Finance leaders and their teams are often on the frontlines of cybercrime since the vast majority of cybercrimes are financially motivated. Protecting your organisation’s money and reputation requires strong, up-to-date financial controls, but strong security practices – like the Essential Eight – help to prevent cybercriminals from breaching or infiltrating systems and infrastructure in the first place.
So what are the Essential Eight? They’re cybersecurity controls that make up a framework developed by the Australian Signals Directorate (ASD). When implemented correctly, they can significantly mitigate an organisation’s security risks.
In this article, we’ll explore the Essential Eight in detail, explain what financial professionals need to know about them, and outline how to work with your IT or security team to provide the best possible defense against cybercriminals.
Understanding the Essential Eight
Originally starting as a set of only four controls, the ASD has fleshed out its initial security guidelines into the Essential Eight – these serve as a baseline for mitigating businesses’ cybersecurity incidents. No set of mitigation strategies can guarantee complete protection against all forms of cybercrime, but the Essential Eight make it a lot more challenging for cybercriminals to compromise network systems.
The ASD has also provided the Essential Eight Maturity Model, a framework that helps organisations assess their cybersecurity posture and maturity. This framework illustrates the effectiveness of these strategies and offers a means for organisations to measure their implementation of the Essential Eight.
The Essential Eight is an excellent starting point for businesses with limited resources to enhance their cybersecurity posture. These essential controls are designed to be easily implemented and cost-effective, making them accessible to organisations of all sizes and budgets.
By adopting this framework, businesses can substantially reduce their risk of falling prey to cyberattacks. For instance, patching vulnerable software minimises the likelihood of attackers gaining access through known exploits, while regular backups ensure critical data is not lost in the event of a successful breach attempt.
As a finance professional, it's important to understand these strategies and work with your IT team to ensure your organisation is well-protected against cyber threats.
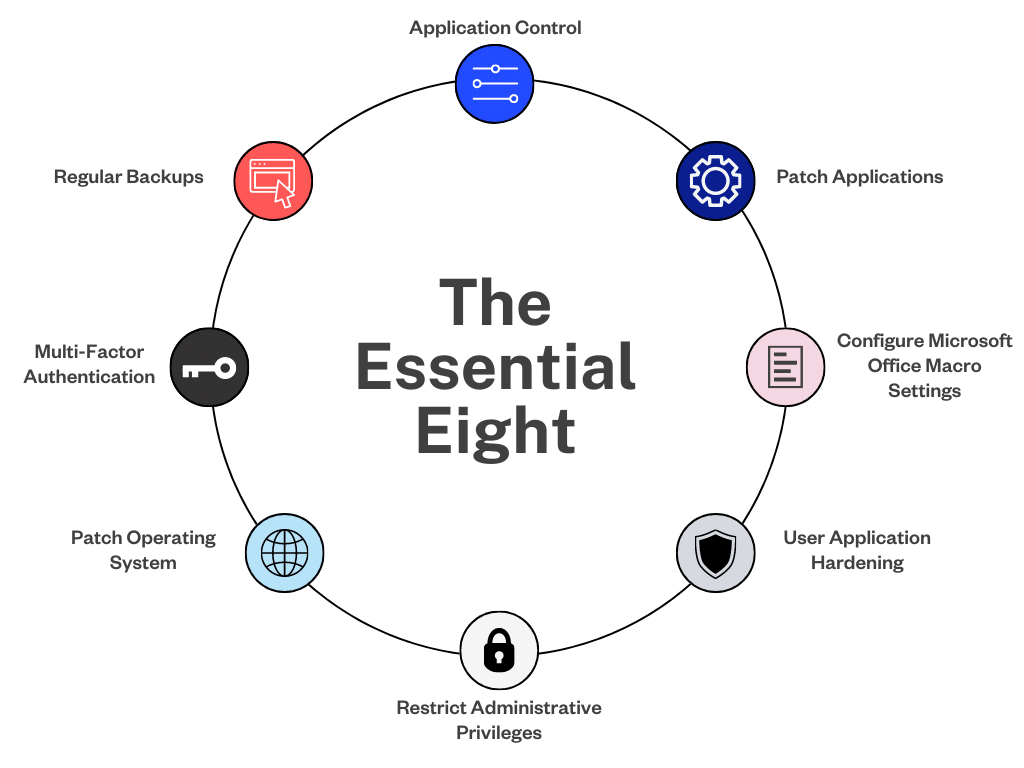
What are the Essential Eight security controls?
