Safeguarding corporate data is at the top of every leader’s list. As cyberattacks continue to evolve and become more sophisticated, cybersecurity also needs to evolve. With so many financially motivated cybercrimes, CFOs and other finance leaders can’t afford to sit back and let security issues bottleneck their IT teams.
That’s why it’s important to be aware of the different approaches organizations can take to safeguard their corporate data, customer data, and financial assets—one of those approaches is ‘zero trust’ architecture.
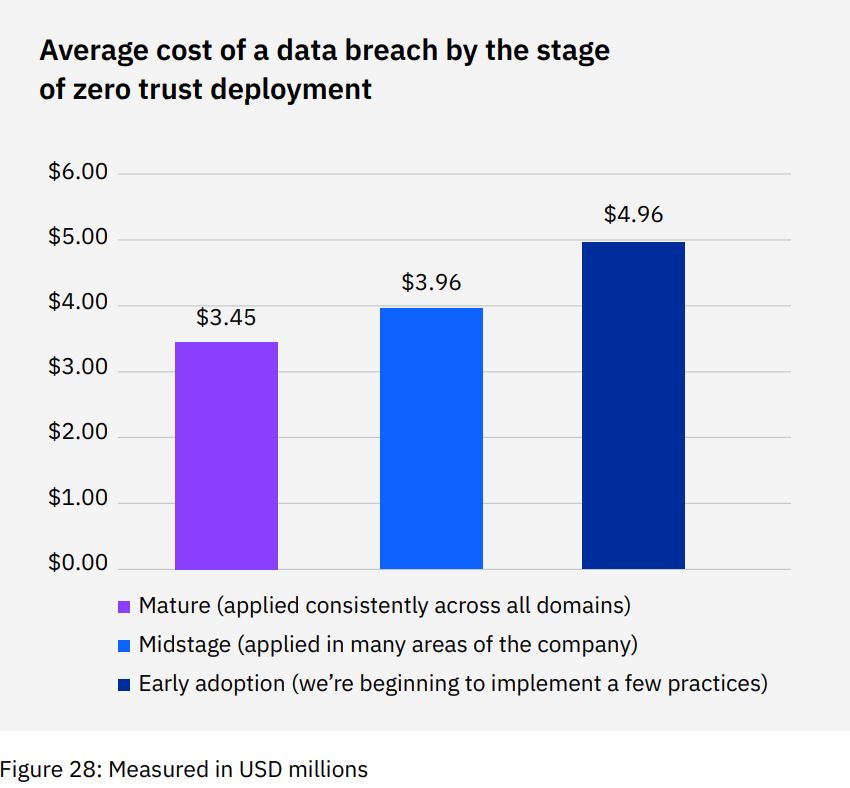
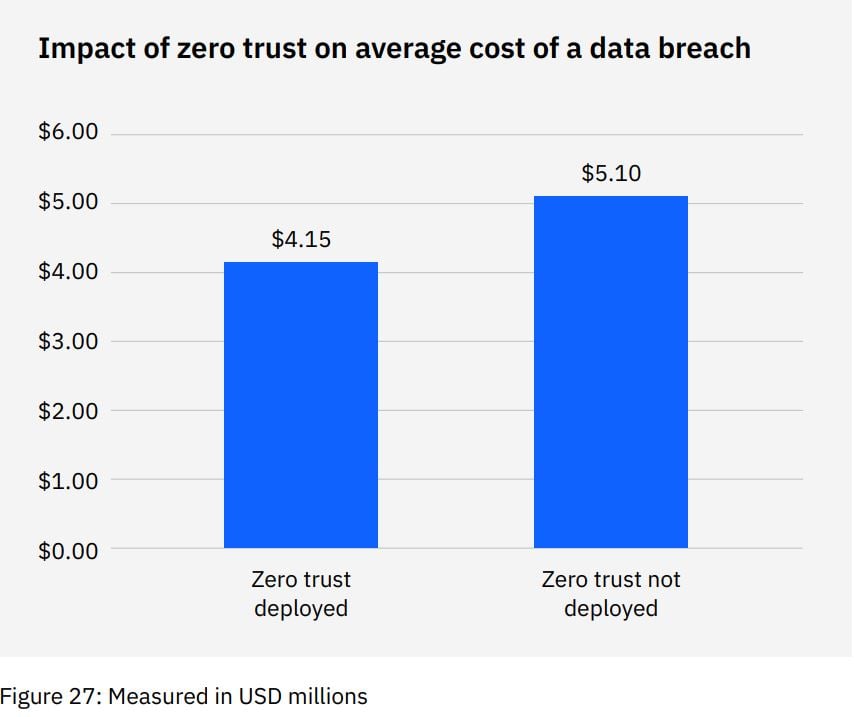
According to the 2022 Cost of a Data Breach Report by IBM, 41% of organizations in the study said they deployed a zero trust security architecture. The other half that didn’t implement the zero trust model incurred an average of USD 1 million in greater data breach costs compared to those that have.
