Payment Security 101
Learn about payment fraud and how to prevent it
Most organisations will already have an incident response plan in place.
However, this dedicated BEC incident response guide aims to provide the necessary steps following a BEC attack. This guide is intended for executives and business leaders looking to ensure their organisations are ready to act swiftly and effectively minimising the risk of CEO fraud, invoice fraud & data theft.
When cyber-criminals launch a Business Email Compromise (BEC) attack against your organisation, every minute counts!
Even with the best preventive security measures in place, CFOs must face the very real risk that cyber-criminals will find a way to launch a successful BEC attack against your organisation. However, having the right plan in place will enable you to rapidly respond the minute an attack is identified.
In this guide, we explore the three key elements of a holistic BEC incident response plan: PREPARATION, PLANNING and EXECUTION.
With each of these elements in place, you’ll strengthen the odds of recovering your funds following a BEC attack.

Download the Business Email Compromise (BEC) Incident Response Guide today to strengthen the odds of recovering your funds following a BEC attack.
Download GuideMost organisations will already have an incident response plan in place to deal with the aftermath of a cyber-attack. However, BEC attacks differ from other types of cyber-attacks, therefore, should be handled differently.
A dedicated BEC incident response plan differs in two key respects from other types of incident response plans:
Whilst IT or cyber-security specialists typically lead an organisation’s efforts to deal with the fallout of a cyber-attack, managing the repercussions of a BEC attack will require a more collaborative approach, in which finance and accounting executives, particularly the CFO, will need to play a key role.
A BEC incident response plan will recognise the multidimensional nature of a BEC attack, which typically include both technical breaches, as well as exploits against gaps in internal financial
controls.
By following this guide to developing a holistic BEC incident response plan, you’ll ensure your organisation is ready to act swiftly and effectively to mitigate the financial and other consequences of a BEC attack.
When it comes to BEC attacks, some unique features apply that set them apart from other types of cyber-attacks. That’s why organisations should develop a dedicated BEC incident response plan.

According to the Australian Cyber Security Centre (ACSC), all organisations should develop cyber incident response plans. Such plans help an organisation ensure it can respond effectively, can limit the fallout from an attack, and help a business recover following a potentially disastrous security breach.
All incident response plans should be living documents that are regularly tested, preferably each quarter, and reviewed annually to ensure the plan is always fit-for-purpose in accordance with the organisation’s evolving requirements.
According to the ACSC, an effective incident response plan must “align with the organisation’s incident, emergency, crisis and business continuity arrangements, as well as jurisdictional and national cyber and emergency arrangements. It should support personnel to fulfill their roles by outlining their responsibilities and all legal and regulatory obligations.”
Unfortunately, too many organisations still don’t invest the time or resources to develop incident response plans. This leaves them exposed to facing substantially higher financial losses and downtime in the event of a cyber-attack.
According to a study conducted by the Ponemon Institute and sponsored by IBM Security, the vast majority of organisations surveyed (74%) are still reporting that their incident response plans are either ad-hoc, applied inconsistently, or that they have no plans at all.
This lack of incident response planning results in organisations not being able to recover quickly following a cyber-attack and may cause prolonged disruptions to business operations. It also substantially raises the cost of an attack. Organisations with well-developed and tested incident response plans save an average of $1.2 million when it comes to dealing with a cyberattack.
According to MoneySmart, an initiative of the Australian Securities and Investments Commission (ASIC) that aims to help people increase their financial wellbeing, you are likely to get your money back following a mistaken payment if:
The fundamental problem with this advice is that it assumes the mistaken transaction occurred as a result of a genuine error, rather than as a result of any deliberate attempt by cyber-criminals to steal from you.
The reality is that cyber-criminals never leave proceeds of their crimes sitting idly in bank accounts for 10 days, let alone seven months!
The masterminds behind cyber-crimes, such as BEC, are highly sophisticated and operate at lightning speed. Stolen funds are rapidly transferred between multiple accounts, usually across different jurisdictions, in order to make tracking down stolen money almost impossible.
Increasingly, fraudsters also convert funds into cryptocurrencies, making the job of law enforcement even harder.
No organisation that finds itself subjected to a BEC attack can afford to wait 10 days, or longer, and still expect to recover stolen funds. Only with swift action will you stand any chance of being able to stop illegitimate payments and recover your funds.