The ASD recommends using the Essential Eight as a foundation for securing Microsoft Windows-based, internet-connected networks. Designed to protect your IT systems and networks, the ASD provides different maturity levels for each control, meaning you don’t have to boil the ocean just to start implementing them, and you can continue enhancing the controls even after their initial implementation.
The controls’ main objectives are to prevent attacks, limit their impact, and secure data availability.
Application control. Implementing effective application whitelisting provides numerous benefits for securing IT systems and networks. By permitting only approved applications to run, you can lower the risk of malware or unauthorised software accessing sensitive data or causing damage.
Patch applications. Applying patches regularly can thwart cyberattacks that exploit vulnerabilities in software. Using automated patch management tools and techniques helps administrators keep their systems updated, saving time and minimising the risk of human error.
Configure MS Office macros. Macros help automate tasks within documents, but cybercriminals can exploit them to execute malicious code on your system. To reduce this risk, ensure that untrusted Microsoft Office macros are disabled while still maintaining document functionality. You can do this by either disabling all macros or allowing only those that have been digitally signed.
User application hardening. "Hardening" against intrusions means eliminating vulnerabilities within your operating system and common programs like web browsers or PDF readers. This could include limiting which users can download or install software or restricting certain aspects of an app without impacting your employee's core responsibilities (e.g., ad blockers can actually make it easier for employees to do their jobs).
Restrict administrative privileges. Limit administrative privileges to authorised personnel who need them for their job function. Restricting access to sensitive data can minimise unauthorised changes to information and decrease the risk of malware infections. Learn more about the principle of least privilege in our guide to zero trust security.
Patch OS systems. Administrators should assess which devices are most vulnerable and prioritise patching those first. Streamlining the OS patching process across multiple devices can be challenging, but automating updates and securing administrator accounts makes it more manageable.
Multi-factor authentication (MFA). This critical security measure requires users to provide more than one form of identification to verify their identity, such as an SMS code or a hardware token, in addition to their password. By using MFA instead of relying solely on traditional passwords, you greatly reduce the risk of unauthorised access to sensitive information or administrator accounts. Read more about MFA.
Regular data backups. Consistently backing up your data enables the swift recovery of valuable information in case of unforeseen data loss, whether due to cyberattacks or other issues like software corruption or human error. This is especially crucial as businesses become more and more reliant on digital data for everyday operations and strategic planning.
Once you have a grasp of these eight controls, your organisation can start assessing the best ways to tailor them to your business structure. So, what are the next steps?
Implementing the Essential Eight
To start checking your cybersecurity strategy against the Essential Eight, the ASD recommends conducting a four-stage assessment. This may require engaging with a security specialist experienced in conducting assessments for Essential Eight controls.
Those four stages are:
Assessing your current security posture
Identifying gaps
Engaging with security experts
Training employees on best practices
Assess your current security posture
Conducting a thorough inventory of your IT systems and networks, evaluating the effectiveness of your current security measures, and identifying potential vulnerabilities in your system are all vital steps for assessing your current security posture. This can help identify areas that need improvement and allow you to prioritise implementation accordingly.
Here are some important steps to keep in mind when assessing your current security posture:
Conduct an inventory of all hardware, software applications, and data
Evaluate the effectiveness of firewalls and antivirus programs
Ensure patches for operating systems, web browsers, and third-party apps are up-to-date
Implement password policies
Evaluate any relevant past security assessment reports
Identify gaps and prioritise implementation
Begin by examining your current cybersecurity posture. At this stage, an assessor should try to identify the most suitable maturity level for your organisation.
