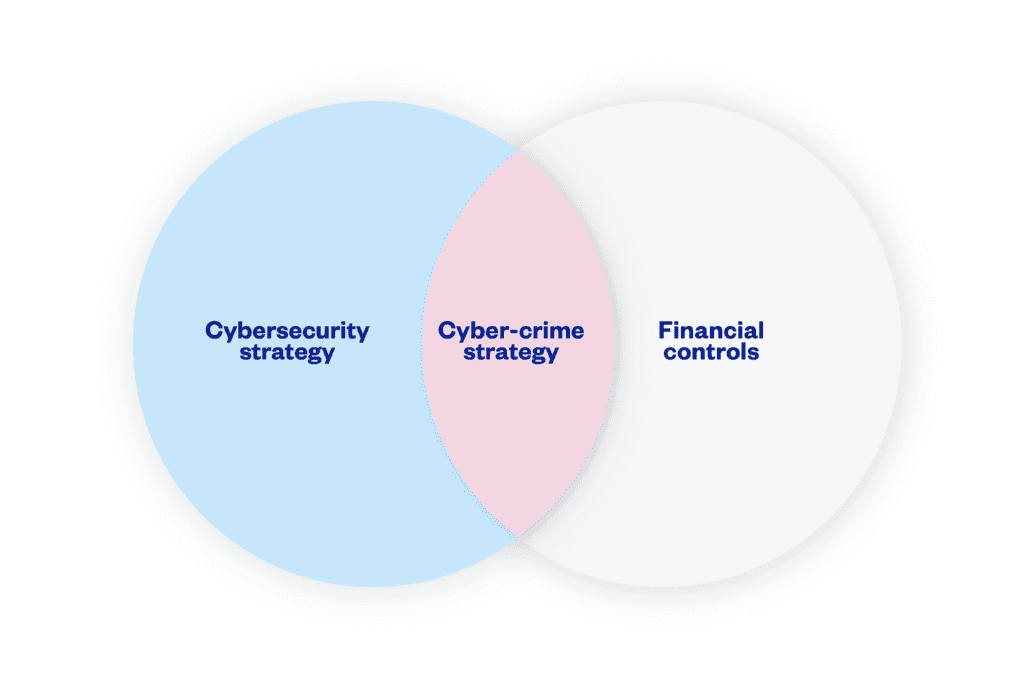
Only a comprehensive cyber-crime strategy, sitting at the intersection of your approach to cyber-security and financial controls, can help you secure your organisation’s finances against a new generation of online fraudsters and scammers.
This guide, Eftsure’s 6th Edition of our Cyber-Security Guide for CFOs, is designed to help you develop a dedicated cyber-crime strategy. It explains:

Download your copy of the 2023 Cybersecurity Guide and prepare your organisation for the next generation of cyber-criminals.
Download GuideAfter 20 years of governments and law enforcement agencies debating how to define “cyber-crime,” the Australian Federal Police now defines cyber-crime as either:
Cyber-security professionals tend to focus on the former, prioritising the protection of networks and devices. Although extremely important, this leaves a gap: many malicious actors may not directly target ICT systems but will use ICT systems to carry out crimes, especially financial crimes.
By contrast, the second definition focuses on how offenders use ICT systems as tools to enhance their criminal activities. It covers a wide range of activities that go beyond the specific targeting of ICT systems, including online fraud and scams.
Professor Peter Grabosky from the Australian National University was among the first to recognise that cyber-crimes mirror older forms of crime – they’re simply committed in new ways.
He described cyber-crime as “old wine in new bottles.” For example:
CFOs have long taken an active role in ensuring their organisation is protected against analogue crimes such as fraud. Today, CFOs still have a critical role to play in ensuring their organisations are protected against modern forms of crime, or “old wine in new bottles.”
Of course, the new generation of cyber-crimes is different in a few crucial ways. Advances in technology continuously offer new opportunities for criminal syndicates, whether it’s a matter of making crimes easier to commit or creating novel vulnerabilities for organisations.
Let’s look at how technology is rapidly changing threat landscapes.
Hybrid work practices offer many benefits, but they also mean that your digital attack surface is larger than ever before.
Your attack surface is the sum total of all the devices and systems you have in your digital environment. The larger your attack surface, the greater the chance that a cyber-criminal will identify a vulnerability they can exploit to get into your digital environment.
For AP staff, the risk is particularly high.
