Payment Security 101
Learn about payment fraud and how to prevent it
Cyber criminals don’t respect an organisation’s internal boundaries.
Whilst a vulnerability in a network or application may open the door to a data breach, sophisticated cyber-criminals often pivot to defraud a targeted organisation by circumventing internal financial controls.
That’s why the modern CFO & finance leaders need to be involved in every stage of their organisation’s internal cyber security conversations, planning and execution in order to mitigate a cyber attack.
Faced with a rapidly evolving threat landscape, the role of the CFO is also rapidly evolving.
The modern CFO must champion the security of their organisation’s finances against increasingly sophisticated cyber-criminals.Financial crime has shifted from the analogue to the digital world. International criminal syndicates now target any organisation they perceive to be vulnerable by conducting all their activities digitally.
Whilst the entire range of risks remains unknown, there is no doubt it is escalating.
Recent years have seen a fundamental change in the threat landscape. Advances in technology, increased computing power, and the reduced costs of initiating an attack, are all combining to open new opportunities for cyber-criminals.
Now is the time for CFOs to take a step back and objectively assess their organisation’s cyber maturity and likely resilience.
Without a holistic approach to cyber-crime prevention, attackers will eventually discover and exploit an organisation’s weakest link in an attempt to carry out fraud.
Whether they discover a vulnerability in a network, a bug in the application layer, or a gap in internal controls, all it takes is one successful breach and the cyber-criminals will gain access to an organisation’s digital environment.
Once on the inside, the path may be wide open for the criminal to move laterally across the entire network, gaining access to a wide range of systems and data, such as email accounts, ERP software, Vendor Master Files and much more.Once the cyber-criminal gains unauthorised access, they can then pivot towards carrying out a range of other malicious activities, such as comprising sensitive data, executing malware, or engaging in highly effective Social Engineering attacks that are designed to deceive Accounts Payable staff and defraud the organisation.
Given this complexity, and the range of unknowns, there is a greater need than ever to embrace technology that helps facilitate Continuous Controls Monitoring as part of a comprehensive end-to-end approach to security. This will help ensure any security gap isn’t able to be exploited by sophisticated cyber-criminals. After all, cyber-criminals only need to succeed once, whereas organisations need to succeed constantly to ensure their security.
The following Accounts Payable security maturity matrix can help ensure organisational resilience against financially motivated cyber-crime:
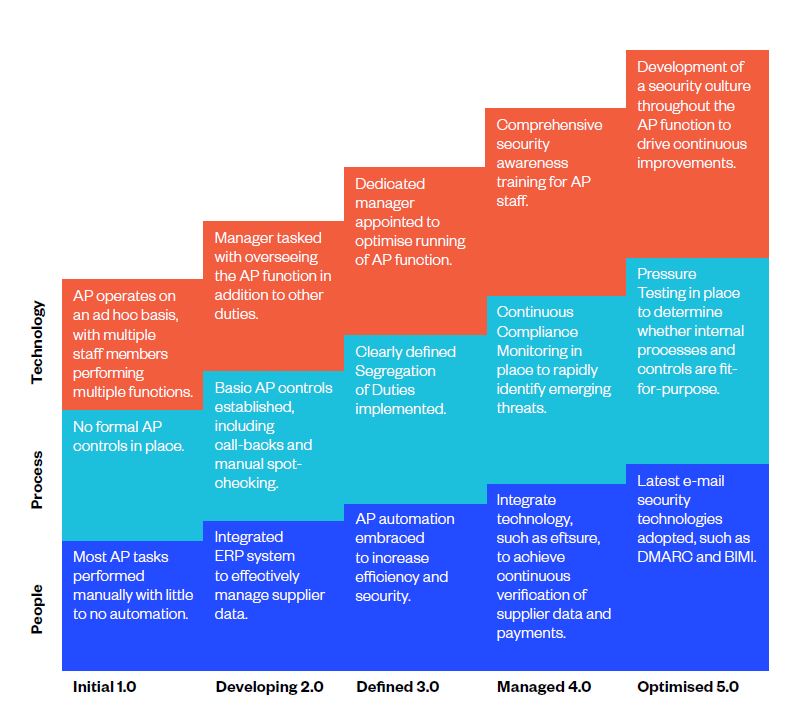
In the new world of financially motivated cyberattacks, every organisation needs to secure both its front door and back door.
