Payment Security 101
Learn about payment fraud and how to prevent it
As the threat of cybercrime continues to escalate in Aotearoa, or New Zealand, greater awareness and preventative measures are crucial. According to the latest Cyber Security Insights 2022, CertNZ recorded an average of 2,166 reported cyber security incidents per quarter, averaging a loss of NZ$4.5 million per quarter.
This is alarming for both individuals and businesses. With a marked increase in cyber-crime reports, the problem appears to be getting worse.
As an executive, you understand the potential for cyber attacks to hurt your business, whether financial losses, reputational damage or data theft. To mitigate those risks, you’ll need a robust cyber-crime strategy, including training to educate your employees on best practices.
In our cyber crime statistics below, we delve into the current state of cyber crime in New Zealand, along with cyber-criminals’ most common tactics. By staying informed on the latest trends and statistics, you can equip your business with the necessary tools to protect against potential cyber threats.
The cybersecurity government body CERT NZ reported 8,160 cybersecurity incidents in 2022. This included individuals, small-to-medium enterprises (SMEs) and large organisations from all over New Zealand. While financial losses have grown exponentially over time from 2017, the number of reported incidents has slowly decreased since 2021.
Phishing and credential harvesting have become the biggest loss for cybersecurity incidents in New Zealand due to several factors. One of the reasons is the increasing reliance on technology for business operations since the COVID-19 pandemic. This has led to a larger attack surface for cybercriminals to exploit, often using phishing techniques to gain unauthorised access to sensitive information.
Scams and fraud accounted for almost $17.1 million (86%) of the overall direct financial loss in 2022. This is further broken down where $5.9 million went to scams involving unauthorised money transfers, $3.3 million went to dating or romance-related scams and $3.1 million went to scams involving a new job or business opportunity offer.
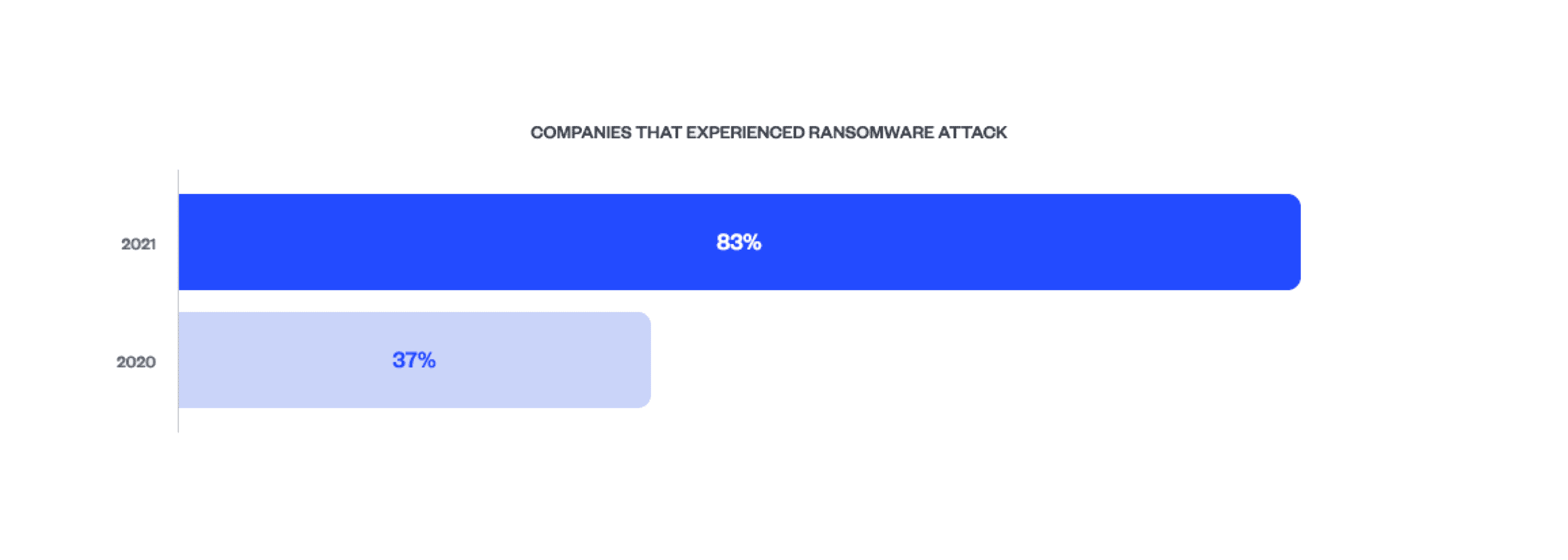
According to cyber-crime reports, ransomware is becoming more common around the world, impacting New Zealand, Australia and the United States all at the same time. Some of the most well-known ransomware strains include Bad Rabbit, CryptoLocker, Jigsaw and Ryuk. Generally, a ransomware attack occurs when the cyber-criminal encrypts a targeted individual’s computer and demands a ransom to be paid to recover their files.
Lisa Fong, NCSC Deputy Director-General says, “It is likely that the Russian invasion of Ukraine has meant both criminal actors from the region, and other significant global threat actors are more focused elsewhere than on activities that have previously impacted New Zealand.”