AP teams rely on a wide range of software applications to fulfil their duties, from enterprise resource planning (ERP) systems to online banking applications. They also have access to highly sensitive data, such as Vendor Master Files, that cyber-criminals dream of accessing. When you combine all this with the fact that AP staff may be using personal laptops or mobile devices for work, as well as less secure home Wi-Fi systems, the risk to your organisation is larger than ever before.
Evidence suggests that cyber-criminals have stepped up their efforts to identify and exploit vulnerabilities in expanded attack surfaces, particularly since hybrid work practices became commonplace during the COVID-19 pandemic.
According to the Australian Cyber Security Centre:
“Over the 2020–21 financial year, Australian individuals, organisations and government entities’ engagement online was largely influenced by the impacts of the COVID-19 pandemic. The pandemic has significantly increased Australian dependence on the internet – to work remotely, to access services and information, and to communicate and continue our daily lives. This dependence has increased the attack surface and generated more opportunities for malicious cyber actors to exploit vulnerable targets in Australia.”
Technology is paving the way for a new generation of criminals to target Australians with fraud and scams from anywhere in the world.
This makes identifying and stopping the people behind cyber-crimes notoriously difficult.
For example, according to the 2020 Acid Agari Geography of BEC report, approximately 60% of all cyber-crime syndicates engaging in BEC attacks are based in Africa, the majority from Nigeria. However, cyber-crime has also emerged as a booming business in many other parts of the world, from Eastern Europe to South-East Asia.
Recent reports highlight the fact that online fraud is being perpetrated on an industrial scale from sites across Cambodia, Myanmar and Laos. In countries with high rates of poverty and endemic corruption, organised crime syndicates are operating with impunity, enslaving impoverished locals and forcing them to launch phishing attacks, payment redirection scams and more.
“They have corporate-like organisations, political connections, professional money-laundering networks and increasingly global reach,” according to reports.
All too often, Australians are the victims of such organised cyber-crime. In fact, Australia is the second most targeted country in the world when it comes to business email compromise (BEC) attacks, only behind the United States, according to a report by Statista.
As an advanced economy, with widespread usage of technology like online banking, Australia makes for a lucrative cyber-crime target.
In a digital world, cyber-criminals understand that verifying the identity of someone is harder than ever. New tools that rely on artificial intelligence (AI) are easily accessible, meaning the barriers to becoming an online fraudster or scammer have never been lower.
This paves the way to easily deceive unsuspecting AP staff.
In the following two case studies, we explore how cyber-criminals are using Deep Fakes, along with malicious emails, to extract millions of dollars from organisations.
A sophisticated Russian cyber-crime syndicate, known as Cosmic Lynx, is using Deep Fakes to scam unsuspecting victims into transferring funds to a bank account controlled by the criminals.
“A Deep Fake is a digital forgery created through deep learning (a subset of Artificial Intelligence). Deep Fakes can create entirely new content or manipulate existing content, including video, images, audio and text. They could be used to defame targets, impersonate or blackmail elected officials and be used in conjunction with cybercrime operations,” according to the Australian Strategic Policy Institute.
Put simply, the cyber-criminals behind Cosmic Lynx use Artificial Intelligence to generate impersonated video or audio recordings of a target organisation’s CEO or CFO. These recordings often instruct AP staff to transfer large payments to the cyber-criminals’ bank accounts.
Thanks to readily available tools, such as Hoodem and online tutorials, almost anyone can now generate realistic Deep Fakes:
Not only are syndicates like Cosmic Lynx using Deep Fakes to take cyber-crime to a new level of sophistication, they’re also perfecting the art of deception through much more convincing phishing emails. Unlike infamous “Nigerian prince” scammers of previous years, many of their phishing emails are far more believable – and use better grammar.
Below is an example of one email Cosmic Lynx is thought to have sent one victim with instructions to send over $1.5 million to a bank account in Hong Kong.
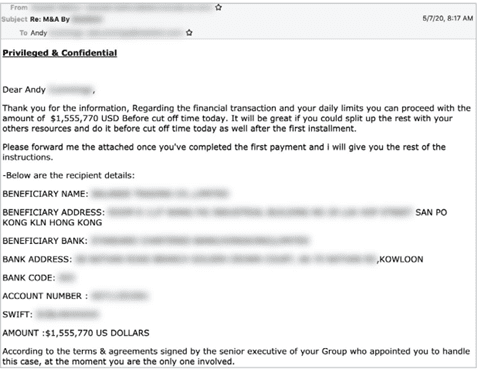
The average amount scammed by Cosmic Lynx is estimated to be hundreds of thousands – sometimes millions – of dollars.