Preventing cyber-criminals from gaining unauthorised access to the organisational environment starts with robust security around any potential entry points across the entire environment. However, in the event cyber-criminals do succeed in breaching the perimeter, it is also critical to have systems in place that stop them compromising financial assets. That’s why every CFO needs to ensure their organisation is implementing effective end-to-end security.
Only a strategy that aligns with both the cyber security and IT functions can succeed in providing comprehensive defence-in-depth to safeguard finances in the current threat landscape.
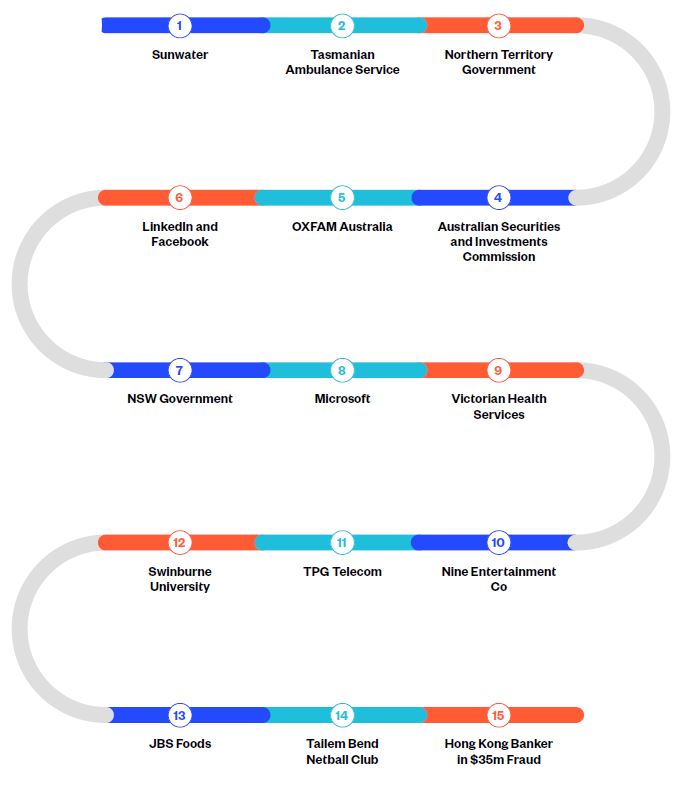
Cyber-criminals took control of several water system servers at Sunwater, Queensland’s largest regional water supplier. The breach went undetected for 9 months, during which they redirected traffic and uploaded malicious content. The attack was able to be executed due to the company running legacy systems containing numerous weaknesses.
Cyber-criminals don’t just target computers. They also breach other devices, such as phones, or in the case of the Tasmanian Ambulance Service, pagers. Unencrypted information was being relayed to paramedics’ pagers using outdated radio technology. Cyber-criminals intercepted the radio data and converted the conversations to text, before posting the information online. Intercepted information included patient health data and personally identifiable information (PII).
The Northern Territory Government’s Department of Corporate and Digital Development was hit by a ransomware attack, impacting it for a period of three weeks. In a reminder of how important supply chain security is, cyber-criminals targeted one of the Department’s suppliers that was responsible for the provision of its corporate software system.
In more bad news for Northern Territorians, the Department of Health publicly released personal and business email addresses from their COVID-19 tracing application in a mass email. This is a reminder that data breaches not only originate from the actions of malicious outsiders. Internal errors can also result in serious breaches.