It’s no surprise to see that the financial and insurance services industry is the most targeted by cyber-criminals. These industries deal with large amounts of sensitive and valuable information such as credit card details, email addresses, names, and other financial records. Cyber-criminals find this type of information highly lucrative and profitable for identity theft and other illegal activities that can be used for financial gain.

Apache Log4j is a popular open-source logging framework used by developers to generate log files in Java-based applications. According to the Cyber Threat Report 2021/2022, NCSC discovered a vulnerability issue in Log4j which left global networks vulnerable to malicious cyber actors remotely accessing systems, stealing confidential information and more.
IDCARE is a not-for-profit organisation that looks after Aussies and Kiwis, providing free and confidential support to individuals who have experienced identity theft or cyber-related crimes. If you fall victim, IDCARE can assist you with personalised support and advice on recovering your identity and developing an identity recovery plan, as well as offer advice on any associated risks.
One of the reasons why SMEs fall victim to cyber-crime is the lack of resources. SMEs often have limited resources for cybersecurity measures and may not have the budget to invest in robust security software or hire dedicated security personnel. However, there are other ways of mitigating risk, like implementing multi factor authentication (MFA) methods of encrypting sensitive information.
New Zealand is a growing target for cyber-criminals. With more Kiwi businesses falling victim to phishing, credential harvesting, scams and unauthorised access attempts, cyber insurance premiums are increasing. Senior Broker Anna Parker from Frank Risk Management comments that businesses need to be careful about their insurance covers, as each insurer may or may not cover the full amount of cyber attacks.
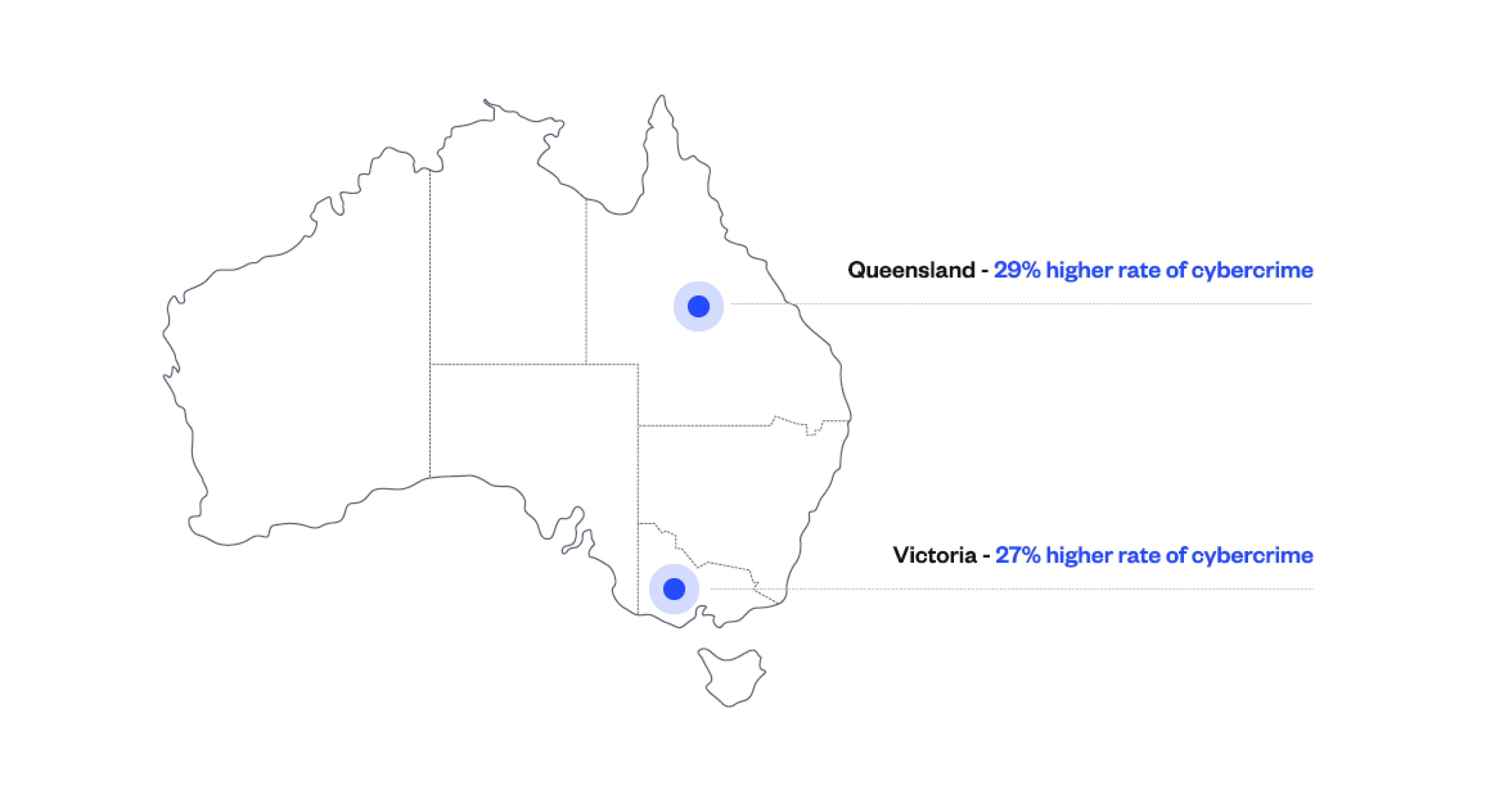
Auckland is the largest city in New Zealand and has a high concentration of businesses, government agencies and other organisations. This may be one of the reasons why it’s an attractive target for cybercriminals who seek to steal or reveal sensitive data. CERT NZ also states that Auckland has had the highest financial loss to online scams and fraud from June 2019-2020 with a total loss of $5.4 million.
While business email compromise (BEC) scams and unauthorised access are different types of cyber threats, they can both be used in a cyber attack. For example, a cybercriminal may use unauthorised access to gain access to an email account of an employee or executive, which they can then use to launch a BEC attack. They could send an internal email impersonating the CEO to deceive employees into committing fraudulent activities.
Imposter scams or impersonation scams are a type of BEC attack. Imposter scams involve a cyber-criminal impersonating a trusted individual or organisation, such as a senior executive or supplier. This allows criminals to trick targeted individuals into transferring money or providing credentials to gain access to accounts to reveal information.