This is where zero trust security comes in. In this guide, we'll explore what it is and why it matters to Finance teams.
What is zero trust security?
According to IBM, the zero trust model was first developed by John Kindervag in 2010. A zero trust framework is a broad framework that promises effective protection of an organization’s most valuable assets. The security architecture requires strict authentication and access controls to protect corporate assets from unauthorized access.
Under the zero trust model, every user, device, application, and service is treated as untrusted and is required to go through a verification process. This verification process includes identity and context verification, which is done before granting access. The idea behind this is to ensure that no malicious actors can gain access to the organization’s valuable assets.
This eliminates the traditional approach of relying on a perimeter-based security system, where certain external connections are not trusted and the internal networks are assumed to be secure. The zero trust model ensures that all connections, both internal and external, are treated as potentially malicious and are thoroughly verified before granting access.
Zero trust security instead creates an environment where every user, device, and application must be authenticated before gaining access to corporate data or resources.
Components of zero trust security
Zero trust security assumes that nothing inside or outside of the network can be trusted, requiring every access request to be verified and authenticated. Let’s take a look at the core components of what makes up a zero trust security framework.
Least privilege access
Least privilege access ensures that employees only have access to the systems and data that are necessary for the core functions of their job. This minimizes the risk of a malicious actor circumventing preventive controls or accessing sensitive assets.
The principle of least privilege is an important one for finance and AP teams, even outside of zero trust frameworks. It’s also a cornerstone of controls like segregation of duties, which diffuses accountability across entire teams—like zero trust security approaches, it’s a control that assumes a system may one day be breached and minimizes risks accordingly.
Device access control
Device access control, also known as selective device access control (SDAC), is a component of zero trust security—it ensures all users, devices, and applications are treated as untrusted until their identity and context can be consistently verified. Proper implementation will require clear policies and processes around device management, activity monitoring, and the implementation of biometrics and behavior analytics.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a core value of zero trust security. MFA is an important part of security hygiene, helping to safeguard your organization’s networks, applications, endpoints, and critical data.
MFA requires you to have at least three or more of the following verification methods to authenticate your access:
Something you know (password or PIN)
Something you have (token, one-time password, or USB stick)
Something you are (biometrics like voice recognition or facial recognition)
We discuss why a simple password is not enough to secure your organization and why MFA is necessary for AP teams.
Continuous monitoring and validation
With traditional network security, employees are given access to different levels of data based on their roles. However, this approach assumes that all users can be trusted equally, all of the time—but this isn’t the case.
Not only are insider threats unfortunately real, but attacks like business email compromise (BEC) mean that users’ accounts can be infiltrated and weaponized at any time. No matter how well-meaning or upstanding your employee might be, it won’t necessarily stop their accounts or inboxes from becoming attack vectors for malicious actors.
Zero-trust security eliminates the blind trust of previous approaches by requiring users to authenticate themselves before accessing any data or resources. Continuous monitoring ensures that all activities within the system are being tracked and analyzed for unusual behavior like anomalies or suspicious login times. By working closely with your IT department, you can ensure that all devices and network resources are properly secured and monitored.
Benefits of zero trust security
According to IBM statistics, organizations with zero trust deployed saved nearly USD 1 million in average data breach costs compared to organizations without the model. Plus, it still allows employees to work from any place on any device with access to tools and data in any ecosystem. In other words, it helps preserve the many benefits of hybrid working and geographically dispersed teams while minimizing some of the risks.