Sources:
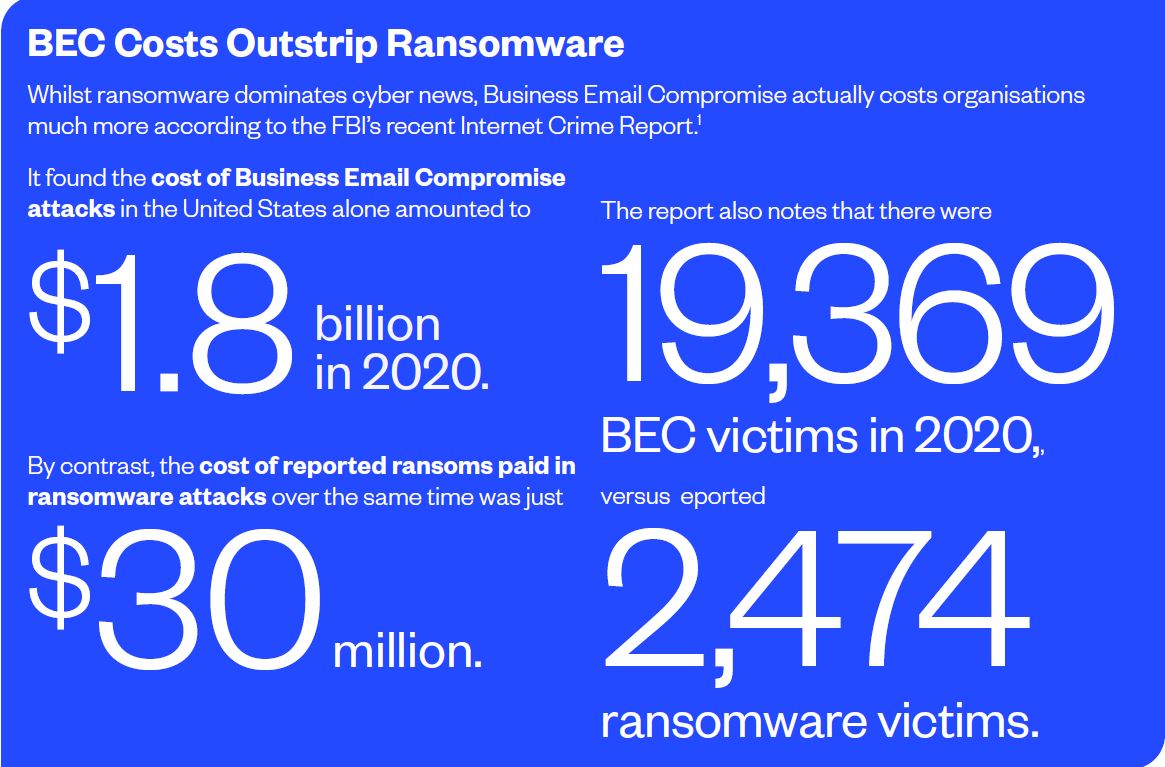
Business Email Compromise (BEC) incidents are rising faster than any other type of cybercrime according to the Annual Cyber Threat Report 2020-2021 by the Australian Cyber Security Centre (ACSC).
The past financial year saw 4,600 BEC incidents reported to the ACSC, with total reported losses exceeding $81.5 million – a 15% jump on the previous year. Not only are incidents of BEC on the rise, but the average amount lost in a successful attack skyrocketed 54% to $50,600. When an attack vector experiences that level of year-on-year increase, the leaders of every organisation need to be paying attention!
So, what exactly is Business Email Compromise?
BEC is a targeted attack that aims to deceive Accounts Payable staff into transferring funds to a bank account controlled by the attacker. Cyber-criminals are known to use a variety of deception tactics. The two most common tactics are:
Cyber-criminals typically send fake emails impersonating a senior executive within a target organisation. They often use the name of a trusted individual, such as the CEO or CFO, in an email ‘From’ header. More advanced attacks also spoof the domain of the organisation being targeted. This involves inserting the target organisation’s domain name in the ‘From’ header of the fake email.
Cyber-criminals gain unauthorised access to the email account of a senior executive in the target organisation, typically the CEO or CFO. This is usually achieved via Social Engineering or a Phishing attack (see below). The attackers then send fake payment instructions to Accounts Payable staff via email using the authentic mailbox.
Because an authentic mailbox is used in these BEC attacks, it is extremely difficult for any Accounts Payable staff member to know that the message is not genuine.
The contents of email messages sent as part of a BEC attack typically:
The ACSC is warning that the criminal syndicates behind BEC are more sophisticated than ever, having developed enhanced, streamlined methods for targeting Australian organisations. BEC attacks are particularly effective because they take advantage of busy Accounts Payable staff who believe they are diligently executing instructions from their superiors.
Because these emails do not necessarily contain any malicious links or attachments, they are often able to circumvent technical security controls, such as email filtering tools or firewalls. Unless Accounts Payable staff are highly trained in identifying such emails, there is a strong likelihood that a BEC attack will succeed.
BEC is now a top concern for Australian banks, with a recent study finding that 86% of bank respondents perceive it to be the greatest risk to their businesses over the next two years. According to the study, over 50% of respondents realise something needs to be done to reduce this growing threat, in particular investing in technology solutions that mitigate the risk.
