Payment Security 101
Learn about payment fraud and how to prevent it

Easily onboard, verify and manage vendor information securely. Operate using a single source of truth and ensure vendor data is up-to-date and contains accurate EIN information.
Pay with confidence and context. Empower teams with payment information at every step of the procure-to-pay process by incorporating fraud alerts.
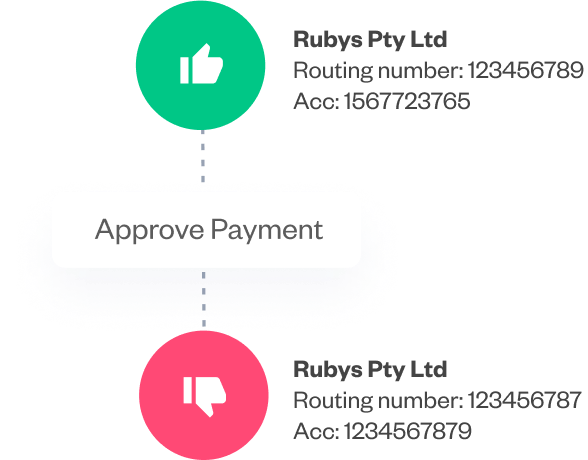

Get organized with a digital interface that allows teams to work autonomously and securely. User roles and permissions enforce standardized protocols and processes.





End-to-end B2B payment protection software to mitigate the risk of payment error, fraud and cyber-crime.