The riskiest guessing game: a guide to insider threats
It’s an uncomfortable reality, but leaders can’t ignore it.
A growing amount of fraud incidents stem from malicious insiders. Rather than micromanaging or distrusting their own people, finance leaders should look to mitigate risks of insider fraud and error through zero-trust procedures and tech solutions.
Foreword
A note from Mark Chazan, Chief Executive Officer, Eftsure
High-profile data breaches and cyber-attacks have rattled business communities worldwide, with headlines dominated by shadowy cybercriminals who target an organisation from the outside.
But there’s an under-discussed yet critical risk: the dangers inside an organisation.
Insider threats are just as risky as external ones, with the potential to cause major financial losses, compromise data, erode customer trust and damage company reputation. Not only are trusted insiders closer to critical processes and sensitive data, but they also have more ways to cover their tracks and can operate with a sophistication that rivals external actors.
It can be hard to imagine an employee acting maliciously or negligently, and it’s true that most of your people are almost certainly acting in good faith. But leaders can’t just rely on “hiring good people” because the risks are too big.
Fortunately, the right processes and technology create a zero-trust environment in which all employees and contractors are held to the same standards, reducing your fraud risks and offloading the need to second-guess your people. This guide will dissect insider threats and arm you with the knowledge to protect yourself – without compromising your team culture.
Defining and classifying insider threats
Defining and classifying "insider threats"

Breaking the term insider threat down
Insider: The US Cybersecurity and Infrastructure Security Agency (CISA) explains an insider as anyone who has (or used to have) “authorised access to or knowledge of an organisation’s resources, including personnel, facilities, information, equipment, networks and systems.”
Threat: CISA defines an insider threat as “the potential” for an insider to use that authorised access or understanding of an organisation to harm that organisation or its personnel.
This definition encompasses any type of threat to the organisation’s security or its employees’ security, including physical threats or violence. However, this guide will focus on the threats that fit more squarely within a finance leader’s purview – that is, potential insider fraud or theft.
Even when it comes to financial misconduct or fraud, many organisations focus on traditional security controls that tend to focus heavily on external threats which are not always capable of identifying internal threats. By nature, insider threats are difficult to detect. It’s the very fact that these types of employees possess intimate knowledge of the organisation’s processes that enables them to execute fraudulent activities discreetly and effectively.
Types of insider threats
Malicious insiders
These insiders intentionally engage in activities that harm their organisation. They may be driven by financial gain, revenge, ideology or personal reasons. Malicious insiders usually steal intellectual property, sabotage systems, leak confidential data, misuse funds or engage in fraudulent activities. Their actions can be extremely damaging and difficult to detect.
Negligent insiders
These individuals pose a threat due to gross carelessness or a lack of understanding of security controls. This type of insider threat goes beyond good-faith mistakes or one-off misunderstandings. Instead, this type of unintentional insider threat is familiar with finance, IT or security processes but chooses to ignore them. They lack malicious intent but still pose a more persistent threat than employees who might make a one-off error.
Compromised insiders
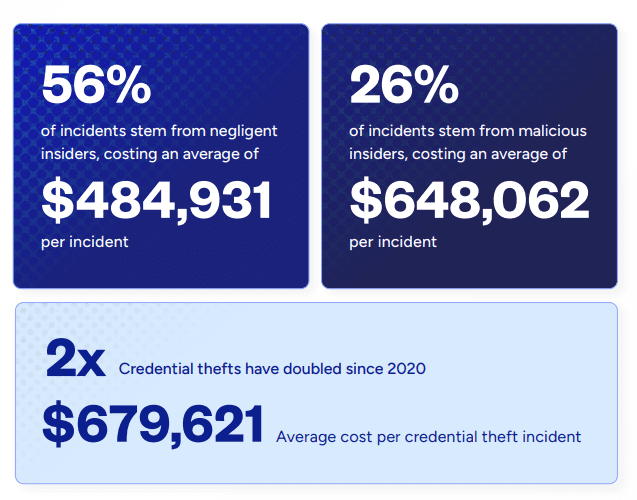
Another type of unintentional threat, compromised insiders unwittingly act as conduit for malicious actors. Cybercriminals may compromise an individual’s email account or device, allowing them to gain unauthorised access to sensitive information or systems. Credential theft – when outside actors compromise staff login details – is on the rise, according to Proofpoint estimates. And it also estimates that the cost of this kind of incident increased 65% from $2.79 million in 2020 to $4.6 million in 2022.