Whilst an organisation may have robust security controls in place to prevent financially motivated cyber-crime, other organisations within the supply chain may not be as secure. Supply chain vulnerabilities can impose significant risks on their commercial partners.
In an interconnected digital economy, each of us is only as strong as the weakest link.
Like BEC, Vendor Email Compromise (VEC) sees cyber-criminals impersonating individuals in order to deceive Accounts Payable staff into transferring funds to a bank account controlled by the attacker.
However, rather than impersonating a target organisation’s senior executives, VEC involves compromising an organisation’s suppliers.
Once a supplier’s email systems are compromised, cyber-criminals can request that their customers update payment details in ERP systems. They can also issue fake invoices to all that supplier’s customers. From a cyber-criminal’s point of view, one successful VEC attack can result in a much greater financial windfall. After all, compromising one supplier allows the cyber-criminals to target all their commercial partners.
Because VEC attacks do not rely on malicious links or attachments, they often evade technical security controls, such as email filtering tools or firewalls. Supply chain security is now a major concern for many organisations, as they have minimal control over the security posture of their suppliers.
In a recent analysis of the key cyber security questions executives need to be asking themselves, PwC partner, Mike Cerny, highlighted the importance of having a thorough understanding of supply chain security.
In the case of VEC, an organisation may end up being defrauded even though it was a third-party supplier that was compromised. VEC attacks often succeed because there is a strong degree of trust that exists between an organisation and its suppliers. When cyber-criminals impersonate a trusted representative of a supplier organisation, many Accounts Payable staff diligently comply with requests to update banking information or process invoices, unaware that they are being deceived.
Instances of personal identity theft are widely known, however entire organisations can be compromised in a similar way.
Business identity theft is where a cyber-criminal seeks to impersonate a business, or specific individuals within a business, typically a senior executive, in order to obtain financial gain. Business identity theft is a prelude to a number of financially motivated crimes. As with BEC, cyber-criminals may seek to impersonate an organisation’s CEO or CFO in order to deceive Accounts Payable staff into transferring funds to a bank account controlled by the attacker.
In addition, cyber-criminals may engage in business identity theft in order to obtain loans or credit cards in the name of the business.
According to the Australian Institute of Criminology (AIC), instances of serious identity theft are increasing at an alarming rate. The AIC defines an instance of identity theft as “serious” if it meets one of the following criteria:
According to this definition, the AIC estimates that serious identity theft cost Australia over $423 million in the financial year 2018-2019.
The Australian Federal Police (AFP) is at the forefront of national attempts to prevent the spread of this type of crime. It recognises that identity crime need not involve impersonating individuals, but rather may involve impersonating corporate entities. It defines identity crime as a generic term to describe activities in which a perpetrator uses either a fabricated identity, a manipulated identity or a stolen/assumed identity to facilitate a crime.
Whether an organisation’s identity is being fabricated, manipulated or stolen, the effects can be devastating. These can include significant financial losses and impacted cash-flow, damaged reputation and long-term business disruption.
Cyber-criminals not only resort to emails when launching their attacks. Mobile phones are increasingly used, as they allow attackers to circumvent email security controls.
A recent report from Scamwatch highlights this trend. Between 1 January 2021 and 19 September 2021, over half of all scams reported to Scamwatch involved the use of phone calls. In dollar terms, Australians lost over $63.6 million due to phone call scams during this period. Not only are volumes of scams involving mobile phones increasing, but the tactics are also more sophisticated than before, encompassing both calls and SMS messages. Cyber-criminals are calling or texting people and claiming to be from a well-known business or government agency.
Their goal is to deceive people into revealing personal information, including financial or banking details. Both individuals and organisations are actively being targeted.
Of particular concern is the use of new technologies in carrying out these scams, such as the deployment of ‘Flubot’ malware. In a ‘Flubot’ attack, the cyber criminals send text messages to unsuspecting victims’ phones with a link to a fake voicemail message. Clicking the link directs the victim to a fake webpage where they are prompted to install malware in order to access the message.
This grants the attacker access to a range of data stored on the device, including credit card details, personal information, text messages and emails. Given so many Accounts Payable staff now work from home, with many using personal mobile devices for work, such phone scams represent a real threat to many organisations.
