A guide to cyberattack protection
On average, a cyberattack occurs every 10 minutes in Australia with small to medium enterprises (SMEs), education, healthcare and government the most …
Reports of phishing attacks are rising year over year, and increases in targeted attacks are even higher.
With more employees working from home – and more employees reporting burnout – malicious actors are finding fertile ground for phishing. It’s little wonder that 77% of organisations faced BEC attacks in 2021, according to Proofpoint.
So how dangerous is phishing, and what are the implications for finance professionals? What are the types of phishing attacks that CFOs need to be aware of in 2023? Let’s dive into phishing attacks and what you can do to combat this common cyber-crime tactic.
Phishing is a form of social engineering attack that is used to steal customer information, such as login credentials (usernames and passwords), credit card information, and email addresses.
Phishing attacks can target senior executives like CFOs or accounts payable (AP) clerks through spoofed emails, text messages, phone calls or social media platforms. Usually, phishing messages contain fake websites or malicious links that can be used to gain access to your organisation’s network or reveal sensitive information.
Depending on the type of organisation and size of your AP team, cyber-criminals have a variety of phishing techniques at their disposal.
Spear phishing occurs when a cyber-criminal targets a specific individual or organisation that requires more in-depth knowledge about its victim. Unlike a blanket phishing attempt, this is a tactic that zeroes in on one particular individual or group. Attackers often conduct extensive investigative research on their target, using publicly available information like events, recruitment material or social media.
An example of a spear phishing attack: your AP clerk receives an email impersonating your IT help desk, requesting to change their password as a routine security procedure. The email might even come at a time when the sender knows the AP clerk is more likely to be frazzled or ready to finish work, such as the end of the day or right before a holiday.
The email may seem genuine to the naked eye. The malicious actor can carefully craft an email that contains the organisation’s logo, a similar email address and a professional-sounding message that uses language or references they’ve picked up from their research. All of this can result in a convincing, authentic-looking message.
Similarly to spear phishing, whaling attacks are specifically targeted at top executives like CEOs, CFOs or CTOs. Cyber-criminals understand that senior management has high data access to sensitive data like customer information, company portals and other senior executives’ contact details.
These types of targeted email attacks usually contain malicious software or malicious code that allows attackers to gain control over your data and defraud your organisation.
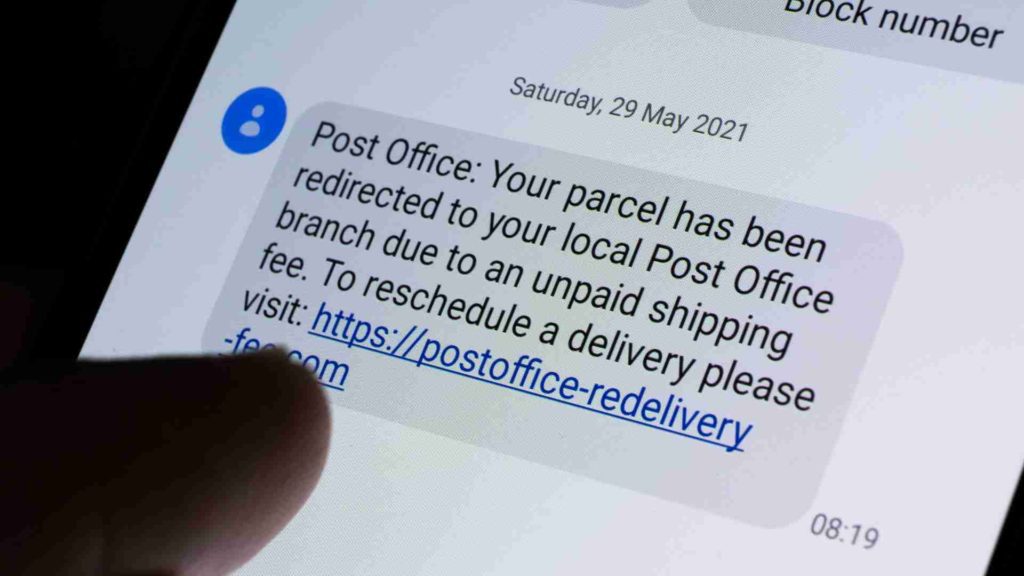
Another variant of phishing is SMS phishing, also known as “smishing.” This attack is carried out on mobile devices through fraudulent SMS/text messages. It can occur on various text messaging platforms like WhatsApp or Telegram.
