What is vendor management?
Vendor management is the act of ensuring that your third-party vendors meet regulatory requirements and contractual obligations. This safeguards your business from …
Identity threat detection and response (ITDR) is a broad framework that protects user identities and identity-based systems from cyber threats.
ITDR relies on a combination of advanced detection techniques and rapid response strategies to safeguard sensitive data.
As cyber criminals shift their focus from firewall breaches to attacks that comprise user credentials, IDTR helps businesses understand the nuances of identity threats and their importance as part of a broader cybersecurity plan.
The sophistication, diversity and volume of identity-based attacks have left many businesses unprepared and exposed.
The level of concern around these attacks was made clear by Gartner when it identified IDTR as its top security trend for 2022. The research firm explained that “acceleration of credential misuse continues, leading to a tragic increase in security incidents” and “more-sophisticated attackers are now actively targeting the IAM infrastructure itself.”
CrowdStrike’s Global Threat Report, also from 2022, found that 80% of all cyberattacks leveraged identity-based techniques to evade detection. The company’s subsequent release in 2023 also reported that criminal use of stolen credentials had increased by 112% over the previous 12 months.
The speed with which cyberattacks are carried out is also on the rise. The average breakout time – or the time it takes for a criminal to exploit a system and position themselves to attack – fell to just 62 minutes in 2023.
While criminals are ready to cause harm in a little more than an hour, businesses take far longer to detect a compromised system. Mandiant, a cybersecurity-focused subsidiary of Google, reported that despite recent improvements, the median detection was a much more pedestrian 10 days.
The most effective IDTR approaches are multifaceted and utilise a combination of technology and best practices to:
Let’s take a look at how the above is achieved in practice via three key elements.
At the heart of prevention are robust controls that protect the IAM infrastructure. These controls identify, prioritise and even rectify identity-related vulnerabilities before they can be exploited.
Similar to a traditional risk management approach, IDTR provides an overview of the risks associated with each of the company’s identity assets.
MFA requires users to verify more than one form of identification. This could take the form of a push notification from an app or biometric (passwordless) authentication from a facial scan.
As part of continuous authorisation, a user’s identity and access privileges are evaluated in real-time and not just at login or periodically.
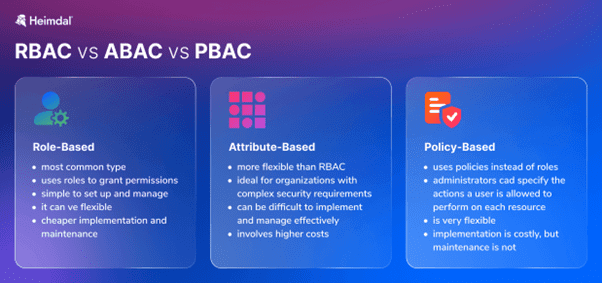
Central to this process is role-based access control (RBAC) and attribute-based access control (ABAC), where employee access privileges are defined by authority level, responsibility, job title and status.
Some organisations may also opt to use policy-based access control (PBAC) if they desire a flexible, context-driven approach. PBAC is an effective enforcer of granular access control policies and can also support risk-based decision-making.
IAM frameworks must also incorporate AI and machine learning to monitor login requests for anomalies and identify threats.
To assist with ITDR, machine learning algorithms deploy user and entity behaviour analytics (UEBA) to look for anomalies in not only user behaviour but also a corporate network’s servers, routers and endpoints.
Ultimately, enterprise-wide deployment of AI and ML enables businesses to leverage the full data analysis capabilities of these technologies.
With this deployment, the company has a centralised point from which it can control levels of access, monitor user activity and detect anomalous behaviour.
In an IDTR framework, controls alert key personnel the moment a possible breach or risk to the organisation has been detected. These controls help identify and manage risks that cannot be prevented and allow personnel to respond quickly and accurately.
Here is how threat detection is facilitated:
Effective identity protection requires the ITDR and IAM infrastructure to communicate with each other in a coordinated effort. This is otherwise known as interoperability.
However, if the data or the infrastructure has been comprised, there are some ways the organisation can respond:
As a framework, identity threat detection and response encompasses various processes, tools and best practices.
Note that it does not replace other security tools that form the backbone of IAM such as:
Instead, think of the ITDR framework as an additional layer of security that provides a business with advanced threat detection capabilities.
So what does advanced identity management and detection look like?
ITDR frameworks allow the business to take proactive measures on privileged account identities that are either misconfigured, unmanaged or exposed.
Misconfigured identities are those that have been set up incorrectly or inadequately.
An obvious example is an identity that is established with a weak password or encryption. Service accounts with privileged access granted to machine identities may also be misconfigured to allow humans to log in.
Unmanaged identities describe user or service accounts that are not properly maintained, controlled or overseen.
Orphaned accounts are one such example. These are accounts that remain active despite being associated with an individual or service that either no longer exists or is no longer in use.
Since orphaned accounts are not regularly monitored or updated, they may be targeted by criminals.
Exposed identities are those that have been maliciously or inadvertently made accessible to unauthorised individuals.
Credentials are often leaked or stolen in data breaches, but cached credentials stored in an endpoint’s memory are also a weakness in identity security.
One other example is a remote application session that has not been closed. In this case, an attacker leverages the open session and its privileged access to cause harm.
In summary:
Vendor management is the act of ensuring that your third-party vendors meet regulatory requirements and contractual obligations. This safeguards your business from …
Multi-factor authentication (MFA) is a security method that requires users to prove their identity using two or more distinct factors before accessing …
Imposter scams are a type of fraud where scammers pretend to be trusted individuals, companies, or government agencies to deceive victims into …
End-to-end B2B payment protection software to mitigate the risk of payment error, fraud and cyber-crime.