The Australian Competition and Consumer Commission (ACCC) is urgently sounding the alarm about a major rise in business email compromise (BEC) attacks. These attacks weaponize compromised email accounts to impersonate trusted senders and trick the target into making fraudulent payments, giving up sensitive info, or downloading malware. Since they're often the ones authorizing business payments, accounts payable (AP) teams are common targets.
The growing threat has prompted the ACCC to release a guide for protecting yourself, including the need for training and awareness. By spotting a BEC attempt, you could save your business thousands in both direct and indirect costs. According to the Australian Cyber Security Centre (ACSC), the average loss per successful BEC has increased to over $64,000.
So let's take a look at how to spot one of these attacks.
How to spot a BEC
1. Bogus email address
One of the first components you should look out for in a spoofed email is the email address. Depending on which email provider you’re using, emails may sometimes display the name of the user. For example, it may have the person’s name or initials as their display picture.
If you suspect a fake email, always look carefully at the actual email address and the domain name, not just the sender’s display name. This is displayed in the fake email below where the sender’s name “Mel Adams” has misspelled the domain name by including an extra “l” in the domain name. Many people might not notice this at first glance.
However, when you check carefully, you'll notice the domain name is a red flag.
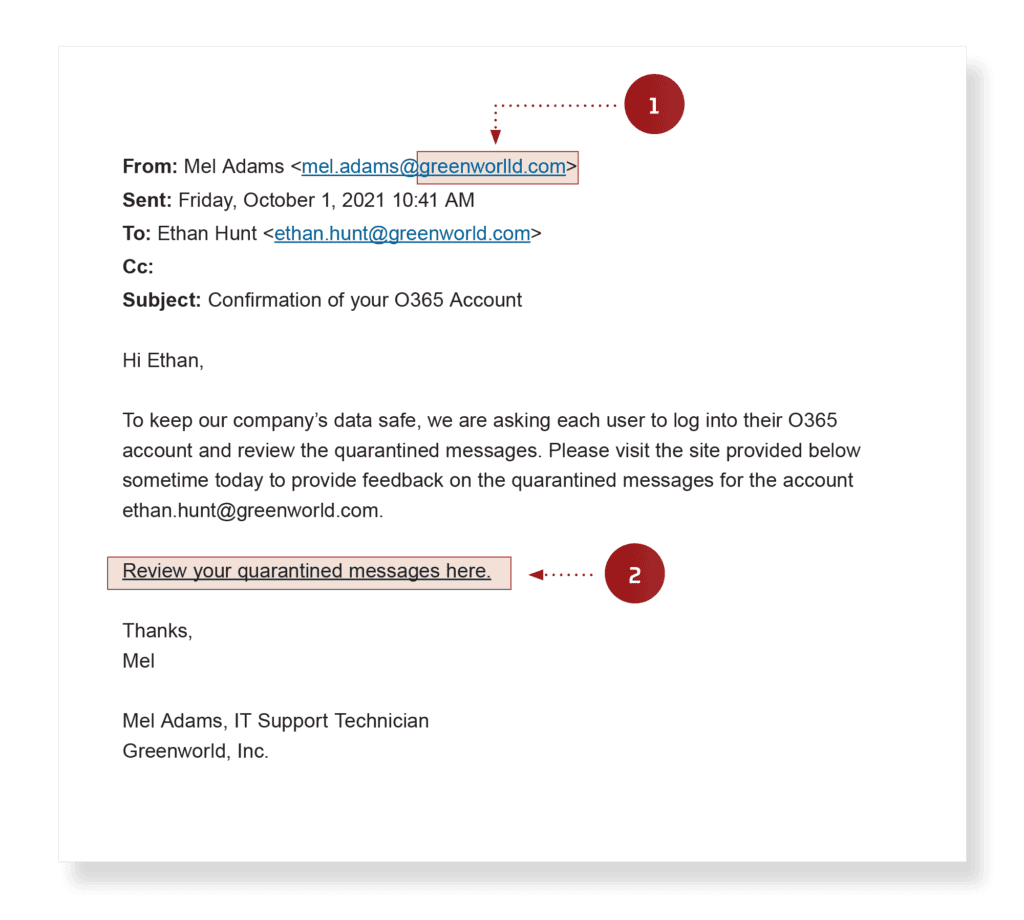
Source: Pratum
It's important to note that attackers are getting more sophisticated, though. Even if you recognize and trust an email address, a malicious actor might have compromised the inbox of your supplier or contact (more on this in step #3).
2. Malicious links or attachments
Another red flag is emails that contain malicious links or attachments. In the image above, words that are highlighted and underlined usually have an attachment. In this case, “Review your quarantined messages here” contains a suspicious link.
By clicking on a malicious link, you may be downloading a virus, trojan, or any other type of malware that can compromise your computer or network. These tactics are potent because they can look so much like the usual links and attachments you might receive from colleagues.
That’s why it’s generally best practice not to click on links or attachments in an email. Your default assumption should be that email with links or attachments needs a closer look, unless it’s a message you’re already expecting to receive.
3. Legitimate vendors or executive emails
Even when emails come from recognized senders, you still need to be careful. Sometimes the call is coming from inside the house.
Also known as an email account compromise (EAC), attackers can gain access to the accounts of trusted colleagues or vendors. Attackers often investigate and research their targets, creating a sophisticated plan to defraud your organization through legitimate email threads.