Cyber-crime can have a range of short-term and long- term financial consequences on organisations that find themselves targeted. Understanding the potential financial risks of cyber-crime is essential for all CFOs, so appropriate risk mitigation strategies can be adopted.
The The costs of cyber-crime extend far beyond any amount that has been defrauded.
A cyber-crime can cause widespread financial and reputational damage. It can result in disrupted business operations, and often leads to copycat crimes against the organisation. While the full range of costs of cyber-crime can be difficult to quantify, one thing is clear: the costs of remediation are far higher than the costs of prevention.
To help quantify the true cost of fraud, a recent study found that for every US$1 of fraud in Australia, the targeted organisation ends up paying US$3.51 in total costs. This is an increased from US$3.40 in the previous year, demonstrating that the real cost of cyber-crime is rising strongly.
When it comes to evaluating the true cost of digital fraud, a combination of factors is driving up actual costs. Chief among these factors is the cost associated with identity verification. Verifying the identity of a third party in a digital transaction is increasingly challenging, with the increasing availability of technologies that are being used by cyber-criminals for nefarious ends.
Digital identity verification is impacted by:
CFOs should work with risk and cyber security specialists to implement a multi-layered approach to mitigating cyber-crime and digital fraud. This should include the use of tools that can authenticate both digital and physical criteria, as well as identity and transaction risk.
Organisations targeted in cyber-crime may face increased premiums when it comes time to purchase or renew cyber incident insurance policies.
Recent research indicates that in some cases insurers impose a 200% premium increase on organisations that have been targeted in cyber-crime. Some of the factors that may influence cyber insurance costs for organisations that have been targeted in cyber-crime include:
CFOs should prioritise working with risk and cyber security specialists to develop incident response plans that can be implemented as soon as a cyber-crime event is detected, as well as a comprehensive strategy for strengthening the organisation’s cyber maturity that prioritises the protection of financial assets.
Cyber-criminals that engage in business identity theft, regularly use stolen identities to apply for loans or credit cards. This could negatively impact an organisation’s credit rating, making it harder to obtain financing in the future.
A drop in an organisation’s credit rating could also increase the costs of raising debt, with targeted organisations facing higher interest rates for borrowed capital, both at the time of raising debt and when renegotiating existing debt. Lenders may perceive an organisation as a high-risk borrower if it has been targeted by cyber-crime, with questions raised about the level of internal governance and controls.
Cyber-crime incidents can also result in serious questions being asked by investors and shareholders, who may develop doubts around the capacity of senior management to assess and mitigate risk. This can negatively impact a company’s valuation.
In 2016, Verizon was looking to acquire Yahoo. However, before the deal was complete, Yahoo suffered a series of cyber-breaches, negatively impacting its stock price by 3%. Verizon subsequently declared the breaches to be a “material adverse event” under the Stock Purchase Agreement, and the purchase price was reduced by 7.25%, or US$350 million.
An organisation’s credit rating, valuation and ability to raise funding can all be impacted by cyber- crime. These matters are central to the fiduciary responsibilities of CFOs, who need to work with cyber security specialists to ensure measures are in place to mitigate the risk that cyber-crime may pose to the organisation and limit negative financial consequences.
One of the most significant costs that must be factored into cyber-crime is business disruption. This is also among the hardest to quantify in advance, as each case of cyber-crime varies in impact and intensity.
Costs may include the need to rebuild operational capabilities in certain circumstances, such as repairs to computer systems and equipment. This can result in resources needing to be diverted from one business unit to another.
Business disruption could also impede the organisation from supplying goods or services to its customers, resulting in less revenue and potentially less market share as customers turn to the organisation’s competitors. CFOs need to work with risk and cyber security specialists to develop comprehensive disaster recovery and business continuity plans that can be activated in the immediate aftermath of any disruption.
Well-developed disaster recovery and business continuity plans can lessen the impact of cyber-crime, allowing the organisation to resume business-as-usual operations as rapidly as possible.
When an organisation is impacted by cyber-crime, it can have long-lasting effects on the brand and its reputation.
Customers, suppliers and other commercial partners may perceive that the organisation is insecure, leading to questions around whether governance, risk management and information security controls can be fully trusted.
This may result in lost revenue and market share.