For organisations that proactively develop a holistic BEC incident response plan, the chances of recovering stolen funds can be significantly higher. With a holistic BEC incident response plan in place, you’ll be ready to instantly respond to a BEC attack.
What is a holistic BEC incident response plan?
Put simply, a holistic BEC incident response plan embraces both substantial preparatory work, as well as clearly defined steps that you need to implement in the event of an attack.
Extensive preparatory work helps incident responders by:
Whilst extensive preparatory work is an essential component of a holistic BEC incident response plan, so too is a detailed implementation strategy. This latter aspect is important, as often your internal IT team may not have complete awareness or visibility over what activities the attackers undertook.
Preparation is key when it comes to developing a holistic BEC incident response plan.
When speed is of the essence, you need rapid access to critical information that can make the difference between losing or recovering your funds. Critical information will help financial institutions and law enforcement agencies track down and potentially recover stolen funds.
That’s why it’s essential for CFOs to liaise closely with their IT teams to ensure any potential data that will be required following a BEC attack is continuously being logged. Of course, to be able to conduct such forensic analysis of logs, you need to ensure you retain logs long enough to stand a reasonable chance of retracing all of the BEC attacker’s steps.
That said, generating and storing logs of everything for a long time can be financially costly, so it is a matter of assessing the risks and finding the right balance.
It is also important to know whether you are gathering evidence with the intention of using it for internal investigations only, or whether there is any chance of it being submitted as evidence in a court of law. For the latter, clearly, the integrity of the evidence collection process and the evidence itself is critical, so take this into account as you plan and conduct the forensic process.
Following are six critical data points that will urgently be needed following a BEC attack:
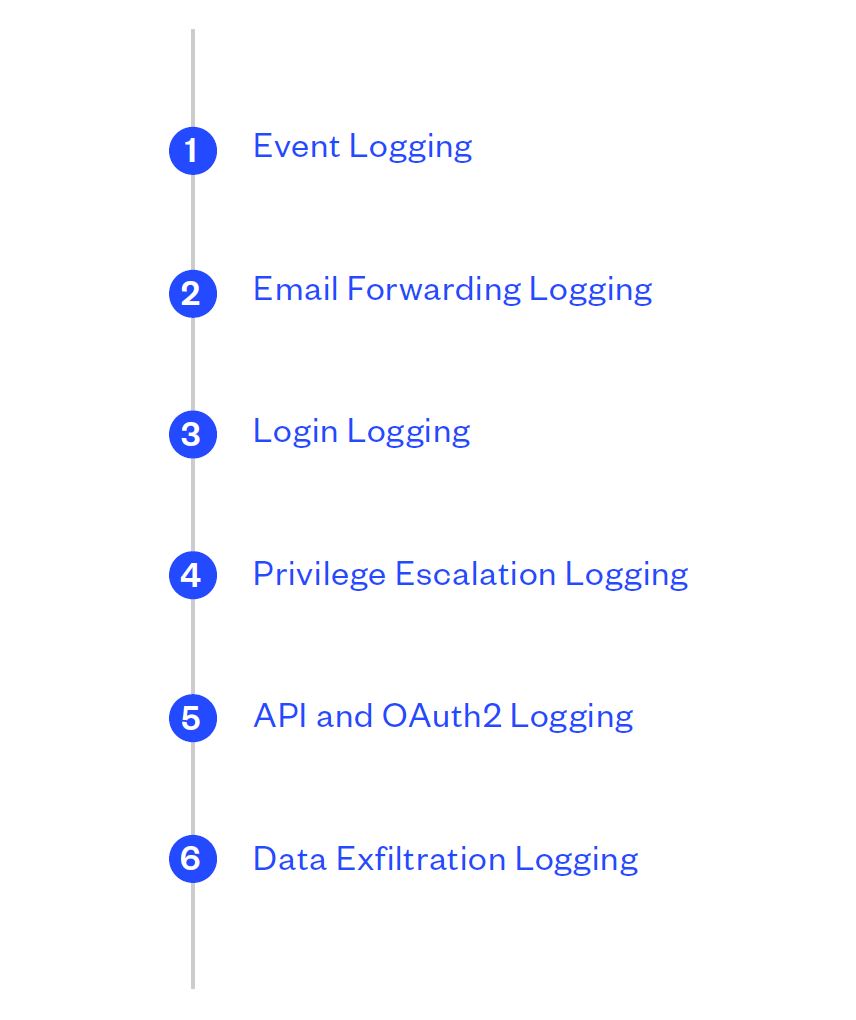
| What is Event Logging? | All your systems should retain logs that record events that occur in your systems, including user access and activity. |
| Why is Event Logging Important? | Logs are critical for establishing a clear understanding of the chain of events that led up to a BEC attack and will provide crucial information about attack methodologies and who may have been responsible. |
| What Information is Available from Event Logging? | The logs referred to below specifically pertain to a Microsoft Office 365 environment and are not exhaustive. Please note that other logs may be applicable to other environments.