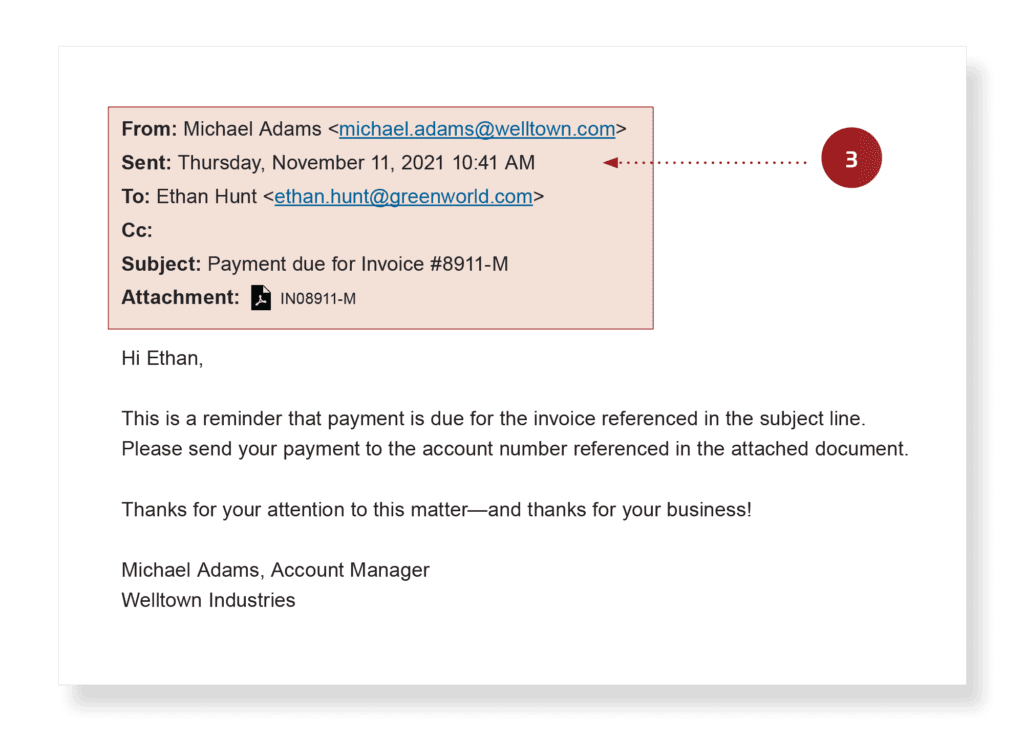
In this case, the attackers have taken over Michael Adams’ email account and have planted their attack. One way to confirm if the email is genuine is to verify with the sender by using other communication methods like phone calls or video calls.
4. Scheduling and timing
To create a sense of urgency, cybercriminals may send suspicious emails at times when you least expect it. For example, attackers may send you scheduled emails during:
When a scammer has infiltrated your employer’s email system, they're far more likely to understand when to send you a timely response. They’re hoping to catch you off guard, when you least suspect an attack or are less likely to spend time verifying the email.
Whenever you see an email calling for immediate action, take a moment to pause and read the email carefully. If the email is unusual, follow up with a phone call to ensure the request is genuine.
5. Email content
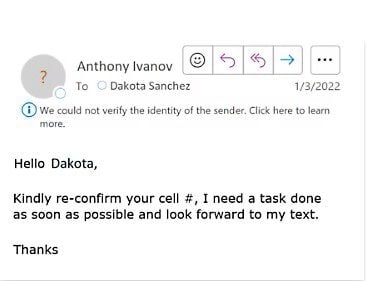
Source: Microsoft
Along with the timing of the email, the contents of the email are just as important. Here are a few examples a BEC attacker may use in a phishing message:
I need help with a quick task, can you send money to this new account?
We would like to process a wire transfer, please confirm today
I need you to make a bank transfer ASAP
Please pay today so I can confirm with my co-worker
I need you to complete a task for me discreetly
Got a moment? Give me your phone number. I need you to do a task for me
Please see the attached invoice. When will this payment be made?
I need you to purchase five $100 gift vouchers and email the codes ASAP
Scammers are known to play psychological tricks on your AP team by sending messages that play on:
6. Request for payment or change of payment details
In a business email compromise, the goal of the scammer is to obtain financial information from their victims by defrauding your organization. BEC scams typically use subject lines or emails that imply urgency regarding payment inquiries or fund transfers – for example, “payment - important” or “quick request.”
They may impersonate your CEO or CFO and request you to pay to another bank account in an invoice or pay a vendor’s bank account that has been compromised by the attacker, once the funds have been transferred.
In unfortunate cases, successful BEC or phishing attacks can lead to a loss of sensitive information including credit card details and other personal information. This gives the attacker the ability to commit further fraudulent activities like selling personal information on the dark web, similar to the recent Optus data breach.
How can Eftsure help?
Identifying warning signs in an email from an attempted BEC attack could save you thousands of dollars.
By incorporating security awareness training and simulating BEC attacks, your AP staff can become more comfortable in spotting phishing emails that contain all sorts of malicious techniques. This is why security awareness training is necessary. Unfortunately, to an untrained eye, a phishing email could seem like a genuine email from a vendor or senior executive.
However, by integrating Eftsure into your accounts payable function, you’ll add a layer of risk mitigation. Whether a BEC incident has occurred within your organization or a partner organization, Eftsure can minimize your chances of experiencing some of the most damaging consequences of a successful attack – that is, fraudulent payments.
Our solution is designed to alert your AP team in real-time that payments are verified, using easy-to-understand, user-friendly alerts on your online payments screen. Our alert system will confirm whether you’re paying the right BSB and account number or if there needs to be further verification.
Contact Eftsure today for a full demonstration of how we can help minimize the risk of a BEC attack, or download our incident response guide to learn more.
BEC Incident Response Guide for Finance Teams
Learn how to respond to a Business Email Compromise attack by following the necessary steps.
Download the Business Email Compromise (BEC) Incident Response Guide today to strengthen the odds of recovering your funds following a BEC attack.










