Only 1 in 10 finance leaders are ‘very confident’ they could stop an AI-powered cyberattack
Only 13% of finance leaders feel fully prepared for AI-powered cyberattacks. Discover where the real risks lie—and how to close the defense gap fast.
Cybersecurity incidents are becoming all too common. Companies, both large and small, are facing increased cyber threats that can lead to devastating consequences.
And the costs associated with those cyber incidents can range from financial losses to irreversible damage to a brand’s reputation.
As a chief financial officer (CFO), it’s crucial to take proactive steps to mitigate cyber security incidents. In this article, we’ll explore the best strategies you can implement to safeguard your business from cyber-criminals.
As a CFO, understanding the importance of cybersecurity incidents is critical to safeguarding your business. On average, one cyber-crime report is made every seven minutes according to the ACSC’s Annual Cyber Threat report.
This means that stolen information is exposed every year, like the information stolen during the Optus data breach – and that’s the exact sort of information that can be used against your organisation. Ultimately, cyber attacks can lead to significant financial losses, including theft of sensitive financial information, ransomware demands and loss of revenue due to downtime.
Once a cyber-attack occurs, it can be challenging to recover stolen information or funds. For senior executives, time is of the essence. It’s critical to have an organised and carefully planned cybersecurity incident report.
Cyber-criminals can use stolen information for a variety of purposes, including financial gain, identity theft and corporate espionage.
They may sell the stolen data on the dark web, use it to commit fraudulent activities such as opening credit card accounts, or even use it to gain access to a company’s internal systems.
Most crucially for CFOs and accounts payable (AP) teams, the information can be used to impersonate trusted contacts, conduct business email compromise (BEC) attacks and otherwise manipulate staff into revealing further information or making fraudulent payments.
In other words, even if a business has not experienced a data breach itself, the potential for future attacks is high and the consequences can still be severe. Let’s look at one example of how cyber-criminals used the stolen information to cause further data breaches.

On 30 September 2022, Energy Australia fell victim to a cyber-attack that affected hundreds of people. According to reports, cyber-criminals had breached the electric company through unauthorised online platform access.
This has exposed hundreds of customers’ accounts including their names, addresses, email addresses, electricity and gas bills, phone numbers and other sensitive information. The Chief Customer Officer, Mark Brownfield said, “We apologise for the concern that this issue may have caused our customers”.
The breach occurred mere days after those experienced by Optus and Medibank, in which “cyber criminals claim to have stolen 200 gigabytes of customer data from Medibank.”
What CFOs should take away is that cyber-crime is constantly evolving, and cybersecurity has to be at the forefront of their priorities in 2023. After a data breach occurs, cyber-crime does not stop. The loss of information from customers can be used against other businesses or, perhaps worse, sold on the dark web.
So what can you do about it?
As businesses become increasingly reliant on technology to facilitate operations and transactions, the need for robust cybersecurity measures becomes even more critical.