1) Unified Audit Log (UAL) This is critical piece of evidence in a BEC investigation. It provides a centralised source for all Office 365 events. The UAL contains at least 76 categories of data, including events from Azure, Exchange, SharePoint, OneDrive, and Skype. 2) Administrator Audit Logs (AAL) This records specific actions that are performed by administrators and users who have been assigned administrative privileges. Given that many BEC attacks involve the attacks granting themselves administrator privileges, AAL can be critical in identifying malicious activity. 3) Message Trace Logs (MTL) MTL provides critical information as it records email flows as they travel through the Microsoft Exchange Server. With MTL, it is possible to determine whether an email was received, rejected, deferred, or delivered. It also shows what actions were taken on the email before it reached its final status, a critical piece of information in any BEC investigation. |
| Discussion Points with IT Team: | Work with your IT function to ensure the logs outlined above will be immediately accessible to third-party incident responders in the event of a BEC attack.
User credentials should be readily available for incident responders so they can launch their investigations without delay. |
| What are Email Forwarding Rules? | Rules configured in email systems that automatically forward emails to third parties. |
| Why are Email Forwarding Rules Important? | Automated email forwarding rules are among the most common methods used by scammers to carry out a BEC attack.
Cyber-criminals gain unauthorised access to an email account and set up blind carbon copy (BCC) rules that forward both inbound and outbound emails to a third party mailbox controlled by the attackers. This enables the attackers to carry out extensive reconnaissance, identify suppliers and access pending invoices. |
| What Information is Available from Email Forwarding Rules? | Identifying and investigating forwarding rules can help revel signs of malicious activity.
Whilst all forwarding rules should be identifiable through system logs, there are likely to be many legitimate forwarding rules set up by various people within the organisation. This can make it challenging to identify which forwarding rules point to potentially malicious activity. When investing forwarding rules, it is important to focus on:
|
| Discussion Points with IT Team: | Disable the ability of users to create forwarding rules to external third party mailboxes without the authorisation of an Accounts Payable manager and an IT manager.
Ensure that an approved list of all forwarding rules is maintained, so in the event of a BEC attack, responders will be able to quickly identify any illegitimate forwarding rules that have been set up by malicious actors. |
| What is Login Activity? | Detailed records of who is attempting to login to your systems. |
| Why is Login Activity Important? | Records of who is logging into your systems are indispensable when attempting to piece together the events that led up to a BEC attack. |
| What Information is Available from Login Activity? | Your IT team should be maintaining detailed logs each time a user attempts to authenticate on any of your organisation’s systems.These logs should record important information such as the IP address and MAC address (associates the login activity with a specific computer or device) used.
An IP address can be used to conduct a geographic lookup of who is logging into your systems. For example, if your company is located in Australia, and you see logs indicating an IP address resolving to Nigeria is being used to log into your systems, this would clearly indicate suspicious activity is taking place that warrants further scrutiny. Logins at suspicious times, such as out of business hours, should also be scrutinised as they may indicate unauthorised access attempts. Importantly, your logs should also record failed login attempts. These may indicate that a malicious actor has been attempting to authenticate on your systems by using compromised login credentials, or is conducting a brute force attack in which they rapidly bombard your systems with many passwords in an attempt to gain unauthorised entry. |
| Discussion Points with IT Team: | All such logs should be recorded in the Unified Audit Log (UAL). Verify with your IT team that such logs are being accurately recorded.