Put simply, the main benefit of zero trust security is a reduction in cyberattack surface.
The zero trust security architecture allows businesses to restrict access to assets and data only to authorized users with verified authentication. This approach minimizes network vulnerability even if one of the endpoints is compromised. In addition, zero trust approaches improve visibility and control over data access.
Organizations can implement contextual policies that allow them to monitor who accesses their data based on various parameters such as location or device type. This enables more efficient control over user privileges and improves compliance with regulations, mostly because it tends to allow for more granular analysis of employee behavior when accessing corporate resources.
Why do finance professionals need to consider zero trust approaches?
The practical reality of rising cybercrime is that finance professionals are often the last line of defense against financially motivated scammers and fraudsters. Cybersecurity hasn’t always been considered the jurisdiction of finance leaders and professionals, but it’s becoming a critical consideration for AP workflows and policies.
Leaders should be looking to partner with IT or security teams, designing the right processes that leverage zero trust principles where appropriate—without input from finance professionals, leaders risk ending up with workflows that aren’t user-friendly and might be difficult to scale across higher volumes of payments and AP activity.
In addition to preventing financial losses due to data breaches, zero trust security can also help CFOs ensure regulatory compliance. Many regional or national regulations require companies to protect the personal information of customers and employees—some zero trust approaches can help finance leaders track who has accessed what information and when it was accessed.
Cybercrime's cost of chaos can cripple even the largest organizations—major breaches like those at Optus or Medibank cause serious damage for brands and their customers, while cyber incidents can shudder an organization completely (see: Levitas Capital).
Even when an organization survives a cyber incident, we’ve seen direct financial consequences like legal fees and lost revenue as well as indirect costs associated with reputational damage. This was also clear in the case of the Latitude Financial data breach, which generated significant media attention and impacted millions of customers.
The theft or loss of intellectual property is another risk that might be mitigated through zero trust security measures. The value of these assets cannot be understated, and their loss could result in devastating financial losses for a company.
Regulatory compliance
Compliance with data privacy regulations, such as GDPR and CCPA, is critical for safeguarding sensitive corporate information. Non-compliance can result in severe penalties, including hefty fines and reputational damage.
Meeting regulatory compliance requirements should be a top priority for any organization that collects or processes personal data. In addition to avoiding legal consequences, compliance demonstrates good corporate governance and reinforces trust between an organization and its stakeholders.
Remote workforce
The COVID-19 pandemic has led many organizations to embrace a hybrid and remote workforce, which has presented challenges for CFOs in securing corporate networks and devices, such as laptops and tablets. With employees accessing sensitive data from various device endpoints, it becomes increasingly difficult to manage which staff have access to what information.
A zero trust security approach can be helpful. This approach requires users to undergo a verification process before being granted access to login credentials or financial information, adding an extra layer of security. For example, enabling Multi-factor authentication (MFA) for all remote login attempts, and IT teams can enhance security by configuring VPNs on work devices.
Senior executives may also address remote users by adopting zero trust network access (ZTNA), the strategy used behind achieving an effective zero trust model. ZTNA is also known as the software-defined perimeter (SDP), which aims to enable secure access to internal applications for remote users.
Integrating zero trust principles in AP and Finance
Zero trust security can be an effective approach for securing corporate data that requires continuous monitoring and authentication. It foregoes traditional perimeter-based security models, making it harder for cybercriminals to access sensitive information.
To get started with zero trust approaches, leaders will first need to look at:
Risk assessment
Identity and access management
Endpoint security solutions
Network security
Continuous monitoring and response
Risk assessment
The first step should be understanding your vulnerabilities. This involves conducting a thorough analysis of all possible risks that may threaten the organization's data security. Once these risks have been identified, it is necessary to prioritize them based on their impact and likelihood of occurrence. One eventuality might be a very small possibility but have catastrophic consequences—leaders will need to weigh all of these considerations against other factors like efficiency, employee autonomy, and user experiences.
Prioritizing risks enables organizations to focus resources on the most critical areas while establishing risk management protocols for lesser threats. These protocols should include measures such as access controls, MFA, and other security tools aimed at ensuring data protection across all endpoints.
