Australians spent $5.6 billion on cybersecurity products and services in 2020, according to industry body AustCyber. And that figure is likely to rise.
So, with Australians spending more than ever on cybersecurity, the number of cyber-incidents should be decreasing… right?
Wrong.
Reports of cyberattacks keep growing year-on-year. High-profile attacks, like Optus and Medibank, demonstrate that cyberattacks are having a devastating impact on Australia. Targeted organisations can face massive losses, while millions of individual customers suffer the consequences of stolen personal information.
All this leads to one big question: why, despite record spending, is Australia failing to stop cybercrime?
At least part of the answer may lie in the fact that our cybersecurity approaches don’t always match up with the most common types of cybercrime.
Cybersecurity versus cybercrime
The Australian Cyber Security Centre (ACSC) defines the term “cybersecurity” as the measures used to protect the confidentiality, integrity, and availability of systems, devices, and the information residing on them.
However, if you take a look at the most recent Annual Cyber Threat Report by the ACSC, you'll notice something interesting. In the vast majority of cybercrimes reported to the ACSC over the last 12 months, the goal was not to compromise the confidentiality, integrity, and availability of systems, devices, or information.
Instead, the goal was to steal money.
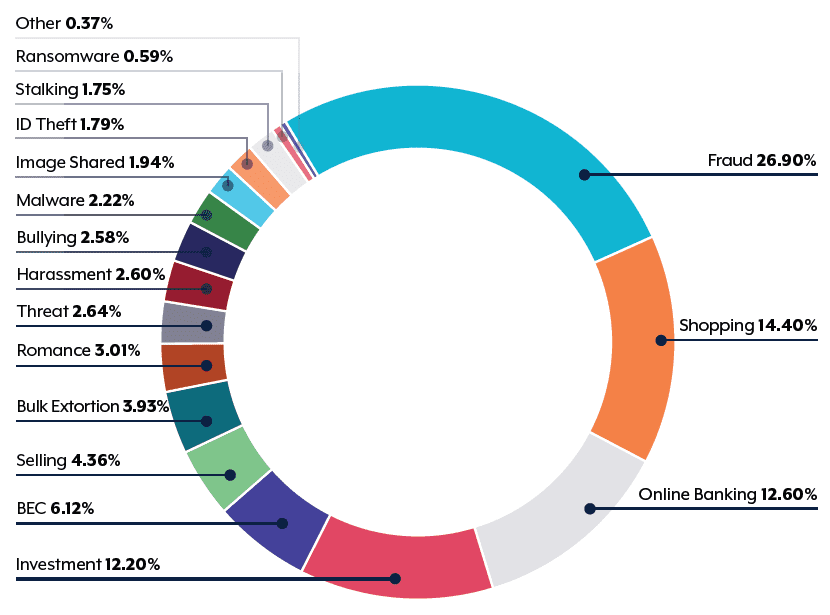
ACSC: Cybercrime reports by type for financial year 2021-22
The top eight reported cybercrimes were all financially motivated. Together, they represent over 83% of all cybercrimes reported to the ACSC last financial year.
Often, cybersecurity is focused on protecting data and the associated ICT systems, yet the cybercriminals are overwhelmingly focused on the money.
In other words, our investments in cybersecurity products and services aren't aligned with the actual threats - or what's motivating them.
Developing a cybercrime strategy
Organisations are starting to focus even more on their cybersecurity strategies. They’re routinely penetration-testing their environment, developing comprehensive information security policies, and investing in systems like multi-factor authentication. All of this helps protect against data breaches and security threats.
These initiatives can definitely make life harder for hackers, but they aren’t directly focused on safeguarding your financial assets. Sure, protecting your money will be a by-product of all these initiatives, but these cybersecurity initiatives don’t do much against the tsunami of financially motivated scams currently drowning Australians.
Protecting your money from financially motivated cybercriminals requires a different approach. It requires a comprehensive cybercrime strategy.
What is a cybercrime strategy?
A cybercrime strategy shares a lot of elements of a cybersecurity strategy. For example, strong user access controls are an essential feature of both. By restricting access to systems to those who absolutely need access, you can help protect both your data and your finances.
What sets a cybercrime strategy apart from your cybersecurity strategy is that it helps you stop scammers who are using digital systems to trick people into handing over money. And, as we can see from the statistics above, financially motivated cybercrimes represent the overwhelming majority of cybercrimes.
A cybercrime strategy brings together elements of your cybersecurity strategy and your financial controls. It recognises the importance of information security but also recognises the importance of robust financial controls, like segregation of duties.

How can a cybercrime strategy stop financially motivated cybercrime?
Take Business Email Compromise, or BEC, as an example.
BEC attacks cost Australians over $98 million last financial year, with the average amount lost in a BEC scam soaring to over $64,000.
BEC involves attackers getting access to an executive’s email account, before using it to send emails to Accounts Payable (AP) staff with instructions to make illegitimate payments, often to fictitious suppliers. While your cybersecurity strategy should prevent scammers from accessing the email account in the first place, we know that no cybersecurity strategy is foolproof. And no matter how strong your cybersecurity strategy might be, you have no oversight or guarantees when it comes to your suppliers’ security practices.
Stopping BEC requires more than simply protecting your email accounts from unauthorized intrusion. It also requires strong financial controls to ensure that:
One AP officer enters payment requests into your system, but another AP officer actions the payment (segregation of duties)
All outgoing payments are double-checked through call-backs
By ensuring you have both strong cybersecurity measures and robust financial controls, you can protect your organisation from rising cybercrime.
Ready to learn more?
Our Cybersecurity Guide for CFOs dives deeper into what’s fuelling new cybercrimes and provides practical guidance for implementing your own cybercrime strategy.