Sophisticated attackers may try to evade detection by disabling the UAL ahead of launching a BEC attack. It’s critical your ITM team has measures in place to alert them to any attempts to disable audit logs, and that they continuously monitor the UAL to ensure it is never disabled. |
| What is Privilege Escalation? | Detailed records of privilege escalation in new or existing user accounts. |
| Why is Privilege Escalation Important? | When launching a BEC attack, cyber-criminals often require access to a range of systems, such as your organisation’s email server. They may seek to obtain access through hijacking an existing user account or may seek to create a new user account.
However, access alone isn’t enough. They will also need high-level privileges that allow them to change system configurations and settings. That’s why privilege escalation is a common feature of many BEC attacks. Attackers will often attempt to change the privileges of existing or newly created user accounts. If they can assign admin or high-level privileges to a compromised account, they can give themselves free rein to implement any changes they wish in the compromised system. |
| What Information is Available from Privilege Escalation Logs? | Your IT team should be maintaining detailed logs each time a new or existing user account’s privileges or permissions change, particularly in email systems.
When it comes to BEC attacks, privilege or permission changes to mailboxes are often an indication of malicious acts. Logs should record events that add or modify permissions in an individual mailbox, as well as folder-level permissions in mailboxes. Additionally, users within a cloud environment may have the ability to send email as another user. Internal policies should detail if and when such activities are authorised. Such activities should also be logged and monitored. |
| Discussion Points with IT Team: | Monitoring user account privileges can be challenging for IT teams. They are often unaware what privileges are required by each user within a given department.
You should maintain a detailed list of all users within the accounting function and the privileges each of those users requires. Critically, you need to ensure this list is always current. Provide the IT team access to this list so they can continuously check it against their system logs to ensure there aren’t any discrepancies. Any discrepancies could indicate malicious activity and must be investigated immediately. |
| What are APIs and OAuth2? | An API, or Application Programming Interface, enables two software systems to communicate with each other. It enables data to be transferred between the two systems using a standard set of protocols.
OAuth2 is a standard that allows one application to gain access to the data of another application using a token, rather than using login credentials. |
| Why are APIs and OAuth2 Important? | BEC attackers exploit vulnerabilities in APIs to access systems, such as mailboxes, in order to carry out their attacks.
Additionally, OAuth2 can be particularly risky. OAuth2 is a widely used standard that allows one application to provide a second application with access to its data, without the need for the second application to have user credentials. In BEC attacks, cyber-criminals often abuse OAuth2 to bypass multi-factor authentication (MFA). |
| What Information is Available from APIs and OAuth2? | By actively monitoring APIs connected to the applications in your environment, as well as usage of OAuth2, it is possible to detect malicious activity that seeks to exploit APIs and OAuth2, indicating a possible BEC attack. |
| Discussion Points with IT Team: | Ensure any potential breaches of APIs or OAuth2 are communicated to the accounting and finance teams so any associated instances of BEC can be rapidly identified. |
| What is Data Exfiltration? | Data exfiltration occurs when your organisation’s data is copied, transferred, or retrieved without authorisation. |
| Why is Data Exfiltration Important? | In many cases, a BEC attack takes place in conjunction with other attack vectors that many see criminals compromising your critical business data. identifying instances of data exfiltration can help identify a potential BEC attack. |
| What Information is Available from Data Exfiltration Logs? | System logs should record events that point to data exfiltration taking place, including:
|
| Discussion Points with IT Team: | Ensure any identified instances of data exfiltration are communicated to the accounting and finance teams so any associated instances of BEC can be rapidly identified. |
Once you ensure all the critical data you will need is being logged, it will be necessary to develop a detailed plan of action that can be rapidly implemented the moment a BEC attack is identified.
When creating your BEC incident response plan, several elements should be included:
When a BEC incident happens, decisions need to be made quickly and under pressure. Your BEC incident response plan should begin by outlining clear objectives and articulating what your priorities will be.
Undoubtedly the primary objective will be to recover any stolen funds. However, there are other objectives you may also need to consider, such as:
Remember, your BEC incident response plan should be a living document.
By conducting quarterly workshops and consultations that bring together leaders from the finance, IT and cybersecurity teams within your organisation, you can embark on a process of continually reviewing your preparedness for a BEC attack, undertaking training simulations, and identifying measures to be adopted that continually strengthen your resilience.