Identity and access management
Implementing MFA, creating strong password policies, and regularly auditing user access are all part of ensuring robust identity and access management.
MFA adds an extra layer of security by requiring users to provide two or more forms of identification before accessing sensitive data. This builds stronger protection around user identity for employees—even if a password or other access information has been exposed, cybercriminals will need additional requirements to complete a login.
Creating strong password policies is another critical measure because it helps prevent unauthorized access from cybercriminals who often exploit weak passwords. Regular auditing of user access ensures that only authorized personnel have access to confidential information while limiting the risk of internal security breaches.
Endpoint security
Deploying endpoint protection software is crucial to maintaining zero trust security. It provides a layer of defense that can detect and prevent malware, ransomware, and other cyber threats from infecting devices within the network. To ensure maximum effectiveness, it's important to choose an endpoint protection software that fits your organization's needs.
Maintaining software updates for all devices is also essential in keeping them secure from known vulnerabilities. Regularly checking for and applying updates ensures that any newly discovered vulnerabilities are patched before they can be exploited by attackers. This process should be automated wherever possible to minimize the risk of human error.
Blocking unauthorized device connections helps prevent potential security breaches by limiting access only to authorized endpoints. This can be achieved through various methods such as implementing network segmentation or using tools like firewalls or intrusion prevention systems (IPS).
Network security
Automated alerts, ones that flag suspicious or unusual activity, can be a beneficial part of a zero trust framework. These alerts can be configured to notify you of any unusual behavior or attempted breaches in real time, allowing your team to respond quickly and effectively.
Along with setting up alerts, this model demands prompt investigation of security incidents. By investigating incidents as soon as they occur, organizations can minimize the scope and impact of potential data breaches. Conducting regular security audits also ensures that your systems are always updated with the latest patches and configurations, reducing vulnerabilities that could be exploited by attackers.
Choosing a zero trust security solution
Factors to consider
Implementing a zero trust security model starts with assessing your current security infrastructure, including:
Reviewing access controls and permissions
Evaluating network segmentation
Identifying potential vulnerabilities in existing systems
Another important factor to consider is which assets and data need protection the most. This includes:
Conducting an inventory of all company data
Categorizing data based on its importance and sensitivity levels
Implementing appropriate access controls for each category of data
Finally, analyzing potential threats and vulnerabilities is essential to create a successful zero trust security strategy. Consider the following:
Identifying common attack vectors
Assessing risks associated with third-party vendors
Regularly testing system defenses through penetration testing
Best practices
Implementing MFA for all users, enforcing strong password policies across the organization, and creating a centralized access control system are essential best practices for zero trust security. And, as a CFO, it's vital to incorporate these types of measures to protect your organization and its financial assets.
Here are some key points to keep in mind when implementing these best practices:
Implement MFA that requires at least two types of verification for each user login, such as a password and biometric scan or token code
Enforce strong password policies by requiring complex passwords that include uppercase letters, lowercase letters, numbers, and symbols
Create a centralized access control system that restricts user permissions according to their job responsibilities. This ensures that employees only have access to the information they need for their job function
By following these best practices, along with other zero trust security measures such as continuous monitoring and risk assessment protocols, you can mitigate some of the most serious cyber risks.
The bottom line
Despite which cybersecurity strategy or architecture your organization chooses, it’s worthwhile to note that zero trust models are the next evolution in security approaches—they no longer focus exclusively on preventing infiltration, they assume infiltration will happen and minimize risks from there. In many ways, it can be a more practical, realistic approach considering the larger attack surfaces of new hybrid working models.
Leaders in finance and AP can adopt similarly realistic approaches when shoring up defenses against financially motivated cybercrime. Even if your organization never suffers a breach, someone else in your supply chain likely will. A single errant click, performed by a single supplier’s employee, can be enough to circumvent your organization’s analog controls and help fraudsters scam your organization.
Along with working on zero trust approaches with IT or security teams, finance leaders should look to reevaluate, test, and potentially upgrade current approaches to financial controls. You can do this as part of a broader cybercrime strategy, one that protects what most cybercriminals are after: your money.
Looking for a good starting point? Reassess your segregation of duties policy, which is one of the most robust ways to minimize the fallout of a breach or scam attempt.