How likely am I to be scammed? A guide to cybersecurity hygiene
In a world increasingly dependent on digital platforms, you may wonder how likely it is that you’ll fall victim to a scam.
The Procure-to-Pay lifecycle contains multiple steps, each of which may be vulnerable to human error or fraud. In order to ensure the security of your Accounts Payable processes, you need to implement a combination of manual and automatic controls from the outset of the lifecycle. Embracing a Shift Left approach will help ensure your Accounts Payable department functions effectively and efficiently, and will help secure your organisation from the risk of losses due to error or fraud.
Anyone developing an application knows there’s a constant tension between the need to roll-out software expeditiously on the one hand, and the need to ensure the software is secure on the other hand.
Market pressures often result in developers needing to write code and build functionality as quickly as possible. But, before any new or updated software can go live, it needs to be rigorously tested to ensure it is built securely and isn’t going to be vulnerable to attack by hackers.
The problem is that security testing can take a long time. Fixing any bugs that are discovered may take even longer. A business may face steep costs associated with retroactively fixing vulnerabilities, not to mention the costs of delaying the software’s launch.
For these reasons, developers have turned to adopting a Shift Left approach. The idea is that security considerations need to be embedded throughout the software development lifecycle. From the time an application is conceived, through every stage of its development, code and functionality are continuously checked to identify vulnerabilities, allowing them to be fixed rapidly. This saves developers time and money by ensuring software releases aren’t impacted by costly delays.
In the same way as a Shift Left approach can help deliver secure software, it can also be applied to ensure the security of your Procure-to-Pay lifecycle.
The Procure-to-Pay lifecycle comprises 8 stages:
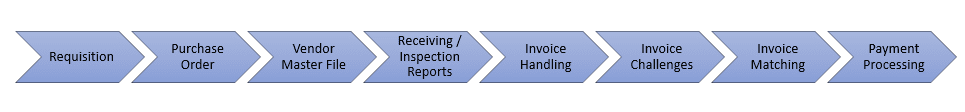
Potential vulnerabilities exist at each of these stages. If left unaddressed, these vulnerabilities could expose you to an increased risk of losses due to fraud or human error.
Rather than simply addressing security at the final stage of the Procure-to-Pay lifecycle, i.e., when you are about the process a payment, it is more cost effective and efficient to embed best-practice security measures throughout the Procure-to-Pay lifecycle. In other words, your Accounts Payable team should be confirming a supplier’s business identity, checking supplier compliance with regulatory requirements, ensuring the legitimacy of invoices, and verifying supplier banking information, on a continuous basis throughout each of the 8 steps above.
If done correctly, by the time it comes to process a payment, you should have strong assurance that the invoice is legitimate, and all payment details are accurate. This will allow your Accounts Payable department to operate efficiently, whilst reducing the risks of incorrect payments caused by fraud or error.
When it comes to implementing a Shift Left approach in your Procure-to-Pay cycle, it is best to adopt a combination of manual and automatic controls.
Implement manual checks to screen requisition request forms, so you can ensure all relevant information is included. Additionally, a line manager who was not involved in the screening process should be required to sign-off requisitions.
Implement manual approvals for all Purchase Orders by a finance manager who was not involved in the requisition process, to avoid internal fraud and ensure all relevant information is included.
When entering supplier data into your Vendor Master File, it is critical that compliance verification takes place and call-backs are conducted to legitimate banking information. Whilst continuous manual controls can be established to ensure all the data in your Vendor Master File is accurate and always up to date, this is resource-intensive and time-consuming. With eftsure, you can automate much of the verification process by cross-matching supplier data against our database comprising over 2 million Australian organisations.
Ensuring requisitioned goods and services are fulfilled as per the Purchase Order is critical before paying any invoice. Ensure manual checks are conducted by both the receiving department and the requisitioner prior to the release of funds.
Segregation of Duties is a manual control whereby different individuals are responsible for different steps of the process. This helps pick up any errors and makes internal fraud harder to execute. Have separate individuals encode invoice data into your ERP, verify invoice legitimacy, and approve invoice processing.
Incorrect or incomplete invoices must be identified and either corrected by the supplier or rejected for processing. AP Automation can assist with this process, however manual controls will be required to ensure issues are addressed with suppliers.
Before processing an invoice, manual controls need to be in place to ensure it matches the Purchase Order and the Receiving / Inspection Report.
To ensure your Accounts Payable department follows best practice procedures, you need to ensure you have Continuous Controls Monitoring in place. Data in invoices, ERP systems, Vendor Master Files, and text-based ABA files that are used to upload payments to online banking portals can be manipulated at any stage of the Procure-to-Pay lifecycle. Manipulation may take place by internal or external threat actors. With Continuous Controls Monitoring, you can ensure that data hygiene and accuracy are always maintained. The most effective way to achieve this is with an automatic controls tool such as eftsure. By cross-matching supplier and payment data against our database of over 2 million Australian organisations in real-time, immediately prior to processing a payment, eftsure provides you the assurance that your data remains correct and has not been manipulated. Attempting manual Continuous Controls Monitoring is both inefficient and ineffective, as it relies on manual spot checks only. Integrating an automated solution, such as eftsure, delivers significant advantages over manual alternatives and substantially reduces your risk of losses due to either fraud or human error.
By embedding a Shift Left security approach throughout the entirety of the Procure-to-Pay lifecycle, using a combination of both manual and automatic controls, you will be able to ensure that your Accounts Payable department functions effectively and efficiently.
It will help you ensure that only legitimate and accurate invoices are processed, avoid delays and mitigate the risk of losses through fraud or error.
The risks of attempting to ensure every invoice is legitimate and accurate at the end of the Procure-to-Pay lifecycle, when your team is processing supplier payments, is too high. Errors and data manipulation can occur at any stage of the process, which is why you need security controls at every stage. By adopting a Shift Left approach, you gain assurance that all outgoing funds are correct and being remitted to a legitimate recipient.
There are many steps in the Procure-to-Pay lifecycle. With error or fraud able to occur at any of these steps, implementing controls throughout the lifecycle is essential. The challenge is that many of these controls are manual in nature, which can be costly and time-consuming for your organisation.
eftsure is a unique solution that automates some of the most resource-intense controls in the Procure-to-Pay lifecycle. Having eftsure integrated into your processes ensures that your Accounts Payable team has the capacity to focus on other priorities, such as those controls which need to be conducted manually.
Contact us today for a full demonstration of the capabilities of eftsure and how it can help your Accounts Payable department adopt a Shift Left approach to securing your Procure-to-Pay lifecycle.
In a world increasingly dependent on digital platforms, you may wonder how likely it is that you’ll fall victim to a scam.
Accounting problems are issues that create a material financial statement error, hide fraud due to poor internal controls, stray from Generally Accepted …
Internal controls over vendor master file keep your data secure with clear rules, audit trails, and consistent oversight for long-term data integrity
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.