Smishing attacks are known for bait messages that appear during busy schedules to catch you off-guard. Smishing was especially rampant during the COVID-19 pandemic, where attackers would impersonate government entities, hospitals or councils to send worrying text messages about vaccines or contact tracing.
Because this tactic seeks to take advantage of busy or stressful time periods, it’s also common for malicious actors to target AP teams during the end of the financial year period.
Other than text messages, attackers have the ability to conduct phone call scams, which is called voice phishing or “vishing.”
Like other types of phishing, this tactic uses psychological manipulation to fool victims into revealing sensitive information – often by creating a sense of urgency, a desire to help or gaining trust.
While many employees have been trained to spot suspicious emails, people may be more likely to trust the sound of a human voice. Especially as deep fake technology continues to improve, it’s crucial to ensure staff are aware of vishing threats.
In November 2020, the co-founder of Australian hedge fund Levitas Capital was targeted with a whaling attack. Starting with a malicious Zoom link in the phishing email, fraudsters gained access to the hedge fund’s email system.
This allowed the attackers to impersonate the co-founder by sending fake email instructions to process illegitimate payments. As a result, the attackers stole over $1.5 million in funds using fraudulent invoices. Unfortunately, indirect costs crippled the organisation, forcing the hedge fund to shut down.
In early November 2018, the Australian National University (ANU) fell victim to a sophisticated spear phishing attack. In fact, the spear phishing email didn’t even contain any malicious link or attachment.
The ANU confirmed that the sophisticated threat actor gained unauthorised access to the Enterprise System Domain (ESD) network which housed their human resources, financial management and enterprise e-forms systems.
Vice-chancellor Brian Schmidt commented on the data breach, saying, “This wasn’t a smash and grab, this was a diamond heist.”
Financial leaders and accounts payable teams should be highly sceptical of emails and websites that purport to provide information or goods. As you can see in some of the phishing examples above, cyber-criminals don’t always need their victims to click on a malicious link or attachment anymore.
Phishing is a serious threat for organisations and their AP teams. This is due to:
The Australian Competition and Consumer Commission (ACCC) found that the top three most reported scams were phishing (50,015) reports, false billing (16,263) reports and online shopping scams (13,068) reports.
Phishing statistics further demonstrate that the cost of phishing attacks can amount to over $3.2 million. Why so much? Other than the direct costs that organisations face, these sorts of cyber-attacks and cyber-fraud can cause reputational damage, regulatory fines and loss of data.
Cyber-crime’s cost of chaos is real. And a simple phishing email is enough to cause severe consequences.
You can protect your AP team from taking the bait. This often requires a comprehensive cyber-crime strategy, one that looks at three main elements: people, processes and technology. And CFOs are best-positioned to lead a cyber-crime strategy in their organisation – find out how to develop and implement your own.
But there are also some basic rules of thumb to spot and prevent a phishing attack:
On average, a cyberattack occurs every 10 minutes in Australia with small to medium enterprises (SMEs), education, healthcare and government the most …
Crowdstrike outage aftermath: Government warnings, scam attempts, and essential steps to safeguard your business from cybercriminals.
See how a Rite Aid data breach compromised 2.2M customers’ data through an elaborate impersonation attack. Learn about the risks and preventive measures.
End-to-end B2B payment protection software to mitigate the risk of payment error, fraud and cyber-crime.