Business email compromise (BEC) is now the leading cyber-crime impacting Australian organisations. Sophisticated cyber-criminals infiltrate email systems in order to deceive AP staff into transferring funds to a bank account they control.
In this documentary, we explore how sophisticated cyber-criminals targeted one leading Australian hedge fund. Starting with a malicious Zoom link, the fraudsters were able to access the hedge fund’s email system. This allowed them to impersonate the fund’s executive and send fake email instructions to process illegitimate payments. The consequences were devastating.
Gone are the days when a budding cyber-criminal needed advanced technical skills to launch their attacks. Recent years have seen the emergence of a cyber-crime ecosystem, in which different cyber-criminals, each with different skillsets, pool their abilities.
This ensures the barriers to becoming a cyber-criminal have never been lower.
Even cyber-criminals with limited technical skills can now target your business using off-the-shelf malicious software (or “malware”) that is developed by advanced hackers and available for lease through the dark web. This business model is known as Malware-as-a-Service (MaaS).
Malware developed by one hacker is then sent by another cyber-criminal to specific individuals in a targeted organisation, often AP staff. In many cases, the malware is disguised as a legitimate link or attachment in an email. Increasingly, malicious links are also being sent via other communications channels, such as instant messaging or video conferencing apps.
When unsuspecting AP staff click the link or open the attachment, they inadvertently open the door to the malware.
Whilst there are many types of malware available for lease, Remote Access Trojans (RATs) are among the most common because they open backdoors into a targeted computer system. This allows the cyber-criminal to access the system whenever they want. Typically, they lie in wait and monitor email accounts before launching their attack at the optimal time.
In BEC attacks, cyber-criminals monitor for any sign of an incoming supplier invoice. Then, they manipulate the invoice’s BSB and Account Number, causing AP staff to inadvertently send the payment to a bank account controlled by the attacker.
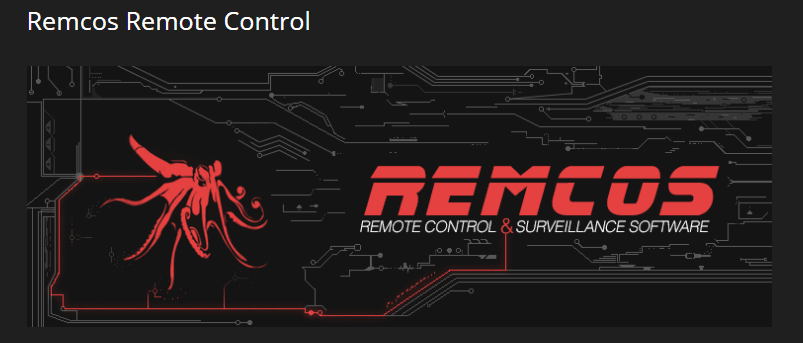
Remcos is a powerful software that allows users to remotely access and take charge of multiple computers.
Although Remcos markets itself as a legitimate computer tool, cyber-security researchers say that it’s widely used by cyber-criminals as RAT malware. All a budding cyber-criminal needs to do is create a Remcos file and find a way to deceive someone into installing it on their computer. The cyber-criminal can then monitor a target’s computer, access all their files, read their emails and steal their passwords.
Thanks to instructional videos, like this eight-minute tutorial on YouTube, even cyber-criminals with limited computer skills can become hackers.
According to reports, cyber-criminals send phishing emails with attachments that supposedly contain important COVID-19 information. However, once the recipient opens the attachment in the email, Remcos is automatically installed, creating a backdoor that allows the cyber-criminal to remotely access and control the computer.
The malicious actor can now gain unauthorised access to email accounts and use these to initiate a range of BEC attacks.
For example, if they gain access to an email account belonging to a CEO or CFO, they can email AP staff with instructions to send funds to a bank account controlled by the criminals. Alternatively, the criminals may seek out emails containing supplier invoices in order to manipulate the BSB and account number, causing AP staff to send payments to the wrong bank account.
Nigel Phair, UNSW Institute for Cyber Security and former lead investigator, AFP High Tech Crime Centre
In some respects, cyber-crime overlaps with cyber-security.
A good example is business email compromise (BEC), an attack vector that sees malicious actors:
These actions can lead to AP staff inadvertently processing payments to incorrect bank accounts controlled by the criminals. In all of these cases, malicious actors are hacking into email systems – this is clearly a cyber-security issue, which IT and cyber-security specialists should be preventing.