Recently, a number of Tesla customers were reportedly sent invoices via e-mail for the purchase of electric vehicles. In one instance, a Perth resident was e-mailed an invoice to pay $74,647.62. However, the e-mail had been intercepted by cyber-criminals, who altered bank account details in the invoice.
The funds were paid into a bank account controlled by the criminals, with no possibility of recovery. The customer involved criticised Tesla for lax controls around invoices. Such incidents can result in significant harm to brand reputation, which is a critical asset for any organisation. CFOs need to adopt a risk minimisation approach to protect their organisation’s brand and financial interests.
With so many risks associated with cyber-crime, CFOs should work with cyber security specialists to identify potential risks and develop strategies that help protect their organisation.
When an organisation is impacted by cyber-crime, the resulting losses can have a detrimental impact on cash-flow.
Not only are there the direct losses from digital fraud, but the organisation may also experience lost revenues due to downtime. This can make keeping up with business-as-usual expenses, such as payroll and other bills, a significant challenge.
Organisations may even be forced to default on credit card or loan repayments, further impacting their credit rating. This can force the organisation to rapidly cut costs, further constraining its ability to recover from the incident.
Armed with an awareness of the evolving cyber threat landscape, and the potential financial impacts of cyber-crime, CFOs need to develop mechanisms for breaking down the internal silos that exist within many organisations.
Without developing close coordination and cooperation between the finance, cyber security and IT functions, the organisation will not be able to develop the truly comprehensive approach required to mitigate the risks posed by cyber-criminals. The following can guide CFOs when it comes to ensuring their organisation is on the right path towards enhancing their cyber maturity:
Governance standards around cyber security are increasingly on the radar of the Australian government and various regulatory bodies.
In July 2021, the Australian Department of Home Affairs opened consultations on options for regulatory reforms to strengthen the cyber security of Australia’s digital economy. Among the matters being considered are whether more needs to be done to hold boards accountable in cases where an organisation has blatantly failed to adopt appropriate cyber risk mitigation strategies.
Whilst the existing suite of cyber security laws, regulations and compliance standards do impose a range of obligations on directors and officeholders, these are applied to specific sectors and industries, rather than being universally applicable to all organisations. Of course, all directors and officeholders have an obligation to act in good faith in the best interests of their company in accordance with the Corporations Act.
It is now widely accepted that cyber security risks are an increasingly important set of risks that all organisations need to oversee and manage.
Despite this, there is no explicit requirement that boards mitigate cyber security risks. However, this may be about to change. Among the measures under consideration by the government are new cyber security governance standards, particularly for larger businesses.
These standards may either be voluntary or mandatory. Either way, they could be considered by a court when determining whether failures relating to the oversight of cyber risk constituted a breach of director or officeholder responsibilities under the Corporations Act.
Furthermore, ASIC, as the primary corporate regulator, has the power to launch legal proceedings against company directors and officeholders for a breach of duties. The consequences could include pecuniary penalties and compensation orders. Directors and officeholders may even be disqualified from managing a corporation in the future.
The implications for CFOs are clear.
With financially motivated cyber-attacks, such as Business Email Compromise, increasing exponentially, CFOs need to be able to demonstrate that appropriate cyber security strategies are adopted that help mitigate potential financial risks.
By advocating for board-level security oversight, which brings together senior executives responsible for an organisation’s finances, governance/risk and information security, it will be possible to demonstrate that effective measures are in place that reduce the likelihood of cyber-crime.
By establishing a sub-committee of the board with all relevant executives, it will be possible to ensure organisation-wide comprehensive staff training programs, appropriate policies and internal controls, and technologies are adopted that help prevent the losses that often result from cyber-crime.
Few concepts in cyber security architecture have garnered as much as attention in recent times as zero-trust.
A zero-trust paradigm is focused on resource and asset protection. It is built on the premise of “trust no-one and no-thing.” In other words, trust is never implicitly granted. Those accessing your systems must be continuously evaluated to ensure they are authorised to do so.
Just because an individual is authorised to access a system, you should not assume they should automatically be authorised to access everything within that system. Prior to zero-trust, security was built around the principle of “trust but verify.”
This approach automatically trusted users and endpoints that successfully authenticated when entering the organisation’s network perimeter. However, it did nothing to protect an organisation from insider threats, or cases where an attacker had managed to acquire login and password credentials.