Review the Essential Eight guidelines thoroughly and determine which areas require improvement and identify gaps
Prioritise improvements based on which gaps are most likely to expose sensitive data or processes, as well as the level of resources available for each change
Develop a comprehensive plan for implementing changes that take into account budget, timelines, and needed skill sets
Remember that even with limited resources, taking action and incorporating the Essential Eight can provide your business significant protection against cyber threats – and those cyber threats can cost your organisation in a variety of direct and indirect ways. Don’t save a bit of money today only to sacrifice more money (and even your organisational reputation) later on. And don't hesitate to seek guidance from security experts if needed.
Engage with security experts
Consulting with an experienced cybersecurity specialist can help you get a clearer, objective understanding of your current posture and which changes to make. By assessing specific risk factors unique to your business, you can identify vulnerabilities and develop tailored strategies to mitigate cybercrime, such as reviewing and testing the effectiveness of controls.
The right specialist can provide support beyond initial assessments and implementation, too. For instance, they can help identify more efficient technical solutions that address ongoing vulnerabilities and offer proactive support against ever-evolving cyber threats.
Partner with security experts who will:
Assess specific risks unique to your business
Identify technical solutions that address gaps in defences
Provide ongoing support and guidance as threats evolve
Train employees on security best practices
Once assessments are complete, you can start developing a security assessment report and map out the timeline to train employees. Cybersecurity training workshops and promoting an anti-fraud workplace are key components of an effective cybersecurity strategy.
First off, educating employees should be tailored and interactive. Invest in training workshops focused on educating employees about cyber risks, phishing attacks, password management, and other best practices.
Additionally, you can minimise your risk of serious damage by encouraging staff members to promptly report any suspicious activity or potential breaches they notice. A strong security culture doesn’t mean that everyone has all the answers all the time – it means that employees aren’t afraid to put their hands up if an email looks dodgy or to swiftly inform a manager if they think they clicked on the wrong link. And incorporating basic security protocols like MFA across all devices and accounts adds an extra layer of protection.
To effectively train your employees on security best practices, consider incorporating the following into your training program:
Real-world examples of successful phishing scams
How to identify and avoid email scams
Techniques for creating strong passwords that are easy to remember
Best practices for securing personal devices used for work purposes
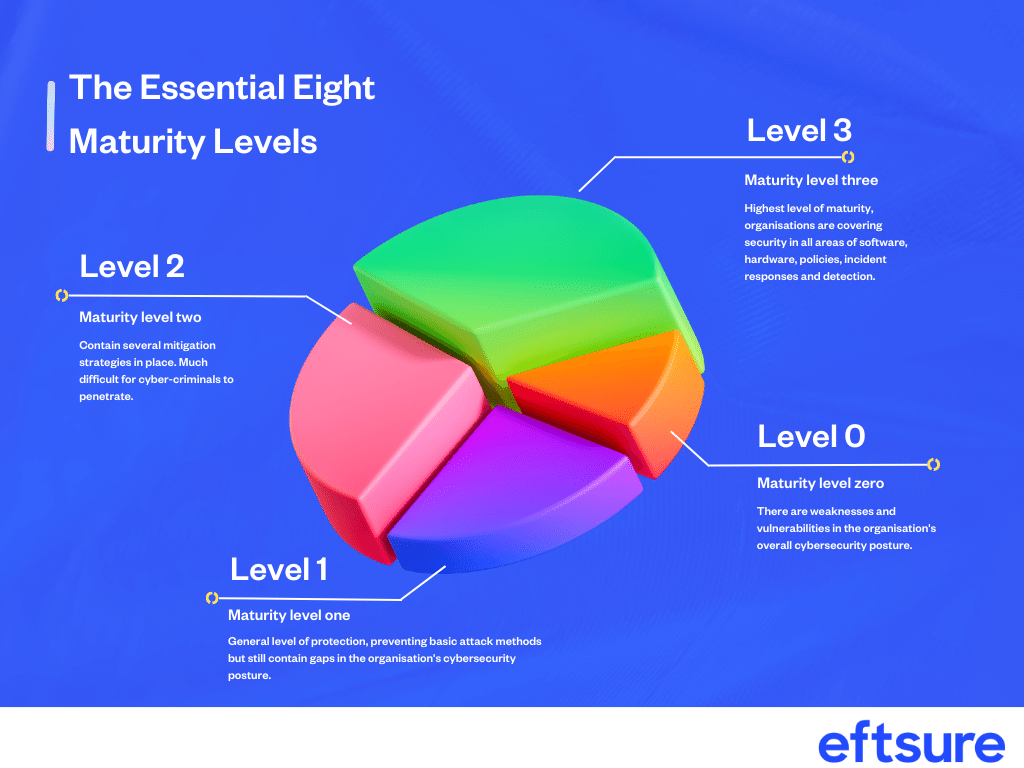
What are the Essential Eight maturity levels?