However, such BEC attacks represent more than a cyber-security breach.
The goal of these attacks is not to hack into email accounts.
The goal is to steal money.
Hacking into email accounts is simply a means to an end.
To succeed, these criminals not only need to breach email accounts, they also need to deceive AP staff into performing certain acts. By deceiving AP staff, BEC evolves from a cyber-security matter to a cyber-crime matter.
Online fraudsters and scammers are always looking for opportunities to breach cyber-security systems – even if you’re confident in your own cyber-security strategy, you can’t control the security measures of third parties like vendors or partner organisations.
That’s why a cyber-crime strategy is essential. If and when a cyber-security breach occurs, an effective cyber-crime strategy can limit the fallout and minimise your organisation’s financial losses.
According to industry body AustCyber, Australians spent approximately $5.6 billion on cyber-security in 2020. That figure that is expected to increase to $7.6 billion by 2024.
Yet, despite record spending, cyber-crime rates are surging.
According to the Australian Cyber Security Centre’s Annual Cyber Threat Report 2020-2021, reports of cyber-crime increased by 13% from 2020 to 2021. Cyber-crime now costs Australians over $33 billion annually.
Even with increased cyber-security spending, cyber-crime incidents – and their costs – are still on the rise.
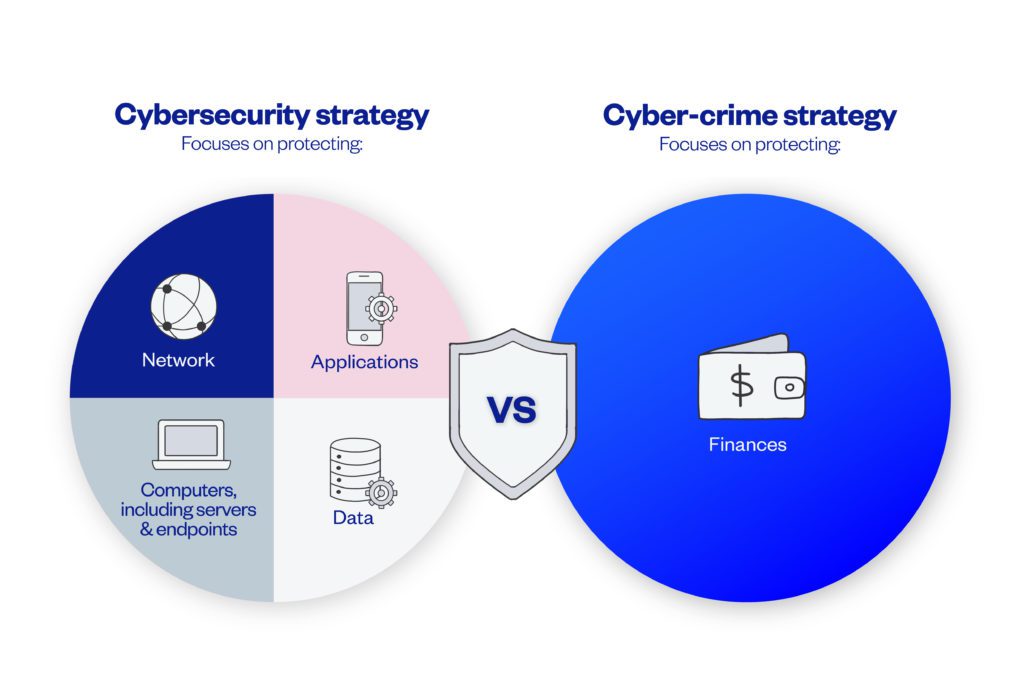
One oft-overlooked factor is that cyber-security primarily focuses on protecting computer systems and data, whilst most cyber-crime is focused on stealing money. In other words, cyber-security strategies are not as focused on protecting the assets that cyber-criminals are usually trying to steal.
That’s why every organisation should develop and implement a cyber-crime strategy.
A cyber-crime strategy brings together elements of your organisation’s cyber-security strategy and elements of your financial controls.
 An effective cyber-crime strategy understands that protecting your organisation’s financial assets will require strong cyber-security as well as strong financial controls. Both elements need to be aligned in order to contain the threat of cyber-crime.