By contrast, zero-trust embraces an end-to-end approach that encompasses identity, credentials, access management, operations, endpoints, hosting environments, and the interconnecting infrastructure to determine whether a user or an action is authorised.
The key to remember about zero-trust is that it is not simply about putting up barriers. Zero- trust should not create friction that undermines productivity or limits peoples’ ability to work.
CFOs should consider how a zero-trust approach can be applied to protecting payments and finances from fraud. In many respects, the basic ideas underpinning zero-trust have been used in fraud prevention for a long time, but they have been executed on an ad hoc basis.
For example, it could be argued that Segregation of Duties aligns with the principles of zero-trust.
Even though an individual within the Accounts Payable team has access to the Vendor Master File, it doesn’t automatically mean they have the ability to enter or change data within the Vendor Master File. When it comes to applying comprehensive zero- trust to fraud prevention, CFOs need to work with cyber security and IT specialists to develop strategies to assess risk based on a combination of factors.
These factors could include the individual, the device being used, as well as the nature of any actions being performed. Bringing all this data together will help determine which users and which actions should be authorised, and which should not.

CFOs have a responsibility to safeguard their organisation’s financial assets by implementing effective risk management strategies. This includes the possibility that malicious insiders may engage in cyber-crime or fraudulent activities against the organisation.
Adopting appropriate internal controls that restrict the level of information individuals have access to helps mitigate the potential risk of a malicious insider. These include limiting the information individuals have access to, otherwise known as the Need-to- Know principle, as well as Segregation of Duties.
Both controls require close coordination between the finance and IT functions. Identity and Access Management (IDAM) systems need to be in place that ensure the right individuals have access to the data they need, whilst not having access to additional information sources.
These systems need to align with all relevant f inance policies and should always be updated to reflect staffing changes, including role changes and departures. Get IDAM settings wrong, and people will have access to too much information, exposing the organisation to greater risk of cyber-crime and fraud.
The risks associated with the wrong IT settings were recently highlighted in a report titled “Local Government General Computer Controls” by the Western Australian Auditor-General. The report highlighted the fact that staff at one local council were using shared generic login credentials to access a server that hosted files storing sensitive financial data.
With unrestricted access to the files, any staff member could potentially redirect payments for council rates, infringements, license and application fees to another bank account. Simply changing a file that was hosted on the shared server was all that was required to commit fraud.
With access to the server not restricted in any way, and no activity on the server being monitored or logged, it would have been almost impossible to identify the responsible party in the event of any fraudulent activity.
CFOs need to work closely with cyber security and IT specialists to ensure appropriate IDAM systems are put in place, access to files and data is closely monitored and controls are in place that prevent staff taking unauthorised actions on computer systems.
Penetration Testing is a cyber security activity that allows an organisation to identify with precision what vulnerabilities exist in its network, application layer and physical environment. It is a widely practiced activity as it arms the organisation with essential knowledge about how cyber-criminals may carry out an attack, and what measures need implementing to strengthen cyber resilience.
Penetration Testing can even be used to determine the extent to which Accounts Payable staff are vulnerable to Phishing and whether additional resources should be directed to raising staff awareness of the threat. Similarly, Pressure Testing is also an activity that can protect the organisation from cyber-crime.
It is an internal process that is designed to determine whether the organisation has appropriate policies, processes and procedures that are fit-for-purpose. Through Pressure Testing, an organisation should be able to determine where any weaknesses exist, paving the way for a strengthening of the organisation’s capacity to withstand a particular challenge.
The recent release of AS8001:2021, the standard issued by Standards Australia for fraud and corruption control, makes clear that organisations should embrace Pressure Testing as a way to assess the operational effectiveness of their internal controls.
Pressure Testing may involve either internal or external individuals or teams initiating a series of test transactions to assess whether the organisation’s internal controls are effective in preventing cyber- crime and fraud. CFOs should work with risk and cyber security specialists to undertake periodic Pressure Testing of their organisation’s policies, processes and procedures.
This is one of the most effective ways to determine the extent to which the organisation’s financial assets are safeguarded from cyber-crime.
Email remains the indispensable mode of communication for Accounts Payable teams. However, email may also be susceptible to a range of vulnerabilities.
Given the risk compromised emails can pose to an organisation’s financial assets, CFOs should be aware that there are a range of new email security features beginning to be embraced by many organisations. Domain Message Authentication Reporting (DMARC) is an email authentication system.
