What Can Scammers Do with Your Phone Number?
When cell phones first became popular, no one thought they’d become what they are today. For the first few years, it was …
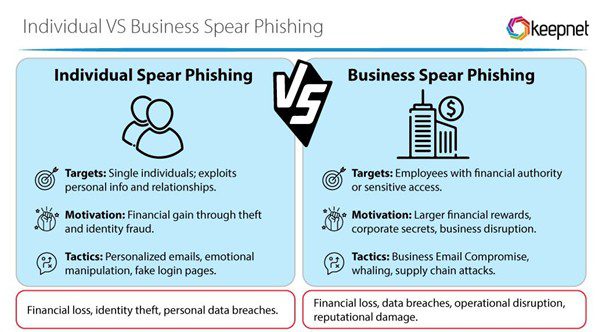
Spear phishing is a targeted cyberattack where personalised emails are crafted and then sent to deceive specific individuals within organisations.
These attacks are most often associated with email, but they can also occur via text messages, telephone or chat apps.
The objective of a spear phishing attack is to convince the recipient to send money, divulge sensitive information or perform actions that compromise their (or the organisation’s) security.
Spear phishing scams are low-volume but high-impact. In a 2023 analysis of over 50 billion emails, enterprise security firm Barracuda found that despite accounting for less than 0.1% of all emails, spear phishing was responsible for 66% of breaches.
Spear phishing is a sophisticated technique where criminals conduct extensive background research on an intended victim and then craft emails that are personal and persuasive.
What’s more, emails often appear to come from known or reputable sources such as coworkers, business partners and upper-level management.
By leveraging personal details and other contextual information, spear phishing emails may bypass standard security measures and exploit the human tendency to trust senders who appear authentic.
Here’s how it works in practice.
Most spear phishing attacks have one or more of the following objectives:
The choice of victim depends on the objective of the attack. In general, however, the victim is someone who can give the fraudster what they want.
If the objective is to steal money, then the victim is someone who has the authority to make payments. If the objective is to infiltrate a network to steal information, the victim is someone with system privileges.
Some spear phishers target new or low-level employees who may be unaware of the risks or at least more easily persuaded. Others will target executive-level employees only (so-called “whaling” attacks).
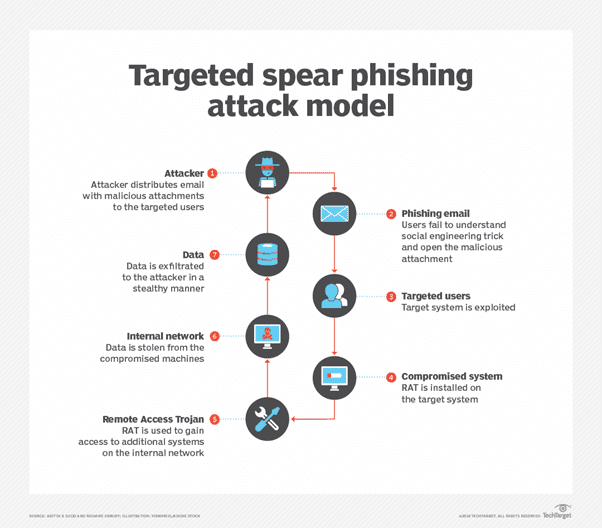
Fraudsters then visit social media platforms and collect information about the victim. They may also browse other sources of publicly available information which, collectively, comprise open-source intelligence (OSINT).
These sources include:
In more sophisticated attacks, criminals use machine learning to analyse public data. Others will break into company email accounts to observe the victim and collect even more information.
Step four is the culmination of the first three steps.
Essentially, the spear phisher crafts a message with details the victim believes only a trusted source would know.
Messages incorporate the information learned thus far plus other cues that lend authenticity to the scam, such as:
Social engineering tactics are also used to pressure the victim. These are particularly effective in spear phishing attacks since fraudsters often impersonate a superior and take advantage of a subordinate’s tendency to respect authority.
Other common tactics include:
Sarah Smith is a Senior Financial Analyst at AlphaTech Corporation, while Michael Thompson is the CFO.
Sarah and Michael have been working on a confidential merger between AlphaTech and Beta Innovations codenamed “Project Fusion”.
Last week, the pair discussed financial models and projections in a private meeting.
Sarah receives an email purporting to be from Michael.
From: michael.thompson@alphatechcorp.com
To: sarah.johnson@alphatech-corp.com
Subject: Urgent – revisions to project fusion financial models
Attachments: Project_Fusion_Models_Update.xlsm
Hi Sarah,
Following up on our meeting last Wednesday about Project Fusion, I’ve reviewed your financial projections and made some adjustments concerning the EBITDA margins and the integration costs we discussed.
The board meeting has been moved up to Monday at 9 AM, so we need to finalise these numbers urgently.
Please find the revised financial models attached. Pay special attention to the third worksheet where I’ve highlighted the changes in yellow. Let’s aim to have a brief call later today to go over any questions you might have.
Also, keep this strictly confidential as per our NDA.
Best regards,
Michael Thompson
Chief Financial Officer
AlphaTech Corporation
Here is an analysis of Michael’s email and how certain characteristics conspire to deceive Sarah:
Once installed, the malware grants attackers access to sensitive financial data and other confidential project details.
Based on the above example, we can see that a few simple checks on Sarah’s part could have prevented the successful spear phishing attack.
The subtle discrepancy in email address is easy to overlook, but an obvious giveaway nonetheless. In addition to email verification, Sarah could have phoned Michael to verify the contents of the email itself. For example, that the meeting had been brought forward.
Failing these checks, email security software that detects and blocks phishing emails (or at least scans for malicious links) is also crucial. It would also be important for AlphaTech to disable macros across its Office products to prevent system-wide compromise.
Otherwise, the business could enable multi-factor authentication (MFA) to prevent criminal access and encrypt sensitive data.
Security awareness training is also a worthwhile investment to ensure that employees recognise the warning signs of a spear phishing attack before it has a chance to cause damage.
Summary:
When cell phones first became popular, no one thought they’d become what they are today. For the first few years, it was …
When Mr. Beauchamp watched a video of Elon Musk – the world’s richest man – recommend a certain investment platform to make …
Your company delivered the good or service it promised to a client and now it’s time to collect the funds owed to …
End-to-end B2B payment protection software to mitigate the risk of payment error, fraud and cyber-crime.