When developing your BEC incident response plan, carefully consider who will form part of the incident response team.
The incident response team will be responsible for:
All members of the BEC incident response team should be actively involved in developing the plans.
This will help ensure clarity exists around each person’s role. Unlike other types of cyber-attacks, a CFO is the ideal executive to lead BEC incident response, due to the financial nature of the crime. However, the IT and cyber-security teams will also play pivotal roles.
Typically, a BEC incident response team will include the following personnel:
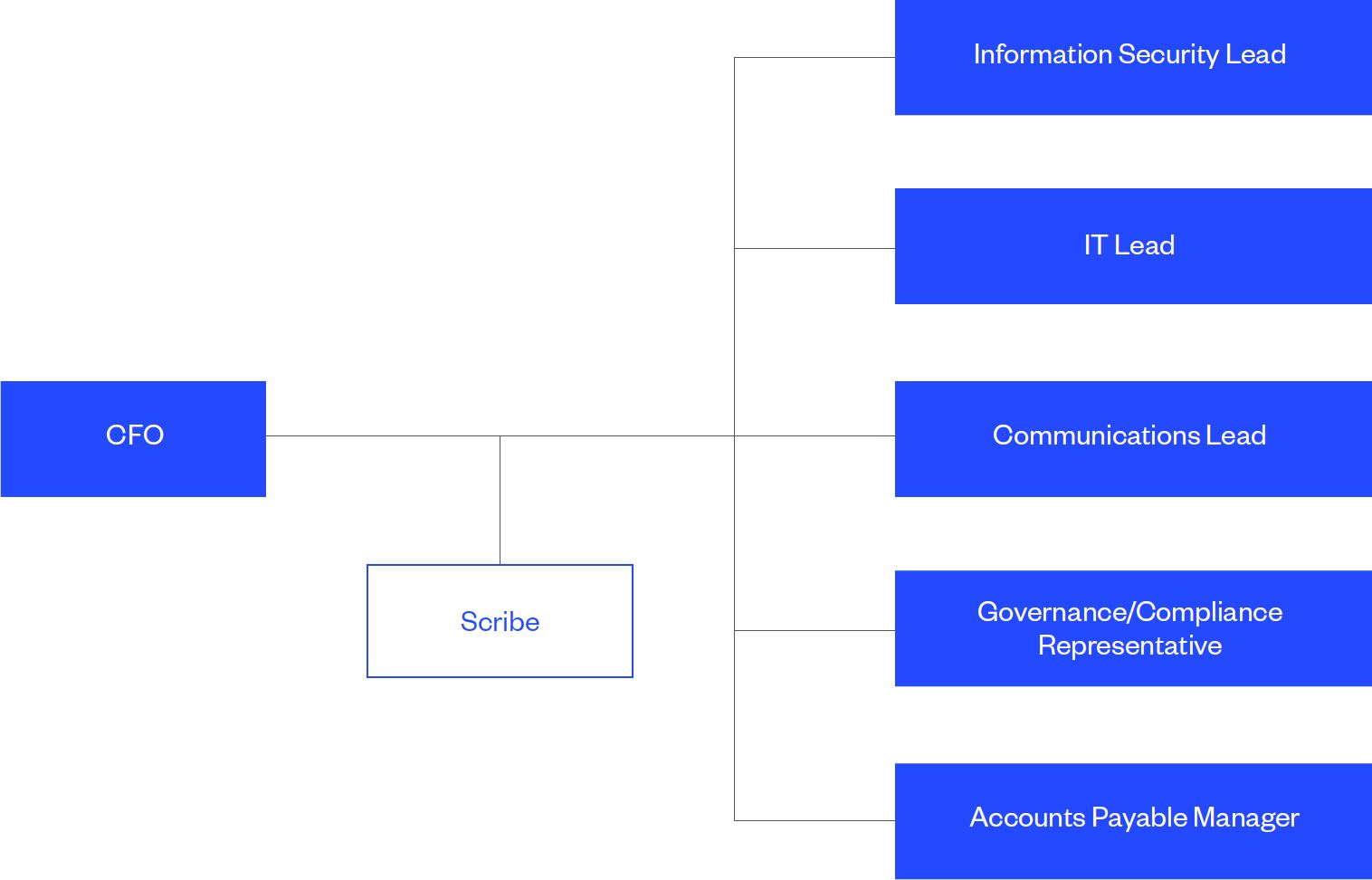
Key decision maker who oversees the incident response and coordinates all activities. Responsible for communicating with financial institutions in an attempt to track, stop and recover funds. Will also oversee communications with law enforcement bodies.