An effective cyber-crime strategy understands that protecting your organisation’s financial assets will require strong cyber-security as well as strong financial controls. Both elements need to be aligned in order to contain the threat of cyber-crime.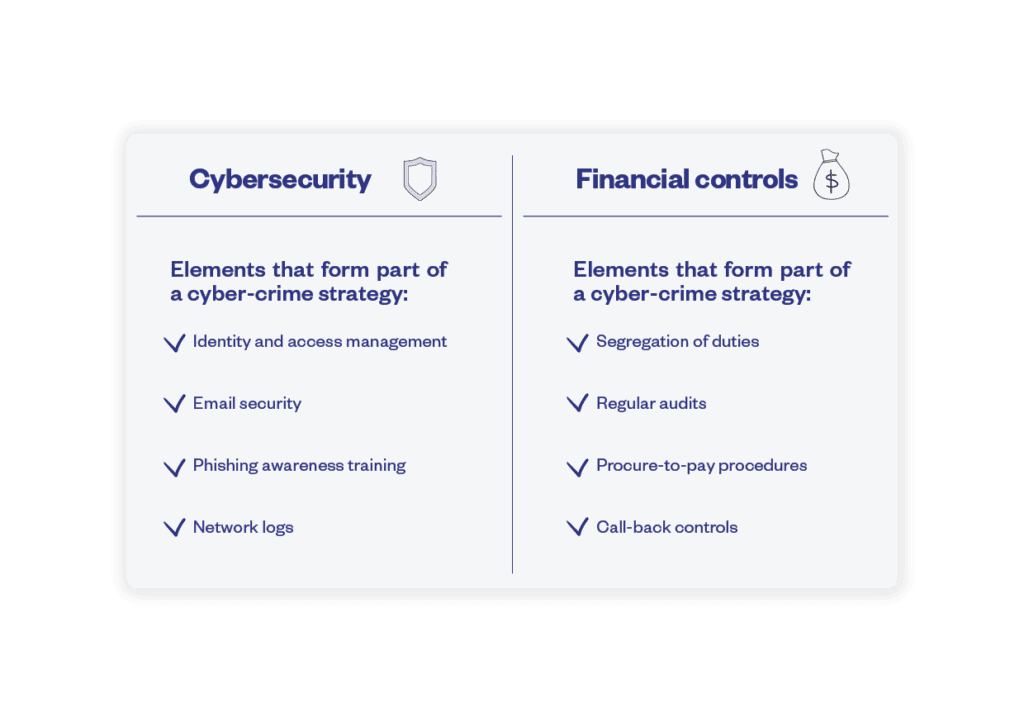 A cyber-crime strategy aims to reduce the opportunity for cyber-crime to happen in the first place. But security breaches do happen, whether in your organisation or a third party. That’s why a cyber-crime strategy also requires appropriate financial controls to reduce the chances that the crime will be successful – in other words, to reduce the potential damage and costs to your organization.
A cyber-crime strategy aims to reduce the opportunity for cyber-crime to happen in the first place. But security breaches do happen, whether in your organisation or a third party. That’s why a cyber-crime strategy also requires appropriate financial controls to reduce the chances that the crime will be successful – in other words, to reduce the potential damage and costs to your organization.
Cyber-Security Strategy + Financial Controls =
Cyber-Crime Strategy
When long-standing ASIC Commissioner, Cathie Armour, recently identified a range of issues that every Australian CFO must prioritise, ‘cyber-resilience’ featured right near the top of her list.
In fact, the corporate regulator hasn’t restricted itself to just speaking about the importance of cyber-resilience. To underscore just how seriously it now takes cyber issues, it recently initiated and won legal proceedings against a financial services firm for repeated failures to adopt sufficient cyber-risk mitigation measures.
RI Advice is a Melbourne-based financial advisory firm.
Over a period of six years, between 2014 and 2020, RI Advice and its authorised representatives faced no fewer than nine cyber breaches. It appears that at least one of the breaches saw cyber-criminals launch a BEC attack. Its email systems seemed to have been hacked as a prelude to deceiving one of the organisation’s clients into sending $50,000 to a bank account controlled by the criminals.
This series of breaches prompted ASIC to launch legal proceedings against the firm. In a precedent-setting judgment, the Federal Court ruled against RI Advice due to its inadequate cyber-risk management systems. The company was ordered to pay the corporate regulator $750,000 in damages.
In line with fiduciary duties under the Corporations Act, all Australian CFOs need to understand the importance of being able to demonstrate to stakeholders – including shareholders, customers, suppliers, regulators and courts – that they take cyber-crime seriously and are prioritising risk mitigation.
