How to Prevent Cybercrime
Cybercrime is an ever-evolving threat that affects individuals, businesses, and governments worldwide. As cyber crime continues to escalate and evolve due to …
The finance industry is extremely susceptible to data breaches. In fact, in 2023, it was the most breached industry and accounted for 27% of all incidents handled by financial risk and advisory firm Kroll.
These breaches are also expensive. Indeed, financial companies lose an average of $5.9 million per breach which is 28% higher than the global average.
If you’re a finance professional and your data has been compromised, a swift and strategic response to any incursion is crucial.
In this post, we’ll outline the steps you should take (and the processes you need to be aware of) to do just that.
Once you have discovered a breach or suspect that one has occurred, immediate action should be taken to limit further damage.
Resist the urge to solve the right problem right away. Instead, focus on containment and identify the security vulnerability that caused the breach.
This process involves several key steps:
What’s more, be careful not to destroy any evidence that may hold the key to identifying the cause (or perpetrators) of the breach later.
When a data breach occurs, it’s essential to assess the situation quickly and accurately. This involves determining the scope of the breach, the type of data compromised, and the potential impact on individuals and organizations. To assess the situation, follow these steps:
By assessing the situation quickly and accurately, you can take prompt action to mitigate the damage and prevent further unauthorized access to sensitive information.
Securing your operations is critical to preventing further data breaches and protecting sensitive information. To secure your operations, follow these steps:
By securing your operations, you can prevent further unauthorized access to sensitive information and reduce the risk of identity theft and financial loss.
If you’ve received notification of a breach, it is important to verify the notification’s authenticity. This step can be performed in parallel with step one. This step is crucial for data breach victims to ensure they are taking the right steps to protect their information.
Why is verification necessary?
Scammers frequently use fake breach alerts in phishing scams. Therefore, it’s important to contact the entity involved (via official channels such as their customer service number or website) to confirm that the breach notification is authentic.
To verify whether your email has been compromised, you can also use eftsure’s Data Breach Checker and receive additional tips and advice on how to protect data.
Step three involves assessing the data breach, whether it’s a small incident or a massive data breach, to help understand the risks it poses and how those risks can be mitigated.
Gather as much information about the breach as possible and do so while the details are fresh.
Each assessment should cover:
All data breaches require swift internal communication to minimise the risk of further exposure, but this is particularly important in finance. This is particularly important in finance, where multiple data breaches can have compounded effects on both the organization and its clients.
Reports make management, legal and security teams aware of the breach so that further action can be taken. The protocols themselves also clarify how breaches are documented, investigated and reported to third parties.
The consequences of non-adherence can be immense. In 2017, credit agency Equifax suffered a data breach that exposed the personal details of around 163 million people.
Hackers worked for 76 days before they were detected, and when Equifax did discover the breach, it failed to comply with internal and external reporting protocols. The company was ultimately ordered to pay up to $425 million in damages to those impacted by the data breach.
Notifying affected parties is a critical step in responding to a data breach. This includes notifying individuals whose sensitive information was compromised, as well as relevant authorities and regulatory bodies. To notify affected parties, follow these steps:
By notifying affected parties, you can help prevent identity theft and financial loss, and demonstrate your commitment to protecting sensitive information.
As a finance professional, you may manage multiple accounts such as workplace systems, banking platforms and investment accounts.
In step five, monitor the above-mentioned accounts for suspicious activity on an ongoing basis, and consider using credit monitoring services to automate this process. Update the passwords for each (and not just those directly impacted by the breach) and remember to do so with robust password hygiene.
Also enable two-factor authentication (2FA) where possible to ensure that hackers cannot access other areas of compromised systems.
In step five, monitor the above-mentioned accounts for suspicious activity on an ongoing basis since criminals may wait weeks or even months before they act.
Reporting the breach promptly can help mitigate the risk of identity thieves exploiting the compromised information.
It may also be pertinent to monitor:
If the breach impacts banks, credit card providers, investment firms or other customers, it should be reported to them as soon as possible. It’s also vital to discuss remediation options and be upfront and transparent about what data was compromised.
Notify credit bureaus: Notify the three major credit bureaus (Equifax, Experian, and TransUnion) about the breach, and request that they place fraud alerts on affected individuals’ credit reports.
In Australia, the Notifiable Data Breaches (NDB) scheme requires organisations with more than $3 million in annual turnover to report data breaches if there potential to cause serious harm to affected individuals. A report must also be sent to the Office of the Australian Information Commissioner (OAIC). In addition to notifying the OAIC, it is also important to notify the three credit bureaus to ensure comprehensive protection for affected individuals.
In the notification process, organisations must consider:
Phishing attacks are a common precursor to data breaches, but in some cases, the process is reversed.
After a data breach, compromised data may then be incorporated into targeted phishing attacks such as:
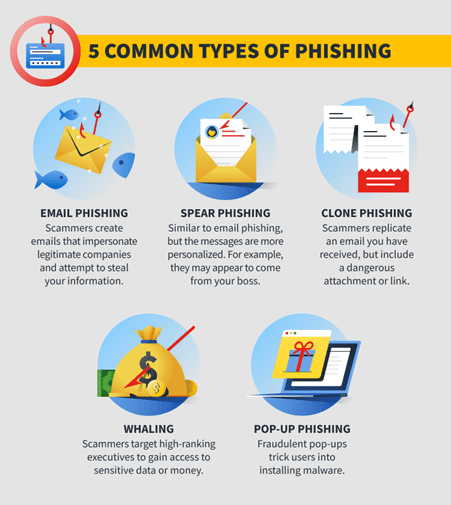
Targeted phishing attacks are particularly dangerous after a data breach because they exploit the trust and familiarity associated with legitimate communications. This is why it’s crucial to remain vigilant for suspicious activity in the period after a data breach.
Once a breach has been identified and properly remediated, the strengthening of cybersecurity measures becomes a priority.
Here are just two of the actions you can be involved in.
Cybercriminals often exploit outdated security devices to infiltrate networks, so keep your defences current to block malicious activity.
In finance, robust firewall configurations and proactive malware detection are essential. Set up automatic updates for security solutions so that your details (and the business’s assets) are better protected against the latest threats.
Training employees on cybersecurity best practices is essential to prevent future incidents. Staff should be encouraged to develop a security-first mindset that can:
Education also helps foster the sort of workplace culture where staff are encouraged to immediately report data breaches to their superiors.
If you’ve been involved in a data breach as a finance professional, the importance of swift and decisive action cannot be understated.
Start by confirming the validity of the breach and check for compromised email addresses with eftsure’s Breach Checker tool. Then it is a matter of changing passwords, enabling two-factor authentication and monitoring the relevant accounts for suspicious activity.
Regularly check your credit report to detect any unusual activity and take prompt action if necessary.
In the aftermath of a breach, be wary of increased phishing activity and ensure that you’re following recognised internal and external reporting protocols.
By following these steps, you can play your part to protect the company’s assets and the personal information of its staff and customers.
Cybercrime is an ever-evolving threat that affects individuals, businesses, and governments worldwide. As cyber crime continues to escalate and evolve due to …
Discover 7 proven steps to safeguard your business from online payment fraud—essential reading for finance leaders facing rising scam risks.
Unsure if a supplier is legit? Learn how finance teams can verify vendors and avoid scams with practical checks that protect payments and reputation.
End-to-end B2B payment protection software to mitigate the risk of payment error, fraud and cyber-crime.