A guide to cyberattack protection
On average, a cyberattack occurs every 10 minutes in Australia with small to medium enterprises (SMEs), education, healthcare and government the most …
Update on 23 July 2024: This article has been updated to include new details about the massive scale of the MediSecure breach and what we currently know about the stolen data.
When Australia’s national cybersecurity coordinator announced that a large-scale ransomware data breach was impacting a commercial healthcare organisation, it would be a while longer before media reports began indicating that the organisation was e-prescriptions provider MediSecure.
Since then, MediSecure has confirmed the attack and revealed that over 12.9 customers were impacted, making it one of the largest data breaches in Australia’s history. Here’s everything we know about the cyber attack and what’s happened to the data.
MediSecure was one of Australia’s two major e-scripts providers, facilitating electronic prescribing and dispensing across the nation. Given the organisation’s size, it’s not surprising that it held a massive trove of data.
In May 2024, MediSecure confirmed that it had identified a cyber security incident that put private personal and health information at risk. At the time, the scale of the attack was not publicly known, and both Australia’s national cybersecurity coordinator and a MediSecure spokesperson stated that investigations were underway.
In a statement on the MediSecure website, the business says the incident likely stemmed from a third-party vendor and that it had taken immediate mitigating steps.
“While we continue to gather more information, early indicators suggest the incident originated from one of our third-party vendors. MediSecure takes its legal and ethical obligations seriously and appreciate this information will be of concern.”
Third-party vendors are a common attack vector for cybercriminals. In our discussion with Lance Rubin, founder/owner of financial modelling consultancy Model Citizn, Lance explained that his business was targeted because they worked closely with large organisations and government entities.
“It’s not you as a business, it’s actually how you’re connected to the broader, industry finance ecosystem… I’d say that probably anyone who’s in financial services and a small business is probably at a greater risk because we’re so trusted, because we’ve got access to our clients information. And therefore it’s not necessarily our own data [that hackers want], it’s our client’s data.”
Australia has seen a growing number of high-profile ransomware attacks, including those against Medibank, Latitude Financial and HWL Ebsworth.
Ransomware attacks involve a malicious actor infiltrating a system to lock or encrypt your files, assets and data, then demanding a ransom for the release of those files. A now-ubiquitous tactic involves demanding a ransom not to leak or sell highly sensitive information or intellectual property. For organisations that store data relating to legal, financial or health-related areas, the dissemination of that information can be especially devastating – unfortunately, this makes them a common target for ransomware attacks.
In particular, healthcare organisations are popular targets for cyber attacks. A similar attack rocked the entire US health system, when a cyber attack immobilised one of the country’s largest health payment and prescription processors, Change Healthcare. The attack resulted in critical delays impacting pharmacies, clinics, hospitals and insurers.
MediSecure immediately stated it was cooperating with the Australian Digital Health Agency and national cyber security authorities to manage the incident’s impacts. Previously, it held a government contract for providing PBS e-script services until late 2022, when exclusivity was granted to another firm, eRx.
The Australian Medical Association president pushed for urgent briefings, calling for a thorough, transparent investigation backed by clear public communication to maintain trust in electronic health systems.
In June 2024, MediSecure went into voluntary administration after it failed to secure a financial bailout from the government. By July, the organisation revealed that the incident had impacted nearly 13 million customers.
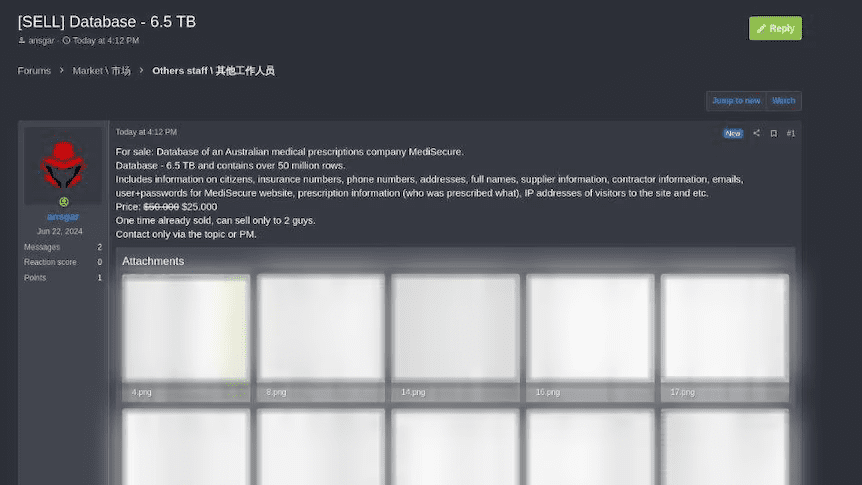
Given the nature of the dark web, it’s notoriously difficult to confirm what happens to stolen data. But there’s reason to believe that the MediSecure data is already in the hands of a threat actor.
In reporting by the ABC, cybersecurity analysts say the data was almost certainly already sold on the dark web for $50,000 (likely USD). That same ABC reporting further reveals that a post on a separate forum is again spruiking the data, this time at half price.
Ransomware attacks have devastating consequences for the organisations and individuals impacted, but there are knock-on effects even for those who aren’t directly affected. A joint police operation claims to have linked 11,000 cybercrime incidents to the Medibank data breach, illustrating how stolen data can act as kindling for other cyber attacks.
Many accounts payable (AP) and finance professionals are on the frontlines of business scams and cybercrime. With stolen data facilitating even more scams, consider two important areas necessary for protecting yourself:

On average, a cyberattack occurs every 10 minutes in Australia with small to medium enterprises (SMEs), education, healthcare and government the most …
Crowdstrike outage aftermath: Government warnings, scam attempts, and essential steps to safeguard your business from cybercriminals.
See how a Rite Aid data breach compromised 2.2M customers’ data through an elaborate impersonation attack. Learn about the risks and preventive measures.
End-to-end B2B payment protection software to mitigate the risk of payment error, fraud and cyber-crime.