Assists the CFO by documenting all activities, and coordinating the timeline for each stage of the incident response.
Analyses data in logs to determine how the attack likely occurred and any additional information, such as attribution, that can aid in the investigation.
Ensures all relevant logs are made available to investigators, will lock-down systems, such as email clients, as required.
Leads the internal and external communications efforts with relevant stakeholders.
There are a range of issues that may arise from a BEC attack, including data breaches, insurance claims, criminal or civil claims. It’s essential to have legal guidance and participation.
Accounts Payable Manager – Oversees an examination of internal financial controls that may have been breached in the BEC attack to identify gaps that need closing.
Depending on the exact nature of the BEC, additional personnel may need to be included in the incident response team. Whoever is ultimately included, the team needs to have the expertise and experience to assess the nature and impact of a BEC incident, in addition to having the authority to act quickly.
The exact steps and details of an incident response process will vary depending on the specific circumstances. However, the following provides a broad outline of the stages involved that should be incorporated into your processes:
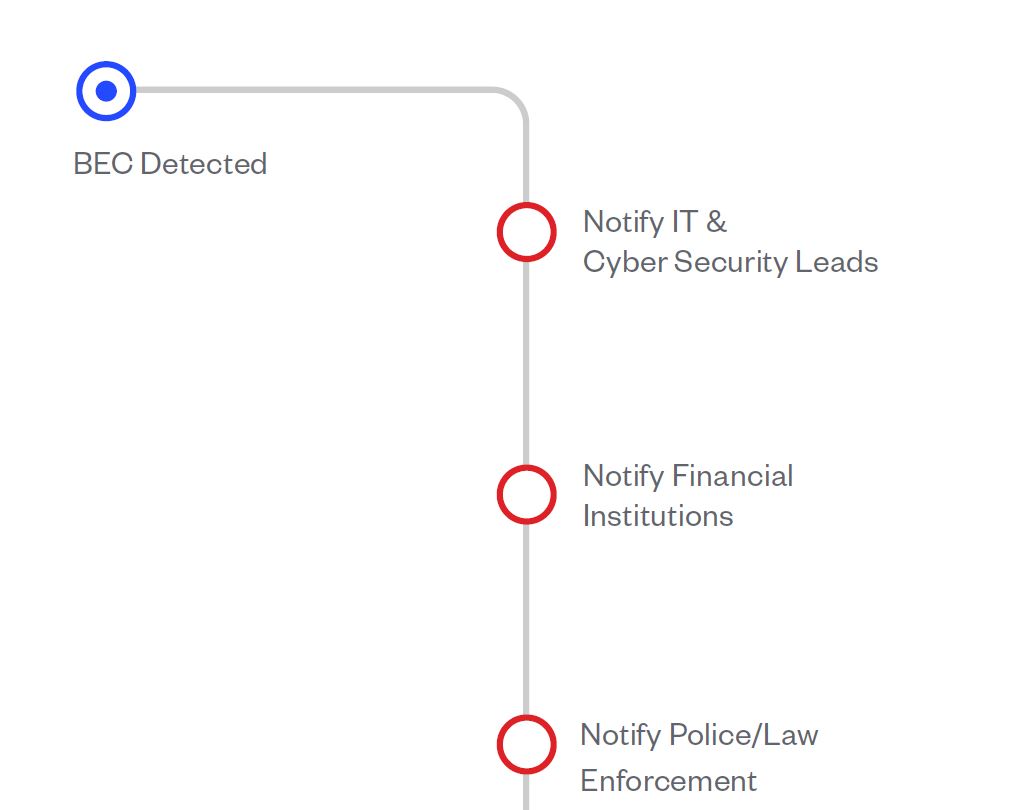
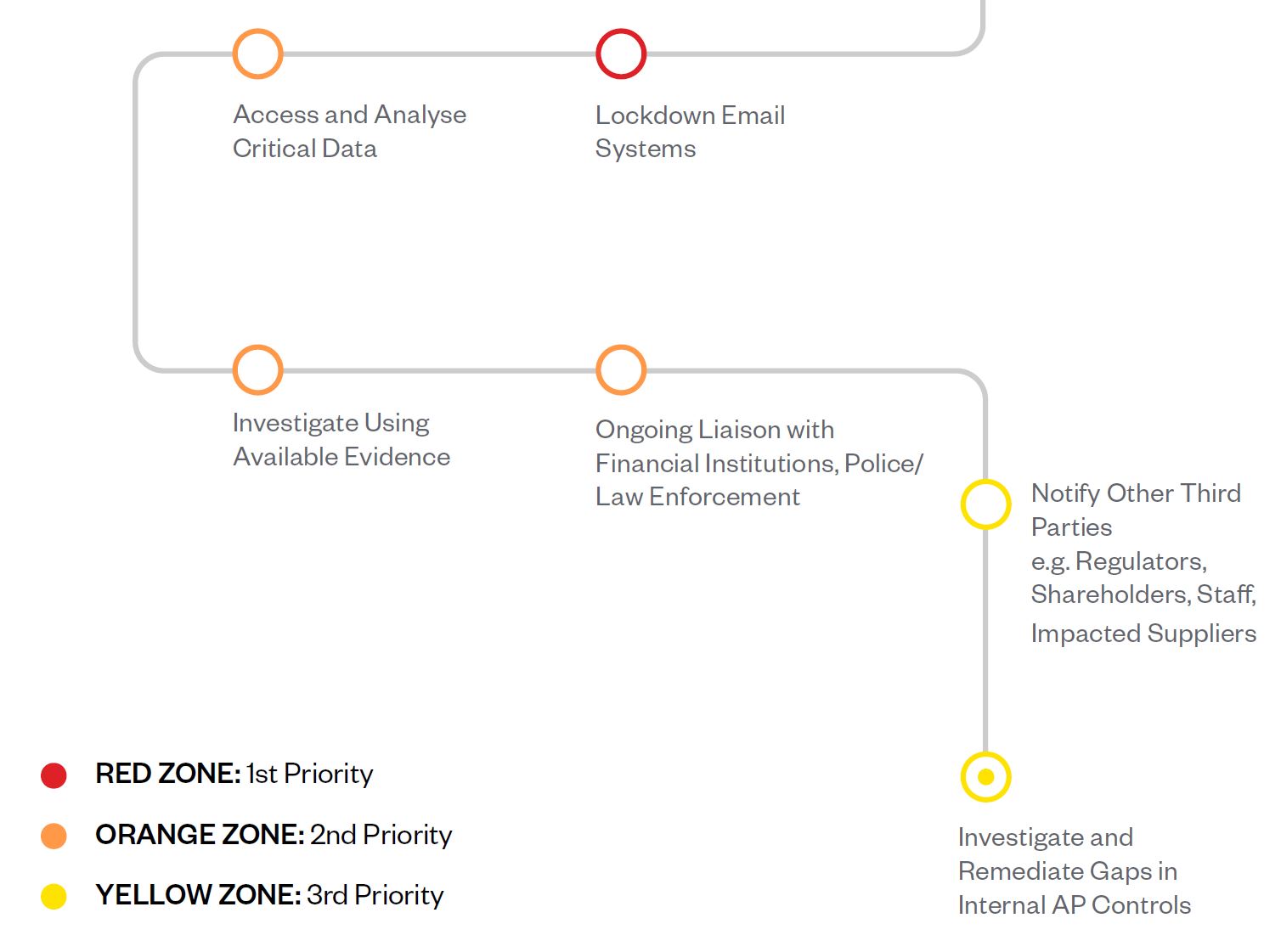
When executing your BEC incident response plan, speed is critical if you stand any chance of recovering stolen funds. The following checklist will help ensure you cover all critical elements:
Following a suspected BEC attack, immediately notify your IT system administrators and cyber security leads. Cyber security leads may be internal or external incident responders.
It is likely that your IT administrators will need to lock down a range of systems and devices for a period of time, whilst their investigations are ongoing, to prevent any further attacks being launched.