Once you have implemented the Essential Eight maturity model into your organisation, you can review the effectiveness of controls and begin working your way to increasingly mature versions of each control. Because the controls are designed to work together, organisations should aim to achieve similar levels of maturity across all eight controls.
The maturity model consists of four levels.
Maturity level zero. At this stage, organisations may have vulnerabilities in their cybersecurity measures that can be exploited by malicious actors using basic attack methods and tools.
Maturity level one. Organisations have basic standards of cyber-defense that can prevent cybercriminals using basic attack methods, but might still be vulnerable to next-level attacks such as launching malicious MS Office macros applications or unpatched software.
Maturity level two. Organisations have several mitigation strategies in place to prevent cyberattacks - to target organisations at this level, malicious actors would need to invest significantly more in tactics and tools that are not already widely known to the public.
Maturity level three. Considered the highest level of maturity, organisations are not only covering security of all areas of software and hardware but have integrated policies around information management, incident responses, roles and responsibilities, and detecting suspicious behavior.
Requirements for each maturity level are outlined in Appendices A to C in this maturity model whitepaper.
How can the Essential Eight benefit your organisation?
The Essential Eight is endorsed by government agencies, making them a trusted blueprint for strengthening your cyber defenses. And, if you’re a government agency, you might be required to implement them.
But it’s not just about whether the Essential Eight are mandatory – they have a few benefits that finance leaders should understand when working with security and IT teams.
They provide cost-effective protection
For small businesses, implementing budget-friendly security measures is crucial.
The Essential Eight provides an affordable solution that can protect against a range of cyber threats. In fact, dealing with a cyberattack can end up costing more than implementing the Essential Eight in the first place.
Real-life examples exist of companies like MobileCorp that have saved money by using these eight strategies and preventing costly data breaches and system intrusions. By choosing to implement the Essential Eight, businesses can achieve cost-effective protection against common attack methods without breaking their IT budgets.
They address common attack methods
The Essential Eight is a comprehensive framework that helps businesses protect their IT systems and networks against some of the most common attack methods. We know from cybercrime statistics that attack methods include popular tactics like phishing, BEC attacks, ransomware, and malware. Each method can cause significant harm to a business's IT system, resulting in data breaches, financial losses, or operational disruptions.
The strategies are recommended by the ASD to provide a more cost-effective method to respond to a large-scale cybersecurity incident. By implementing these strategies such as application whitelisting and patching applications promptly, businesses can significantly reduce their risk of falling victim to cyberattacks.
How can Eftsure help improve your cybersecurity posture?
Cybersecurity statistics demonstrate that cybercrime is an ever-growing threat to all businesses, no matter the size. As we’ve seen in the past with high-profile attacks like Optus and Latitude Financial, businesses of all sizes can fall victim to serious cyber incidents, making it important for every organisation to strengthen their cybersecurity strategies.
Using the Essential Eight as the foundation for your cybersecurity posture can help protect against data breaches and security threats. However, sophisticated cybercriminals continue to adapt and are always hunting for ways to leverage new technology against legitimate organisations.
To keep up with this threat, your cybersecurity strategy will also need to evolve.
That’s why it’s crucial that you combine your cybersecurity strategy and financial controls to create an effective cybercrime strategy. A cybercrime strategy allows you to align elements together like segregation of duties and email security, adding later-stage protections that protect your organisation even if cybercriminals manage to infiltrate your systems (or those of a supplier). This helps you protect your organisation from some of the most serious consequences of cybercrime and fraud attempts.









