What Can Scammers Do with Your Phone Number?
When cell phones first became popular, no one thought they’d become what they are today. For the first few years, it was …
Real-time Transport Protocol or RTP detection refers to the identification, analysis and management of network traffic that is used to transmit audio, video and media in real-time.
Contexts where RTP detection is applicable include:
To better understand RTP detection, it is first important to explain Real-time Transport Protocol itself.
RTP is a network communication protocol that helps transport audio, video and media data instantaneously.
As such, it is present in many communication and entertainment systems where a media stream needs to be broadcast live or received by many users at the same time. Notable systems include Skype, FaceTime, WhatsApp, Zoom, Twitch and Microsoft Teams.
The protocol’s primary objective is the smooth and consistent delivery of data, and in the next section, we’ll take a look at how this is accomplished.
Packets and jitter are crucial concepts that dictate how well audio and video RTP streams are delivered over a network.
When Real-time Transport Protocol is used to transmit data, the data is sent in discrete bunches known as packets.
Think of each packet as a piece of data (such as a snippet of audio or video) that also contains other important information such as a timestamp and sequence number.
Packets are sent over the network to their destination, but due to the distributed nature of the internet, some packets:
Jitter refers to variation in the time it takes for packets to arrive at their destination.
In an ideal network, packets arrive at regular intervals. Often, however, some packets arrive quickly while others are delayed. If packets do not arrive as expected, jitter increases and it becomes more difficult for RTP to transmit a smooth and interrupted stream.
When jitter is pronounced, audio and video may be characterised by sudden pauses, distortion, static, echoes, repetition, pixelation, frozen frames and synchronisation issues.
Essential to RTP detection are two other protocols that work in conjunction with the Real-time Transport Protocol. These include:
Here are some of the practical ways the three protocols assist in RTP detection.
Quality of service (QoS) pertains to the qualitative measurement of the overall performance of real-time audio and video communication.
As hinted at earlier, the collection of QoS statistics is the domain of RTCP. Depending on the metric in question, the RTCP issues a report so that corrective action can be taken.
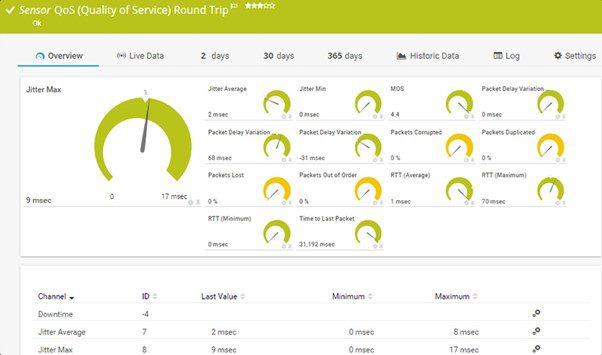
Let’s return to out-of-order delivery, packet loss and jitter with examples of how each is rectified.
In the case of out-of-order delivery, packets are sent to a buffer where the receiver reorders them according to their respective sequence number.
In this context, the receiver is the device, application or system that receives and processes data packets from the sender.
If a packet is lost and does not arrive, some RTP streams estimate or recreate the lost data based on the surrounding packets.
One technique – known as Packet Loss Concealment (PLC) – employs algorithms to repeat or interpolate data and make the disruption caused by missing packets less noticeable to the user.
RTCP uses a specific type of packet known as the Receive Report (RR) packet to measure jitter.
The RR packet contains a field specifically to measure jitter, which is calculated by measuring how much the timing of an audio or visual packet deviates from the expected interval.
Jitter buffers help smooth out variations in packet arrival time by temporarily storing them before they are processed. This ensures that packets are delivered at regular intervals despite network fluctuations.
Adaptive buffers can even adjust their size in response to network conditions. The size of the buffer increases and decreases during periods of high and low jitter respectively.
RTP detection helps system administrators and other security professionals manage the RTP traffic in a network.
Two important tasks help administrators clarify how many VoIP or video sessions have been established and what bandwidth is required to support them based on QoS standards.
These include:
To maintain consistent transmission of data, RTP traffic may also be prioritised over less time-sensitive data to ensure packets are delivered with minimal delay.
Adaptive streaming is also used in contexts where network conditions fluctuate. Here, systems detect when bandwidth is limited and can adjust the bitrate of a stream to ensure the transmission is not interrupted.
Network performance management has obvious benefits for the user experience and customer satisfaction. With the total number of 5G connections predicted to skyrocket to 7.9 billion by 2028, these benefits will become more important as both the volume of data and speed of data transmission increases.
RTP streams can also be vulnerable to various types of attacks such as eavesdropping, spoofing and denial-of-service (DoS) attacks.
RTP detection helps identify suspicious or unauthorized RTP traffic and enables the implementation of security measures such as encryption, intrusion detection and access control.
Security is especially important in environments where sensitive information is transmitted, such as in corporate communications, finance and telemedicine. In these and other VoIP contexts, SRTP encrypts the content of each RTP packet so that even intercepted data cannot be read without a key.
STRP also ensures that the data has not been modified during transmission. To do this, it generates a cryptographic hash for each packet that is checked by the receiver to ensure it is genuine and unmodified.
Summary:
When cell phones first became popular, no one thought they’d become what they are today. For the first few years, it was …
When Mr. Beauchamp watched a video of Elon Musk – the world’s richest man – recommend a certain investment platform to make …
Your company delivered the good or service it promised to a client and now it’s time to collect the funds owed to …
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.