It’s useful to understand the different types of insider threats – your organisation may be at greater risk of some threats compared to others, which should inform how you prioritise risk mitigation measures.
As CFO, your concern can’t stop at malicious insiders – you’ll also need to consider the impact of negligent employees or those prone to human errors within your accounts payable (AP) teams. In fact, negligent insiders are the root cause of most incidents – Proofpoint claims that 56% of incidents, totalling 3,807 attacks, were due to employee or contractor negligence, with each incident carrying an average cost of $484,931 per incident.
While unintentional threats might be more common, malicious insiders are likely to cost your organisation a larger dollar amount. They accounted for 26% (1,749) of incidents, with an average cost of $648,062 per incident.
Insider threats are rising in both frequency and cost
Frequency
According to a 2023 Trellix analysis, insider threats have increased by 47% over the last two years. And research from Ponemon Institute and DTEX estimates that the number of incidents has been increasing each year since 2018.
Even if incidents are increasing, does this mean insiders are responsible for most of them? Unfortunately, the DTEX 2022 Insider Risk Report estimates that around 57% of fraud incidents involve an insider.
On average, a growing number of organisations are experiencing more than 21 incidents per year.
In 2023, 71% of companies experienced between 21 and 40 insider incidents per year, an increase from 67% the previous year.
Companies in North America are spending the most to resolve insider risks over a 12-month period, potentially indicating that a greater number of incidents are impacting these organisations.
Cost
Across all types of insider threats, the annual cost per incident continues to become more expensive – and incidents caused by malicious insiders are the most expensive of all. Remediating these incidents can eat up significant resources and time, not to mention damaged relationships or lost revenue.

What are red flags for insider threats?
Internal fraud can be notoriously difficult to identify and stop. Compared to external actors, insiders tend to have far more avenues to obscure their actions. Given how difficult it can be to detect these threats, it’s essential to know the warning signs – and to foster a culture in which other staff can identify these red flags and feel comfortable speaking up.
1. Requesting unnecessary access to systems and networks
In every organisation, access to systems and sensitive data should be accessible on a need-to-know basis. Sometimes called the principle of least privilege (PoLP), this means limiting access only to those employees who need it to perform their duties.
Be alert when an employee:
- Makes an unusual request to access controls to a system or file
- Requests greater privileges within a system than they’ve already been permitted
- Requests sensitive information that is not required to perform their job function
- Makes requests through internal stakeholders without informing managers
You should carefully assess whether granting or extending access will undermine segregation of duties policies. For example, an employee may have read-only access to vendor banking data and may be requesting editing access. Such requests should always be carefully considered before agreeing to the request.
If an employee is requesting too much access to sensitive information that is not required to perform their job, it may be an indication of malicious intent and their activities should be carefully monitored.
2. Disorganised or incomplete record-keeping
Employees who maintain disorganised or incomplete records may be doing so in a deliberate attempt to obfuscate malicious activities. Without organised records and activity monitoring, accurate audit trails become almost impossible.
Be alert when an employee:
- Consistently fails to attach receipts or invoices to expense reports
- Uses incomplete expense descriptions that make it challenging to track expenses accurately
- Fails to consistently organise and file financial documents
- Disregards established protocols for record-keeping
- Consistently fails to report errors or discrepancies in record
Every organisation should invest in ensuring they have the right policies and oversight of records to ensure that proper standards are maintained. Regular internal audits will be able to identify problematic record-keeping practices at an early stage, so they can be rectified promptly. In short, you need to keep on top of employee record keeping.