This is critical as you should attempt to stop any outgoing payments as quickly as possible. Once your funds are sent to the receiving bank account, the beneficiary will move quickly to:
Any delay reporting the incident to your bank will substantially reduce your chance of recovering any of your funds.
Ensure several nominated senior executives in your organisation have emergency contact details for relevant representatives from your financial institutions (including out-of-hours contact details), so there will always be someone available at any time to stop an unauthorised payment.
Each of the major Australian banks has resources dedicated to assisting customers who have been subjected to scams:
Australian law enforcement agencies, such as the Australian Federal Police (AFP), work with Interpol and law enforcement in other jurisdictions in an attempt to track down funds stolen through BEC attacks.
Despite the fact that funds recovery only occurs in a small number of cases, you should immediately report the attack to your State or Territory police, who can escalate the matter to the AFP or other relevant law enforcement bodies.
You should also report incidents to relevant government agencies:
It will likely be necessary to lock down your organisation’s email systems due to the fact that a BEC attack can be launched in a number of ways:
It will likely take some time for investigators to determine the precise nature of the attack vector. That is why it will be essential to ensure all your organisation’s email systems are fully locked down as a precautionary measure until further information becomes available.
Have a method in place to maintain essential communications with staff, customers, suppliers and other essential stakeholders that is not dependent on your organisation’s email systems, as these may be off-line for some time. Having a database of phone numbers will allow you to call or use instant messaging services to communicate essential information.
Depending on how long it takes responders to get a handle on the situation and restore access to email systems, your organisation may face extended disruption. Keeping communication channels open will build trust with key stakeholders that everything is under control and will contain the risk of reputational damage.

Prior to experiencing a BEC attack you should ensure that your organisation is logging all the critical data that would be needed in an investigation.
Ensure the IT team is extracting all the relevant logs and providing these to investigators so they can rapidly get to work compiling evidence that will assist with efforts to recover stolen funds.
BEC attacks are complex.
Experienced investigators will need to examine all the available logs and data to piece together what exactly occurred.
Your internal IT and cyber security teams may not have the specific skill-sets required to conduct such complex investigations. You may need to engage expert incident responders who will act swiftly to identify the attack vector, attribute responsibility, and attempt to track down the destination of your funds.
By seeking the advice and expertise of external cyber security incident response professionals to conduct a thorough forensic investigation, you will ensure the maximum amount of evidence is extracted as quickly as possible. This will ensure crucial information is supplied to financial institutions and law enforcement, strengthening the chances that the perpetrators can be identified, and your funds recovered.
Ensure all relevant evidence extracted from your data is rapidly supplied to your financial institution, as well as police and law enforcement. This will help them with their inquiries and improve your chances of a successful outcome.

There may be a range of other third parties that should be notified. These may include the suppliers who were the intended recipients of the payments.
Depending on the nature of the BEC incident, and whether other data was breached during the attack, there may be a need to notify regulators, shareholders and impacted customers. There may also be media inquiries that need addressing. When it comes to crisis communications, always attempt to be as transparent as possible as this will help mitigate the risk of reputational damage.
A key feature of a BEC attack is that it not only exploits technical vulnerabilities, it also exploits gaps in internal controls within your Accounts Payable (AP) function.
A thorough audit of your AP controls should be conducted to understand how the attackers manage to circumvent your controls, whether there were any internal threat actors and what steps need to be taken to ensure these gaps are remediated.
BEC attacks are among the most common, and most costly, cyber-attacks. Attackers take advantage of technical vulnerabilities, as well as gaps in internal controls, to steal funds. And attackers are becoming increasingly sophisticated. They rapidly transfer stolen funds to offshore bank accounts or cryptocurrency – making them almost impossible to track down.
Even with the most comprehensive BEC incident response plain in place, the chances of recovering stolen funds remains exceedingly low. That’s why prevention is the only solutions.
With Eftsure sitting on top of your accounting processes, you can ensure you always know outgoing funds are being sent to the intended recipient.
For further information and resources to protect your organisation from BEC attacks, speak with us today.

Book a demo with Eftsure to discover how our solution protects your business from BEC attacks.
Book a demoEnd-to-end B2B payment protection software to mitigate the risk of payment error, fraud and cyber-crime.