Cyber-attacks can result in reputational damage, financial losses, and legal liabilities, making it essential for business leaders to take proactive steps to minimise the risk of cybersecurity incidents. Here are some practical strategies that businesses can adopt to reduce their vulnerability to cyber threats:
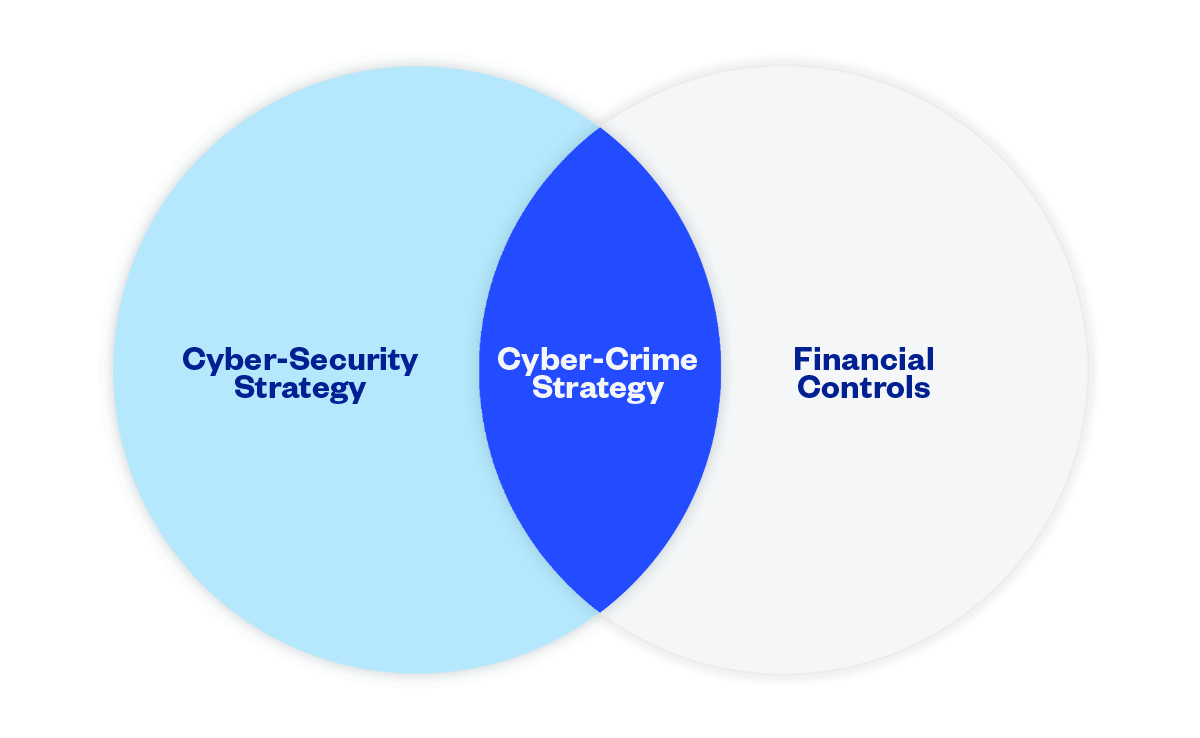
A robust cybercrime strategy includes a clear and concise security policy, outlining the alignment of financial controls and cybersecurity procedures that aims to protect the organisation’s finances and financial data.
Find out more about how to implement a cyber-crime strategy.
Multi-factor authentication is a security process that requires users to provide two or more forms of identification to access a system or network. This approach makes it more difficult for cyber-criminals to access sensitive information, even if they have obtained a username and password. In this free guide, find out more about MFA and why it’s necessary to include it as your first line of defence.
Encryption is the process of converting sensitive information into code that is unreadable without a decryption key. By encrypting sensitive data, businesses can protect data from unauthorised access even if there is a breach. This is particularly important for data that’s transmitted over the internet or stored in the cloud.
For senior executives, this is a useful tool to send sensitive emails through encrypted email messages. By integrating S/MIME (secure/multipurpose internet mail extensions) your email messages are protected through encryption or digital signatures. We explore further in our email security best practices guide.
Vulnerabilities in software and procedures can be exploited by cybercriminals to gain unauthorised access. It’s basic security hygiene to update software and systems, helping businesses protect themselves from known vulnerabilities. Software providers are constantly improving their software, this is due to a variety of reasons such as system bugs, vulnerabilities, system loopholes and more.
By updating your software and systems, you can stay up to date with the software provider’s defences.
Cybersecurity and anti-cyber-crime measures are critical for businesses to protect their data and designs from cyber-criminals. To reduce the risk of a cyber security incident, businesses must develop a comprehensive cyber security plan that includes security procedures, training and software.
As a CFO, it’s essential to prioritise cyber security and take proactive measures to safeguard your company and customer data. By combining your financial controls and cybersecurity strategy you create a cyber-crime strategy. This will mitigate the risk of cyber attacks, protect organisations’ reputations and avoid financial losses or legal fallout.
Want to learn more? Join our upcoming webinar on Thursday at 12PM – 1PM AEST April 20th where we explore what happens after a data breach and how it’s a problem for financial leaders.

Only 13% of finance leaders feel fully prepared for AI-powered cyberattacks. Discover where the real risks lie—and how to close the defense gap fast.
AI voice scams are targeting finance teams—using deepfake tech to mimic executives and authorise payments. Learn how they work—and how to stop them.
Discover 14 real-world AI-driven tax scams targeting US finance teams this season—what they look like, how they work, and how to stop them in action.
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.