Cyber Brief for CFOs: July 2024
All the news, tactics and scams for finance leaders to know about in July 2024.
Each month, the team at Eftsure monitors the headlines for the latest Accounts Payable news. We bring you all the essential learnings in our Security Report so your Accounts Payable team can stay secure.
When it comes to cybersecurity, most businesses focus on protecting themselves from external threats. However, what many fail to recognise is that some of the biggest risks to their security come from within their walls.
A recent example is the 23-year-old IT support contractor who allegedly diverted an estimated total of $90,000 from the Australian National Maritime Museum (ANMM). The IT support worker is suspected of engaging in authorised access to various systems and servers, according to the Australian Federal Police (AFP).
Authorities claim that the man obtained financial information from illegal access to AMMM’s AP system and illegally changed bank account details stored in the museum’s system to his own. They also allege that he used this information to make fraudulent credit card purchases.
According to the AFP, police have seized several electronic items including a laptop, hard drives and a mobile phone. The Sydney man faced Burwood Local Court on Friday 3 March 2023 after he was arrested by the AFP for an alleged cyber-crime enabled fraud against ANMM.
Based on the information currently available about this case, ‘insider threats’ remain a difficult hurdle that many organisations face. Insider threats can appear in many forms and have various motivations behind their attack such as sabotage, fraud, espionage, coercion or reputational damage.
Insiders who have malicious intentions may act on their own, or they might be influenced by external parties who bribe or coerce them against the organisation’s interest for financial gain. Therefore, it’s crucial to your defence on understanding and identifying how to protect yourself from insider threats before it’s too late.
Learn how to protect your business against insider threats.
According to research, the average Australian receives five scam calls, emails or messages a week, adding up to more than 250 attempts a year.
Cyber-criminals are becoming more sophisticated each year as they impersonate all types of organisations, government bodies, corporate entities and more. Aurora Casili knows all too well how quickly scammers can take a person’s life savings.
The 18-year-old lost more than $36,000 in a cyber scam back in December last year.
Cyber-criminals used a technique called ‘spoofing’, where they infiltrate an existing message threat and impersonate a trusted entity. In this case, Casili received a text message that seemed authentic – it appeared to be from NAB.
The message urged the teenager to immediately phone an 1800 number to stop an unknown bank transfer. The unsuspecting teenager complied with the directive in the SMS message.
Following a conversation with someone she believed was a bank representative, the teenager verified her name, date of birth and address over the phone. The individual on the other line told Casili that “she needed to create a new account and transfer her money.”
Chris Sheehan, the executive for group investigations and fraud at NAB and former fraud detective with the Australian Federal Police, said the culprits are “transnational organised crime groups, they’re incredibly well-resourced.”
AP departments are just as vulnerable when it comes to the potential dangers of receiving duplicitious emails, SMS or phone calls. With the advances in technology, there is a growing variety of tools that cyber-criminals can use to impersonate other people and win trust, including deep fakes, phishing emails, AI voice generators and more.
It’s important to ensure a robust verification process before revealing any type of information. This can be achieved by looking up an entity’s legitimate phone number by visiting their official website and verifying first and last names, business details, etc.
In January 2023, the Queensland University of Technology (QUT) revealed thousands of individuals associated with the university potentially had their data compromised by a ransomware attack.
The staff at the university first noticed this attack when the campus printers began to spit out bulk ransomware notes. As a precaution, the university shut down its IT systems to lessen the damage of the cyber-attack.
The following message was printed at QUT.
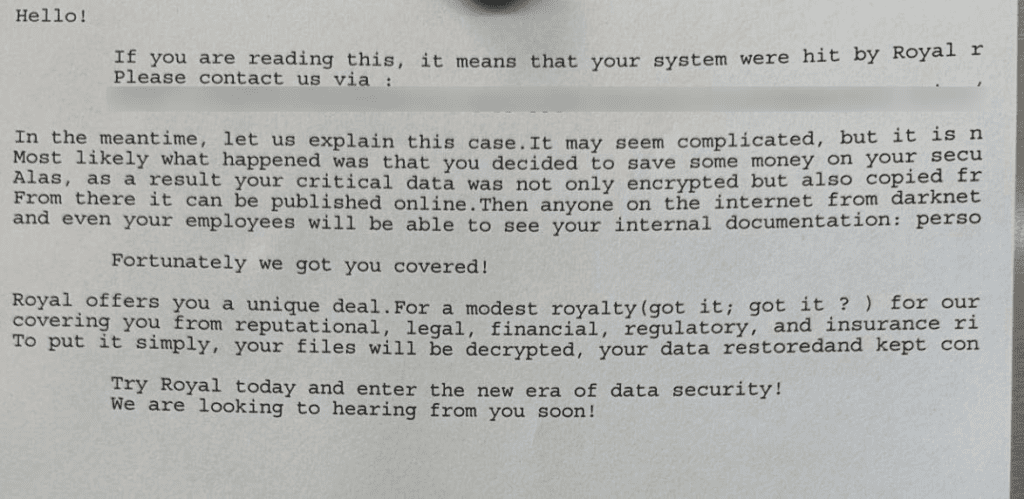
The printed ransomware note says “your critical data was not only encrypted but also copied,” warning it could be published online unless a “modest royalty” is paid.
According to forensic analysis, the cyber-attack was initiated from unauthorised access to several files on an internal storage drive which included sensitive information of employees and students. As a result, a total of 11,405 people were impacted by the Royal ransomware cyber-attack, including 2,492 current university staff, 8,846 former staff and 3,820 people’s tax file numbers.
The response to this came from QUT vice-chancellor Professor Margaret Sheil, who said “We understand how this happened and what the particular vulnerability was.”
She went on to say that the university had addressed the vulnerability. Since the attack, QUT has boosted their cybersecurity measures by “accelerating” its use of more secure forms of storage.
The cost of chaos can be too much to bear when organisations experience a data breach. It can result in higher cyber insurance premiums, disrupted business operations, reputational damage and more. That’s why it’s important to prioritise data security in your AP function.
Incorporating a variety of data security solutions like encryption, authentication methods, data backups, and cloud security can be the key differentiator in mitigating the risk of a cyber-attack. By ensuring your cybersecurity strategy and your financial controls align, you can better contain the threat of cyber-crime.
Learn how to align your cybersecurity strategy with your financial controls today.
On 10 March, California state authorities took control of Silicon Valley Bank and closed it, resulting in one of the largest US bank failures since the 2008 global financial crisis. After a New York bank swiftly followed suit, US federal leaders stepped in to try and thwart a domino effect by promising protection for depositors.
The situation is still evolving, and there’s still discussion around what caused the SVB bank run and what it means for the tech sector and banking system.
What’s less ambiguous is that the situation has resulted in large numbers of companies needing to move to new banks, with AP teams fielding more requests to change banking details than usual. SVB’s customers were primarily tech companies and startups, with some of the biggest names in tech – like Salesforce and Roku – banking with SVB. It’s not surprising that the collapse has kicked off a flurry of changes in banking details.
But this sort of chaos is fertile ground for cyber-criminals, who are liable to try and take advantage of more hectic periods – especially those with any type of uncertainty. Employees may be more likely to make a mistake or skip a step in a financial control process.
Be on high alert – and read more about the SVB collapse and what it means for cyber threats in Australia and New Zealand.
All the news, tactics and scams for finance leaders to know about in July 2024.
All the news, tactics and scams for finance leaders to know about in June 2024.
All the news, tactics and scams for finance leaders to know about in May 2024.
End-to-end B2B payment protection software to mitigate the risk of payment error, fraud and cyber-crime.