Failing to mitigate the risk of cyber-crime could not only cause your organisation to suffer significant financial losses, it could result in a range of other repercussions, from serious legal consequences to reputational damage.
The total cost of the chaos that ensues from cyber-crime can be extensive. In extreme cases, it can financially cripple an organisation.
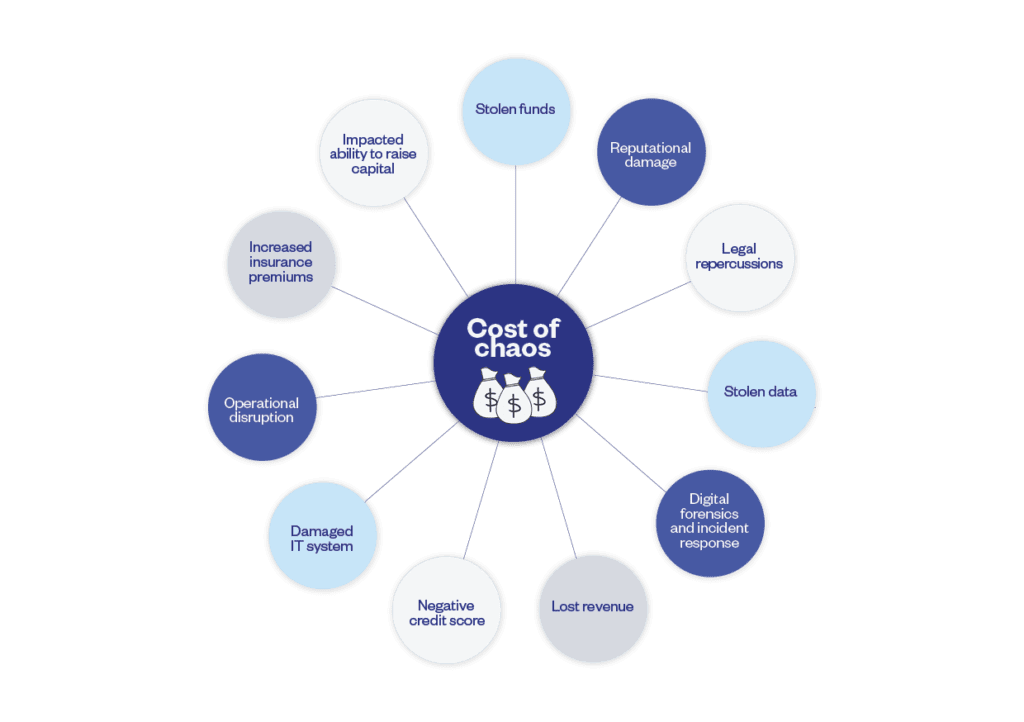
Given the potential for cyber-crime to cripple your organisation, CFOs can’t afford to delegate total responsibility for the mitigation of cyber-crime to IT or cyber-security teams.
In fact, according to Nigel Phair, former lead investigator with the Australian Federal Police’s High Tech Crime Centre, the CFO is the ideal individual in an organisation to take ownership of its cyber-crime strategy. This is because the CFO is charged with protecting the very asset cyber-criminals are targeting: the finances.
“Because cyber-crime is all about fraud and scams, and businesses need to protect their money, the CFO is the logical individual in an organisation to oversee the development of a cyber-crime strategy.” Nigel Phair UNSW Institute for Cyber Security and former lead investigator, AFP High Tech Crime Centre
When developing your organisation’s cyber-crime strategy, there are five essential elements to include. These five elements cover your People, Processes and Technology.