According to abnormal security, the average cost of a BEC attack in 2021 was around $120,000, while 35% of cyber-crime losses stem from BEC. Crane Hassold, director of threat intelligence at Abornal Security noted that “any time an employee has to assess whether an email is malicious, [it’s] an opportunity for them to make a mistake”.
Email is the most used communication method due to several reasons. One of them is anonymity. Email allows criminals to remain anonymous or use fake identities, making it easier for them to avoid detection and impersonate trusted brands or individuals. If you are looking to secure your email security, check out our email security best practices.
It’s important to increase awareness of BEC attacks in the workplace. Many employees may not be aware of what a BEC attack is or how to recognise one. It’s important to promote a cybersecurity culture that recognises the risks of such attacks and empowers employees to put their hands up when something doesn’t seem right.

Businesses that are looking to mitigate the risk of a BEC attack can do so on the CERT NZ website. CERT NZ provides solutions around keeping software up to date, deploying complex passwords and adopting antivirus software to combat the threat of BEC attacks.
Identity theft is a type of cyber-crime where malicious actors steal an individual’s personal information such as their name, address and financial information to commit fraud or illegal activities. The consequence of identity theft can be severe to organisations, including financial loss, reputational damage and loss of customer trust.
Cyber-crime statistics show that the most commonly compromised information in New Zealand is identity documents. Passports are on top of the list, with 21.2% of NZ cases handled by IDCARE involving stolen passport numbers. This is followed by the driver’s licence category at 19.7%. Individuals and businesses are not doing enough to mitigate the risk of identity theft, we cover the 7 steps that you can take to act now.
Cyber-criminals are using phone calls to carry out identity theft scams by impersonating trusted companies like your bank or email software provider. In some cases, they may get you to reveal your information by pressuring victims. They may claim that there is an urgent issue with the victim’s account or that they need to verify your account to prevent fraud.
For individuals, you can monitor your credit reports and bank and credit card statements for suspicious activity. You can contact IDCARE for more assistance if you suspect your identity has been stolen. For organisations, you should consult your IT teams for any signs of unauthorised access or unusual activity.
Not all New Zealand businesses are doing enough to mitigate their risk of cyber-crime. But it’s the responsibility of every business to adopt best practices for protecting their data and systems, especially since vulnerabilities in one organisation can impact every other organisation in a supply chain or network.
Phishing attacks typically involve sending fraudulent emails or messages that appear to be from a legitimate source but contain links to fake websites or attachments that contain malicious software (malware). Phishing is a type of social engineering tactic commonly used by cybercriminals. Other than phishing, individuals and businesses may also fall victim to baiting, scareware or pretexting.
One way cyber-criminals use phishing is by creating look-a-like email addresses that appear to be from a colleague or supplier. This could contain links to a fake invoice or requests to provide information. Fake emails are low-cost and effective for criminals.

MITRE adversarial tactics, techniques and common knowledge (ATT&CK) framework is a curated knowledge base and model for cyber adversary behaviour. By mapping recorded incidents to MITRE ATT&CK, the NCSC gained insight that the most commonly recorded known method of gaining access to a network was by exploiting a public-facing application.
It can be relatively easy for criminals to deceive your employees into clicking on a phishing link, especially if the email or message appears to be a trusted source. To mitigate this risk, you must verify the authenticity of the sender before entering any information or clicking on any links/attachments.
Ransomware is a destructive attack for organisations, particularly because it locks down the victim’s computer systems, making them inaccessible until a ransom is paid to the attacker. This can cause major disruption in business operations, loss of revenue, decreased productivity and more.

When it comes to ransomware attacks, the reality is that it’s difficult to accurately determine the number of businesses that have been targeted and the full extent of the damages caused. This underscores the considerable difficulties faced by businesses, cybersecurity experts and government officials in grappling with the consequences of cyber-crime in the country.

CERT NZ reports that at least 65% of cybersecurity incidents could have been prevented by two-factor authentication (2FA). You can incorporate 2FA by creating a strong and unique password that involves special characters, letters and words, as well as another method of authentication such as text message or email.
Botnets are often created by infecting large numbers of computers with malware, which allows the attacker to control the targeted computers remotely and use them for various activities. This might include sending spam or launching a denial-of-service (DDoS) attack. The botnet is used to distribute malware to carry out a ransomware attack.

According to the NCSC, their ability to detect and prevent cyber-attacks has resulted in avoiding or minimising damages worth NZ$119 million for critical organisations in NZ over the past year. They attribute much of their success to the Malware Free Networks service, which involves sharing threat intelligence with partners including internet service providers.

Cybercrime is any criminal activity that involves using computers, mobile devices or other electronic devices for purposes such as fraud and theft. Cybercriminals use digital devices to attain access to a user’s personal information.
Cybercrime is a serious issue that individuals and businesses are still struggling to combat. There are many different types of cyber crimes and they all continue evolving, such as business email compromise, business identity theft, ransomware, malware, phishing, social engineering, phone scams & more.
According to the CERT NZ 2022 report summary, New Zealand individuals, small and large organisations have reported a combined financial loss of $20 million from cybercrime.
CFOs have a fiduciary duty to safeguard their organisation’s finances. With cyber-crime representing an increasingly significant risk to those finances, it’s important to implement digital controls. Not only are finances affected but also increase insurance premiums, impact credit rating & valuation, cost of business disruption, reputational costs and impact cash flow.
A sub-committee of the board should be established with all relevant executives to ensure comprehensive staff training programs, appropriate policies and internal controls, and technologies are adopted organisation-wide to help prevent losses from cyber-crime.
In most cases, cyber criminals’ objective is to attain financial gain from either individuals or businesses. This is achieved either by gaining access to types of data such as financial information (credit cards, invoices, bank details) company information (emails, usernames, passwords) and more.
Eftsure provides continuous control monitoring to protect your eft payments. Our multi-factor verification approach protects your organisation from financial loss due to cybercrime, fraud and error.