By implementing DMARC, an organisation can ensure that only genuine emails it sends out are delivered to third parties. Unauthenticated emails that are sent out by cyber-criminals who purport to be from the organisation, will not be delivered to the third party.
As organisations begin implementing DMARC, this should result in a steady decline in email-based cyber-crime such as Phishing and Business Email Compromise, although it may not assist in cases where a cyber-criminal gains access to an executive’s genuine mailbox and uses it for nefarious purposes. In more encouraging developments, a new method is being introduced that enables the use of brand- controlled logos within email clients, such as Outlook.
Known as Brand Indicators for Message Identification, or BIMI, this new approach ensures only genuine emails that have been DMARC authenticated will display the sender’s corporate logo. BIMI has the potential to offer a quick and easy way for Accounts Payable staff to identify a fake email, as the purported sender’s logo will not be displayed.
CFOs should liaise with cyber security and IT specialists to ensure their organisation adopts the latest email security technologies.
Continuous Controls Monitoring is an indispensable element in securing any organisation from cyber-crime. With the nature of the risks constantly adapting, vigilance is essential.
This is particularly the case for Accounts Payable functions, where there are often extended periods of time between a supplier being onboarded into a Vendor Master File until a payment is processed.
During this window, any number of events can occur that result in incorrect payments. Cyber-criminals may succeed in manipulating supplier banking details following breaches of the ERP/Vendor Master File.
Malicious insiders may compromise data in the text-based ABA files that are used to upload payments to online banking portals. Alternatively, cyber-criminals may succeed in deceiving Accounts Payable teams into erroneously changing supplier banking details.
Due to all these reasons, it is critical that robust controls are implemented and continuously monitored to identify any potential cyber-crime.
CFOs should cooperate with cyber security and IT specialists to ensure that technologies are introduced that help facilitate Continuous Controls Monitoring. This will provide the essential oversight that is needed to protect the organisation’s financial assets from cyber-crime.
The time has come for every CFO to begin focusing on their organisation’s cyber security.
The risk to an organisation’s financial viability from cyber-crime has never been greater. And it’s a risk that is only increasing. Whilst every function within an organisation should be concerned about cyber security, the finance function must be particularly vigilant as it is often the primary target of cyber-criminals.
CFOs have a critical role to play in ensuring an organisation-wide, fully integrated strategy is embraced that limits the exposure to attacks, whilst mitigating the risk of financial losses in the event that an attack succeeds.
Given that even the most well-resourced organisations find it impossible to stop all cyber- attacks from occurring, having systems in place to prevent financial losses is essential. Through close cooperation with cyber security and IT specialists, the CFO is uniquely placed to strengthen the controls around financial assets to ensure a cyber attack doesn’t also result in devastating financial losses.
The most effective way a CFO can strengthen the controls around their organisation’s finances is through the adoption of technologies that facilitate continuous oversight and compliance monitoring.
Eftsure is a unique automated platform that enables Accounts Payable staff to process large volumes of invoices efficiently and effectively, whilst reducing the risk of cyber-crime to financial assets. Sitting on top of an organisation’s accounting processes, the proprietary eftsure database, which comprises over 2 million Australian entities, allows Accounts Payable teams to verify supplier banking data in real-time, immediately prior to processing an EFT payment.
This ensures that Continuous Compliance Monitoring is in place, so any emerging threat to the organisation’s finances can be rapidly identified and contained.
When a supplier’s banking data match the records in the eftsure database, the payment will display a GREEN thumb signal, indicating it is safe to proceed with the payment. A mismatch results in a RED thumb signal, whilst an unverified supplier results in an ORANGE thumb signal, indicating further investigation is required prior to proceeding with the payment.
For any CFO seeking to strengthen the security around financial assets, this is an effective approach that provides a high degree of assurance. Attempted cyber-crime that seeks to manipulate supplier banking data, either in invoices, ERP systems, or via any other method, will be flagged and the outgoing payments can be halted.
Contact Eftsure today to take the first step towards securing your organisation’s financial assets from cyber-crime.

Book a demonstration with Eftsure and take your first step towards securing your organisation's financial assets.
Book a demoEnd-to-end B2B payment protection software to mitigate the risk of payment error, fraud and cyber-crime.