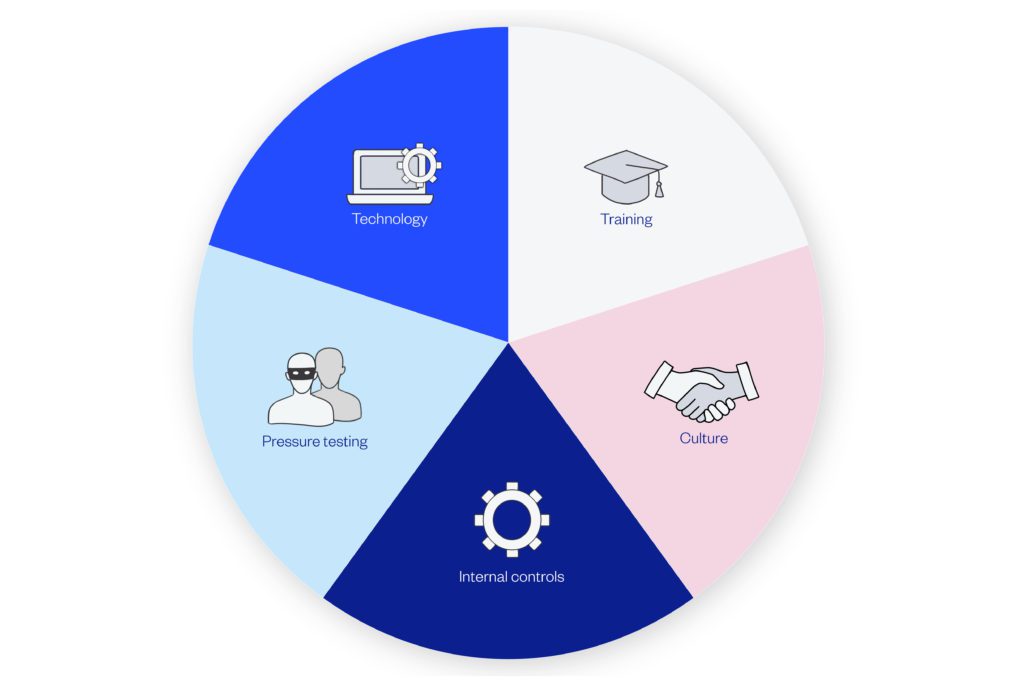
With cyber-criminals actively targeting the people in your organisation, staff training has never been more important.
Many organisations now run cyber-security awareness training on a regular basis. Training modules usually include:
This sort of training is important, but it’s typically developed by cyber-security professionals and may neglect a range of other common cyber-crimes, such as online fraud and scams.
Dedicated cyber-crime training is also necessary. These training modules should cover topics such as:
Cyber-crime training is not a one-time occurrence. It needs to be provided on an ongoing basis, helping staff internalise the important lessons and develop long-term habits around spotting signs of cyber-crime. Shorter, more frequent training modules are likely to be more effective than longer, annual training modules.
Some key points to remember when developing a cyber-crime training program:
Training initiatives are just the first step when it comes to stopping online fraud and scams.
You also need to cultivate a culture that aligns everyone in your organisation around efforts to prevent cyber-crime. After all, your goal should be encouraging staff to become an extension of your eyes and ears across the organisation, alerting you to any suspicious activities.
When cultivating a strong security culture and awareness, focus on the following:
Your internal controls are the processes you put in place to mitigate a range of risks, such as cyber-crime.
Because cyber-crime risks are constantly evolving, your internal controls also need to be continuously reviewed and enhanced. Without sufficiently robust internal controls in place, your organisation may face a heightened risk of online fraud and scams.
According to CPA Australia, robust internal controls should satisfy the following goals:
As part of your cyber-crime strategy, make sure you establish a cadence for regularly reviewing your organisation’s cyber-crime risks and whether your existing internal controls need strengthening.
One way to ensure your internal controls are sufficiently robust is through regular pressure testing.
Pressure testing is a methodology that helps you determine whether your policies, processes and procedures are up to the task of mitigating a particular cyber-crime risk. This is one of the most effective ways to identify vulnerabilities in your internal controls, as well as how to strengthen those controls.
