Cyber Brief for CFOs: July 2024
All the news, tactics and scams for finance leaders to know about in July 2024.
Each month, the team at Eftsure monitors the headlines for the latest Accounts Payable security news. We bring you all the essential learnings, so your Accounts Payable team can stay secure.
“For every ransomware demand that I know gets paid, I can tell you 20 victims of a BEC (Business Email Compromise) scam, accounting for just as much if not more.”
That’s the assessment of Reece Corbett-Wilkins, from Sydney law firm Clyde & Co.
Despite the focus on ransomware, hackers are increasingly turning to invoice manipulation to scam Australians out of their hard-earned money. And the overheated Australian property sector presents cyber criminals with rich picking.
Read more: Ransomware vs BEC: Which are the biggest threats?
With limited protections around high-value property transactions, every individual within the real estate transaction chain is being targeted, including buyers, agents, mortgage brokers and conveyancers.
Clyde & Co’s cyber response team experienced a 150 per cent increase in reported BEC incidents from 2018 to 2021. The sums lost are often huge, with one client recently losing over $750,000.
Anyone involved in property transactions must take seriously the threat posed by BEC. Neglecting the threat is putting you at serious risk of massive financial losses.
Cyber criminals are becoming more sophisticated. Meanwhile, their attacks are more destructive and costly than ever.
As a result, the private and public sectors need to collaborate and share intelligence that helps attribute attacks to the various global crime rings according to Doug Witschi, Assistant Director for Cybercrime Threat Response and Operations at Interpol.
“We’re not going to be able to arrest ourselves out of this problem,” he said. “Cybercrime is such a global threat, unlike transnational organised crime. If a gang was funnelling drugs and drug money between two countries, the local cops could work together to take down the crime ring using legal tools like mutual assistance treaties and bilateral agreements between the two,” he explained.
However, according to Witschi, cybercrimes like Business Email Compromise (BEC) are global in nature, making it almost impossible for any national police force to put a stop to such practices.
“I can’t see a single nation being able to get on top of it when you think that 13 per cent of countries don’t have law – let alone policy – around cybercrime. It just means that any international legal framework doesn’t exist in those countries,” Witschi added.
The message is clear – when it comes to safeguarding your organisation from cybercrime, don’t assume police or other law enforcement agencies will be able to fully protect you. Every organisation must have preventive measures in place that mitigate the risk of falling victim to cybercriminals before they strike.
Learn how CrimeStoppers is working with Interpol to try and stop global crime syndicates.
The cybercrime squad within the Victorian police force has coopeted unnamed Virtual Private Network (VPN) operators in the fight against Business Email Compromise (BED) bandits.
Whilst VPNs allow for the secure transfer of data between computers, and have become widely used by remote working staff during the pandemic, VPNs may also be used for nefarious means. Cyber criminals routinely use VPNs to operate stealthily online, by masking their computer’s IP address, making it almost impossible for law enforcement to track and trace their activities.
According to Detective Sergeant Tas Gagatsakis from Victoria police, several US and Australian VPN providers handed over their customers’ IP addresses to police when asked for them.
There are VPN providers that “are obliged to assist law enforcement when given the correct paperwork or search warrant,” according to Detective Sergeant Gagatsakis.
Victorians reportedly lost $31,904,837 to BEC attacks in 2021. The vast bulk of these funds were never recovered.
Rather than relying mostly on tracing money transfers to identify BEC criminal syndicates, Victoria police are now turning to techniques that will potentially expose the criminals’ IP addresses. Of particular note, Victoria police are currently investigating a Nigerian national who is part of a cyber-crime syndicate that stole $7 million through BEC attacks against both small and large Australian businesses between 2019 and 2021.
Whilst IP address tracing is likely to help law enforcement authorities in their efforts to disrupt BEC attacks, it is unlikely to permanently stop the phenomenon. VPN providers located in other jurisdictions, far from the oversight of Australian authorities, are unlikely to compromise their customer data. For VPN providers, such a move could risk alienating many of their customers, proving detrimental to their business.
Furthermore, cyber-criminals could use multiple VPN providers, making it almost impossible to track them down.
Prevention remains the best strategy when it comes to protecting your organisation from BEC attacks.
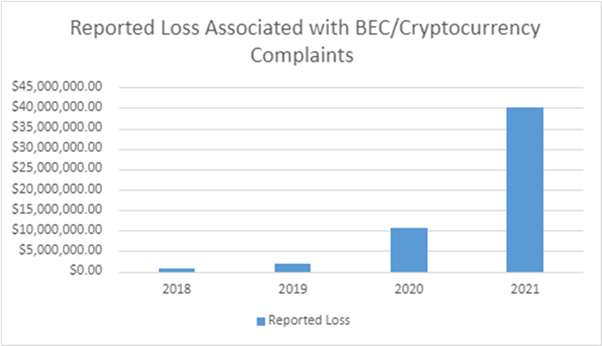
Business Email Compromise (BEC) attack vectors continue to evolve. According to the FBI, the latest technique being used by cyber-criminals involves the use of cryptocurrencies.
The FBI has received an increased number of BEC complaints involving the use of cryptocurrency, such as Bitcoin. There appear to be two types of BEC attacks incorporating cryptocurrencies:
In both situations, the victim is unaware that their funds are being sent to be converted to cryptocurrency.
In the first type of attack, the BEC scammer deceives a victim into transferring funds to a cryptocurrency wallet directly controlled by the scammer.
In the second type of attack, BEC scammers use stolen identity documents belonging to innocent third parties to set-up cryptocurrency wallets. The victim is then deceived into sending funds to the cryptocurrency wallet that’s in the name of the individual whose identity was compromised. However, in reality, the scammer has full control over this cryptocurrency wallet.
The FBI recommends the following strategies for preventing BEC attacks:

All the news, tactics and scams for finance leaders to know about in July 2024.
All the news, tactics and scams for finance leaders to know about in June 2024.
All the news, tactics and scams for finance leaders to know about in May 2024.
End-to-end B2B payment protection software to mitigate the risk of payment error, fraud and cyber-crime.