Common ways to pressure test your AP team’s internal controls and cyber-crime awareness
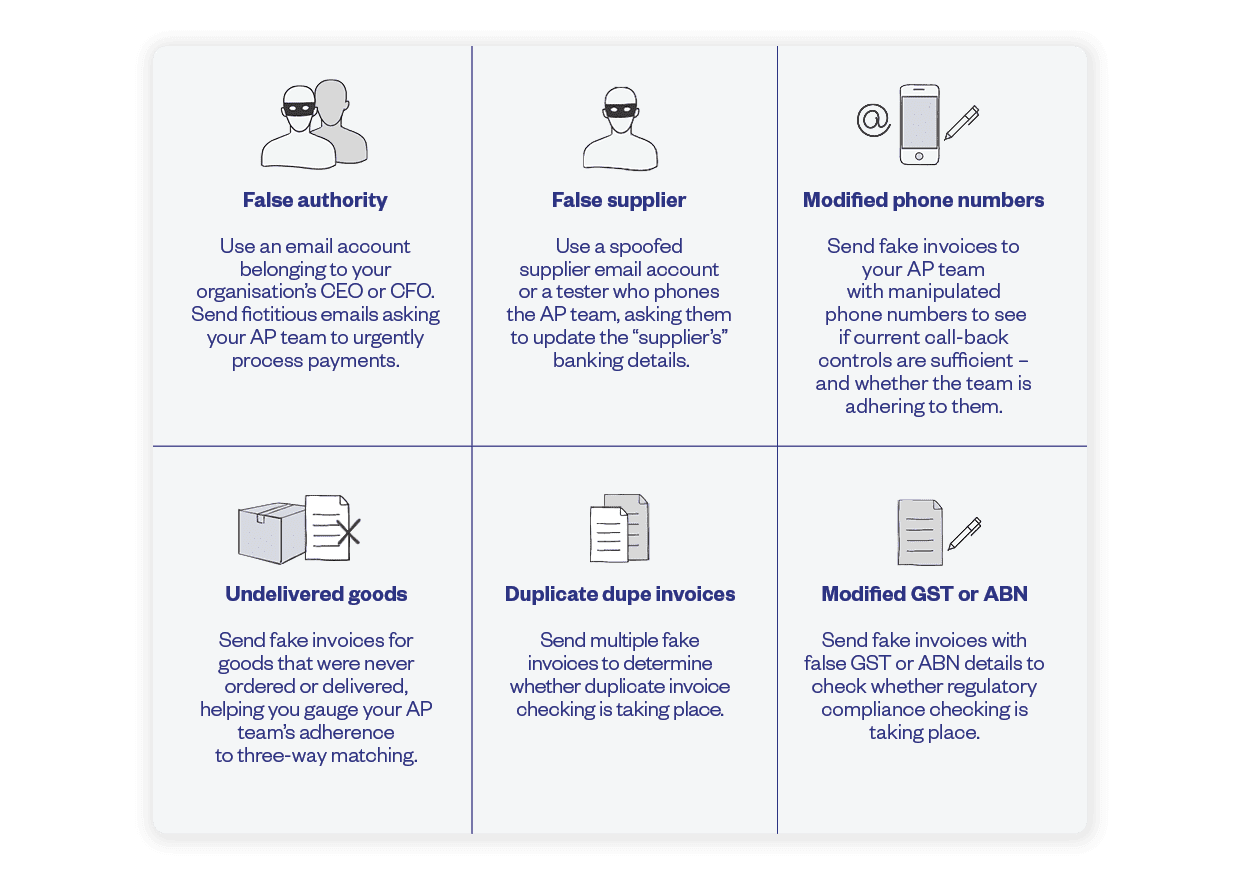
This is just a selection of the types of pressure testing that you can implement. The range of pressure tests will depend upon the specific cyber-crime risks your organisation is most likely to face.
Cyber-criminals are always looking to leverage new technologies and approaches. If you’re not doing the same thing, you might be ceding crucial advantages in the fight to protect your organisation from cyber-crime and fraud.
Your people and processes are essential lines of defence against cyber-crime, but both can be prone to circumvention or error. The right technology can standardise and automate manual processes – where human error is more likely – and lower your risks of cyber-crime, even when fraudsters and scammers have bypassed your other defensive layers.
This element of your cyber-crime strategy doesn’t require you to boil the ocean. Solutions like Eftsure can be set up quickly and work on top of your current system and processes.
Eftsure is the leading technology solution helping Australian organisations of all sizes stay secure from technology-enabled cyber-crime.
With Eftsure sitting on top of your accounting processes, you benefit from a final line of defence that ensures funds are not misdirected by online fraudsters and scammers. Even if the cyber-criminals manage to deceive your people and evade your processes, you can rest assured that outgoing payments are only sent to the intended recipient.
Eftsure’s proprietary database collects data from over 90% of active Australian corporate entities. This data is collected from multiple, independent sources – critical for ensuring its veracity and legitimacy.
Each time you process outgoing payments, the beneficiary details are cross-matched in real-time against the Eftsure database. When the banking details align, you receive a ‘green-thumb’ notification, indicating the beneficiary’s banking details are legitimate. When banking details don’t align, you receive a ‘red-thumb’ notification, indicating the payment should be paused for further investigation.
No other technology solution offers this level of assurance to CFOs, finance and accounting executives, or AP staff, helping you protect your organisation from a new generation of fraudsters.
Technology is giving cyber-criminals the upper hand. Eftsure tilts the playing field back in your favour.

Book a demonstration with Eftsure and take your first step towards securing your organisation's financial assets.
Book a demoEftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.